WEDNESDAY: 7 December 2022. Afternoon Paper. Time Allowed: 3 hours.
Answer ALL questions. This paper has two sections. SECTION I has twenty (20) short response questions of forty (40) marks. SECTION II has three (3) practical questions of sixty (60) marks. Marks allocated to each question are shown at the end of the question.
Required Resources:
- A computer
- Internet connection
- Simulator such as packet tracer or GNS3
SECTION I
1. Protocols such as Open Shortest Path First (OSPF) and Enhanced interior Gateway Routing Protocol (EIGRP) which ensures routers exchange route information, compare path information and select best path to destination network are known as? (2 marks)
2. What is the name of the service discovery protocol that translates human readable domain name to machine readable IP address? (2 marks)
3. Fiber optic cable transmits data as pulses of light through flexible, optically pure fibers of glass or plastic. Which of the type of fiber-optic cable can help data travel approximately 500 meters? (2 marks)
4. A network administrator is designing a new network infrastructure with the objective of ensuring end user mobility when connecting to the network. Which type of connection would be recommended? (2 marks)
5. Transport Layer is the fourth layer from the top in Open Systems Interconnection (OSI) Model which provides communication services to the application processes that was running on different hosts. Which transport layer protocol ensures reliable same-order delivery? (2 marks)
6. The Internet Assigned Numbers Authority (IANA) is the standards organization responsible for assigning various addressing standards using 16-bit port number that identifies the source and destination. Which port group includes port numbers for FTP, HTTP, and TFTP applications? (2 marks)
7. What is the name given to a protocol that allows users to share whole files with other users?
8. What is the name of the protocol that allows a client to download data from or upload data to the server? (2 marks)
9. The prefix-length is a decimal value indicating the number of leftmost contiguous bits of the address. What is the prefix length notation for the subnet mask 255.255.255.248?
10. Which component of an IP address identifies computer on a network? (2 marks)
11. The compressed representation of IPv6 address 2001: CAFE:0DB8:0001:0000:0000:0000:0010 is? (2 marks)
12. Which command utility can be used to test internal configuration of an IPv6 host? (2 marks)
13. Mr. Lidibwe a newly hired technician is troubleshooting a network where it is suspected that a defective node in the network path is causing packets to be dropped. The technician has only IP address of the end point device with no other details provided. Which command utility can be used by the technician to identify the faulty node? (2 marks)
14. The message sent by a host to check the uniqueness of an IPv6 address before using that address is referred to as? (2 marks)
15. Give the name of a TCP mechanism used to enhance performance by allowing a device to continuously send a steady stream of segments as long as the device is also receiving necessary acknowledgements. (2 marks)
16. What is the name given to small, wireless transmitters that use low-energy Bluetooth technology to send signals to
other smart devices nearby? (2 marks)
17. Communications technology refers to all equipment and programs that are used to process and communicate information. Which type of telecommunication technology is used to provide Internet access to vessels at sea? (2 marks)
18. Which Intermediary device connects multiple IP packets and determines the best path to send packets?
19. A feature that allows routers to select the best path to use whenever there are two or more different routes to the same destination from two different routing protocols is referred to as _____________________. (2 marks)
20. The following IP Address 192.168.10.63/27 can be categorised as which kind of address? (2 marks)
SECTION II
21. Variable Length Subnet Mask (VLSM) was designed to avoid wasting IP addresses. With VLSM, a network is subnetted and then re-subnetted. This process can be repeated multiple times to create subnets of various sizes based on the number of hosts required in each subnet. Effective use of VLSM requires address planning.
Use the diagram below to answer the questions that follow:
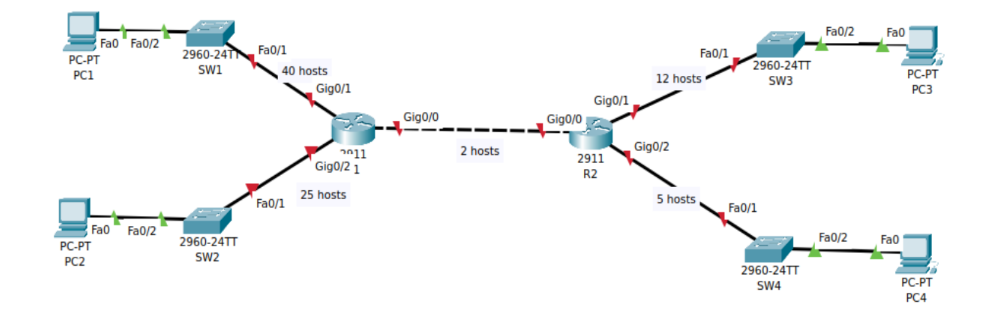
IP ADDRESS: 192.168.10.0/241.
1. How many IP addresses are required in the largest subnet? (2 marks)
What subnet mask can support that many host addresses? (2 marks)
2. How many IP addresses are required in the second largest subnet? (2 marks)
What subnet mask can support that many host addresses? (2 marks)
3. How many IP addresses are required in the third largest subnet? (2 marks)
What subnet mask can support that many host addresses? (2 marks)
4. How many IP addresses are required in the fourth largest subnet? (2 marks)
What subnet mask can support that many host addresses? (2 marks)
5. How many IP addresses are required in the fifth largest subnet? (2 marks)
What subnet mask can support that many host addresses? (2 marks)
(Total: 20 marks)
22. Using a network simulator and the details you obtained in Question 21, answer the following questions:
Use the first network address of the largest subnet to configure your network based on the topology and capture a screenshot showing IP details configuration. (4 marks)
Use the first network address of the second largest subnet to configure your network based on the topology and capture a screenshot showing IP details configuration. (4 marks)
Use the first network address of the third largest subnet to configure your network based on the topology and capture a screenshot showing IP details configuration. (4 marks)
Use the first network address of the fourth largest subnet to configure your network based on the topology and capture a screenshot showing IP details configuration. (4marks)
Use the first network address of the fifth largest subnet to configure your network based on the topology and capture a screenshot showing IP details configuration. (4 marks)
Upload Question 22 document.
(Total: 20 marks)
23. Create a word processing document named “Question 23” and use the word processor document to save your answers to questions 1 to 4.
Using appropriate simulator, setup the topology as shown below
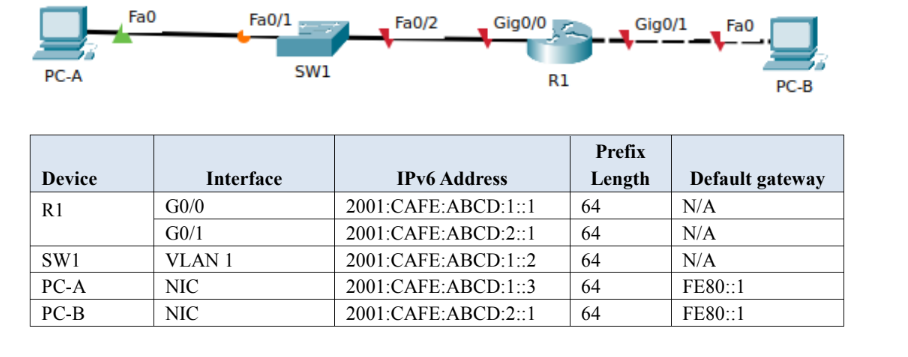
Required:
1. Configure the global unicast IPv6 address provided in the table to the intermediary and end user devices.
Capture a screenshot of the output. (8 marks)
2. Using a command utility, test connectivity between PC-A and PC-B. (2marks)
3. Using PC-B, access R1 remotely using Secure Shell (SSH). (6 marks)
4. Disable unused switch ports on SW1. (4 marks)
Upload Question 23 document.
(Total: 20 marks)
