INSTRUCTIONS: ANSWER ALL QUESTIONS.
QUESTION 1
In the list below, what would be the first logical step when troubleshooting a computer?
A. Call the vendor
B. Define the circumstances of the problem
C. Check the computer CMOS
D. Define what applications are being used
QUESTION 2
Mr. Tekino while working on a client’s computer saw the message “invalid media device” after installing a new hard drive. Advise him on the best action to take.
A. Add operating system to the hard drive
B. Compress the hard drive
C. Partition the hard drive
D. Format the hard drive
QUESTION 3.
is suitable to clean different components of a computer without leaving scratches or debris.
A. Soft cloth
B. Cable ties
C. Compressed air
D. Parts organizer
QUESTION 4
Which one of the following access controls entails users assigning access rights based on rules user specify?
A. Mandatory access control (MAC)
B. Attribute Based Access Control (ABAC)
C. Role based Access Control (RBAC)
D. Discretionary access control (DAC)
QUESTION 5
Application integration is crucial in modern business. There are a number of application integration challenges that businesses face today. Which of the following is NOT a valid way to overcome these challenges?
A. Have easy-to-use, web-based, graphical integration design that business application owners can drive on their own. B. Self-documenting interface with the ability to track changes and restore old versions if something goes wrong.
C. Opt for multiple, smaller integrations over large, more complex ones.
D. Training all users to become application integration experts so that they have the required skills.
QUESTION 6
Is define as any electrical or electronic equipment that’s been discarded.
A. Faulty hardware
B. E-waste
C. E-devices
D. Waste electronic equipment
QUESTION 7
Which one of the following converts the formats of electricity pulled from power sources to match the format required by
the machines they power?
A. ROM BIOS Chip
B. CMOS RAM
C. Hard Drive
D. Power Supply
QUESTION 8
Which of the following best describes the characteristics of the information that is required by top level executives in an
organization?
A. It is sourced from internal sources and external sources, highly detailed and relevant to the long term
B. It is sourced from external sources, highly summarized and relevant to the short term C. It is sourced from internal and external sources, highly summarized and relevant to the entire organization
D. It is sourced from internal sources, highly summarized and relevant to the long term
QUESTION 9
Security of computer hardware and its components is also necessary for the overall protection of data. Which one of the following does NOT entail security of computer hardware and its component?
A. Internal components
B. Locks and cables
C. Software
D. Cloud Computing.
QUESTION 10
The device that tests computer ports basic functionality is known as .
A. digital multimeter
B. Loopback adapter
C. toner probe
D. port tester
QUESTION 11
During computer assembly, the processor is mounted onto the ZIF socket. After processor mounting, the will be attached on top of the processor.
A. processor fan
B. processor bay
C. heat fan
D. heat sink
QUESTION 12
Which one of the following refers to the process of replacing a product with a newer version of the same product?
A. Updating
B. Downgrading
C. Upgrading
D. Improving
QUESTION 13
A point of contact within the organization meant to cater for internal technical ICT queries is referred to as .
A. ICT guide center
B. ICT Help desk
C. ICT queries point
D. ICT data center
QUESTION 14
____________________is used to describe devices that work with a computer system as soon as they are connected.
A. Standard hotub
B. Plug-and-Play
C. Universal Serial Bus
D. High Definition Multimedia Interface
QUESTION 15
Which one of the following is a cyber-attack that entails stealing smaller amounts of money from thousands of bank accounts at once?
A. Data diddling
B. Salami attack
C. Password attack
D. Cross-site Scripting
QUESTION 16
Which of the following is NOT components of an information system?
A. Software
B. Information
C. Procedure
D. Arithmetic and logic unit
QUESTION 17
What is the name given to a hardware device or software program used to convert data from one format into another?
A. Register
B. Encoder
C. Decoder
D. Flip flop
QUESTION 18
____________describes security measures that are designed to deny unauthorized access to facilities, equipment and
resources and to protect personnel and property from damage or harm.
A. Network Security
B. Physical Security
C. Information Security
D. Database Security
QUESTION 19
Acronym RSI stands for?
A. Repetitive Standing Injury
B. Real Strain Injury
C. Repeated Standing Injury
D. Repetitive Strain Injury
QUESTION 20
What is the name of the physical docking point where an external device can be connected to the computer?
A. Websocket
B. Outlet
C. Port D. Socket
QUESTION 21
Identify the type of cybercrime attack initiated by cybercriminals to masquerade as a senior player at an organization and directly target senior or other important individuals of a given organization.
A. Whaling
B. Smishing
C. Spearphishing
D. Vishing
QUESTION 22 What is defined as an integrated set of components for collecting, storing, and processing data and for providing information, knowledge, and digital products?
A. Information system
B. Computerized system
C. Data system
D. Digital system
QUESTION 23
The type of system integration that supports the expanding of the functionality of the existing system is referred to as.
A. Business-to-business integration
B. Enterprise application integration
C. Third-party system integration
D. Legacy system integration
QUESTION 24
Which one of the following refers to the abuse of computers and high-technology appliances to undermine computing resources of an adversary?
A. Information Warfare
B. Electronic Warfare
C. Cyber Crime
D. Cyber Reconnaissance
QUESTION 25
Which of the following is not a power on- self- test (POST) output message?
A. Audio codes
B. onscreen text messages
C. hexadecimal numeric codes
D. Video codes
QUESTION 26
Disaster response is the reaction and activity involved in helping people who have involved in some kind of catastrophe. Among the following, identify number one priority of disaster response.
A. Resuming transaction processing.
B. Protecting the hardware.
C. Protecting the software.
D. Personnel safety
QUESTION 27
___________________ refers to group of computers are linked together so they can work as a single entity.
A. Clusters
B. Sectors
C. Vectors
D. Heads
QUESTION 28
An attempt by attacker to take control of computer system, programs and network communication can be referred to as .
A. Threats
B. Session hijacking
C. Cyber hijacking
D. Cyber Attacks
QUESTION 29
Glorix Ltd sells both new and refurbished computers and their accessories. Mrs Clarax bought a new computer recently and has lodged a complaint with respect to how her computer has become very slow. Which of the following is NOT a possible cause for this?
A. Too many startup programs.
B. Processor has become obsolete.
C. Many applications installed that are rarely used
D. Low hard disk storage capacity.
QUESTION 30
A decision that is made by a proprietor of an organization using the experience acquired and documented rules can be
referred to as?
A. Structured decision
B. Semi structured decision
C. Unstructured decision
D. Complete decision
QUESTION 31
_________relates to copying of physical or virtual files or databases to a secondary site for preservation in case of equipment failure or another catastrophe.
A. Encryption
B. Locking
C. Decryption
D. Backup
QUESTION 32
is a cross-functional organizational backbone that integrates and automates many internal business processes and information systems within the sales and distribution, production, logistics, accounting, and human resources.
A. Enterprise Resource Planning
B. Payroll Management System
C. Customer Relationship Management
D. Human Resource Management
QUESTION 33
Who among the following are referred to as nefarious hackers and their sole objective is for financial gains?
A. Amateur hackers
B. Black hat hackers
C. White hat hackers
D. Gray hat hackers
QUESTION 34
Ergonomics is an applied science concerned with designing and arranging things people use so that the people and things interact most efficiently and safely. Identify from the following what a user should NOT do.
A. Sit in the same position for more than an hour
B. Use a speaker phone or headset, as needed.
C. Keep your computer monitor at or below eye level.
D. Use wrist and palm supports to rest in between tasks.
QUESTION 35
What tool is used to safely and quickly remove integrated circuits (ICs) from their sockets? A. All-purpose cleaner
B. Chip extractor
C. Compressed air
D. Wet cloth
QUESTION 36
Which of the following is an advantage of system integration?
A. Realization of all organization’s goals
B. Increased productivity
C. Better security of data
D. Development of viable systems
QUESTION 37
___________is the term that relates to weakness exhibited in system or network.
A. Threat
B. Attack
C. Vulnerability
D. Exploit
QUESTION 38
One of the hard drive types is the , which is a storage drive composed entirely of memory chips, rather than rotating magnetic disks in traditional hard disks.
A. serial ATA (SATA)
B. small computer system interface (SCSI)
C. solid state drives (SSD)
D. parallel ATA (PATA)
QUESTION 39
Which of the following statements listed below is NOT a good reason why web services must be tested?
A. The web services and client applications communicate over the world wide web, and there are abundant chances of a security breach.
B. The host maintains and improves the services periodically therefore development team must put in regular effort to improve the product, which involves changes through different builds and releases.
C. Webservices are small applications that have specific functionality therefore, a test is necessary to validate the functionality and quality of these services.
D. In order for the services providers to show their superiority and expertise in offering those services to their clients.
QUESTION 40
Mr. Zlate found out his computer is running perfectly after he powered it up, the longer he used it the slower it became. What could be the problem with the computer.
A. A non-bootable floppy disk is in the floppy-disk drive and you should remove it
B. The hard-drive has failed and you should replace it
C. RAM has failed and you should replace it
D. A key on the keyboard is stuck and the keyboard should be replaced
QUESTION 41
is an information system that supports the capturing, processing, storage of transactions and production of a variety of documents related to routine business activities
A. Transaction processing systems
B. Decision support system
C. Executive support systems
D. Management information system
QUESTION 42
Identify from the following, an Extensible Markup Language (XML) related technology.
A. XTML B. XSave
C. XDS
D. XHTML
QUESTION 43
Which of the following commands will high-level format drive C, write the hidden operating system files in the first part of the partition, and prompt for the entry of a volume label to be stored on the disk?
A. Format C: /S/D
B. Format C: /D/S
C. Format C: /S/V
D. Format C: /V/S
QUESTION 44
Which of the following is a public network scam undertaken by cyber-criminals where the user is made to consent digitally to provide confidential information?
A. Man-in-the-Middle Attack
B. Denial-of-Service (DOS) Attack
C. Phishing Attack
D. Password Attack
QUESTION 45
The following are keyboard challenges;
I. Hard to press keys
II. The keyboard not attached to the PC
III. Dusty keys
IV. The keyboard failure
V. Sticky keys
Among those listed above, choose two that are likely to result to an error message “Keyboard error” being displayed on a computer screen.
A. I & II
B. I & III
C. II & IV
D. II & V
QUESTION 46
Which one of the following relates to safe and responsible use of Information and Communication Technologies (ICT)?
A. Cyber ethics
B. Cyber security
C. Cyber safety
D. Computer ethics
QUESTION 47
_________is the area where the computer stores its configuration information.
A. RAM
B. CMOS RAM
C. ROM
D. Flash Memory
QUESTION 48
Businesses, governments, and individuals can experience huge complications from having sensitive information exposed. Identify among the following a step not undertaken by cybercriminals in Data breaching.
A. Reconnaissance
B. Exfiltration
C. Fixing virus
D. System attacks
QUESTION 49
Which of the following cannot be classified as a weekly disk maintenance activity?
A. Backup any data or important files. B. Delete all temporary files
C. Empty the Recycle Bin.
D. Check for and install any operating system updates.
QUESTION 50
Which program runs first after booting the computer and loading the graphical user interface (GUI)?
A. Desktop Manager
B. File Manager
C. Windows Explorer
D. Authentication
QUESTION 51
The is a pathway composed of cables and connectors used to carry data between a computer microprocessor and the main memory.
A. System bus
B. Expansion bus
C. Register
D. Interrupt request (IRQ)
QUESTION 52
Which of the following represents the correct order in which you should install components into the case after disassembling a computer?
A. Power supply, motherboard, drives, cards
B. Drives, motherboards, cards, power supply
C. Cards, motherboard, power supply, drives
D. Motherboard, drives, cards, power supply
QUESTION 53
Which of the following is NOT a cause of blue screen in computers?
A. Faulty memory card
B. Faulty hardware drivers
C. Faulty system software
D. Faulty sound card
QUESTION 54
Which one of the following is a program designed to help users’ detect a computer virus and avoid them?
A. Spyware
B. Antivirus
C. Adware
D. Malware
QUESTION 55
Which of the following is software testing type, in which the testing is performed on each individual component separately without integrating with other components?
A. Acceptance testing
B. Component testing
C. System testing
D. Integration testing
QUESTION 56
Among the statements below, identify the best describing how simple object access protocol (SOAP) is used.
A. It is used for the exchange of information throughout platforms, languages and operating systems.
B. It provides communication and connectivity between the devices and the internet for API-based tasks.
C. It is used to create Web pages and tells the browser how to display them.
D. It is the protocol where encrypted HTTP data is transferred over a secure connection such as Transport Layer Security or Secure Sockets Layer.
QUESTION 57 A customer reported that upon booting up his computer, the message: Invalid drive configuration,” was displayed. What could be the problem?
A. The hard drive power cable within the system unit is faulty
B. The hard drive is not properly connected
C. The hard drive has not been formatted
D. The hard drive cylinder is faulty
QUESTION 58
Evolution of technology has evolved and shaped the way we communicate, learn, and work. In view of the above, which of the following relates to exploring appropriate ethical behaviors in respect to public network usage?
A. Cyber Law
B. Cyber Operations
C. Cyber Ethics
D. Cyber Security
QUESTION 59
is the name given to the processor’s characteristic that offers some protection against overheating.
A. Firmware
B. Spooling
C. Throttling
D. Multiprocessing
QUESTION 60
Which of the following ICT enabled services, is defined as the usage of Information and Communication Technology (ICT) by the government to provide and facilitate government services, exchange of information, communication transactions and integration of various standalone systems and services?
A. E-commerce
B. Mobile ticketing
C. Social networking
D. E-Governance
QUESTION 61
Which of the following is NOT a feature of expert systems?
A. Expert systems can be expensive to develop
B. Expert systems can deal with mixed knowledge
C. Expert systems can explain how and why a decision or solution was reached
D. Expert systems can provide portable knowledge
QUESTION 62
A client called saying that a printer is not working. The printer was brought for repairs. What is the first thing you could do after receiving it?
A. Run MSD diagnostics
B. Attach it to a PC and print something
C. Check the cable
D. Unbox it and examine it for physical damage
QUESTION 63
Which of the following is crucial for organizational development and success and makes an employee become more efficient and productive?
A. Finding system defects.
B. Training employees.
C. Penetration testing.
D. Computer testing
QUESTION 64
Which of the following adheres to the principle of keeping sensitive information highly classified?
A. Confidentiality
B. Availability
C. Integrity
D. Maintainability
QUESTION 65
_________________hardware device used for direct memory access.
A. Power supply
B. ROM BIOS
C. Direct Memory Access controller
D. Hard drive or controller
QUESTION 66
Which of the following is NOT a feature of web services?
A. Interoperability
B. Supports Exchange of Documents
C. Reliable Messaging
D. Security and privacy
QUESTION 67
What type of maintenance defined as “the regular and routine maintenance of equipment and assets in order to keep them running and prevent any costly unplanned downtime from unexpected equipment failure”?
A. Corrective Maintenance
B. Adaptive Maintenance
C. Preventive Maintenance
D. Perfective Maintenance
QUESTION 68
Code of Conduct is regarded as a set of rules pertaining to the use of participatory media. A digital code of conduct forms the basis for user and content moderation. In view of the above, which one among the following is not part of the code of ethics.
A. Integrity
B. Objectivity
C. Integration
D. Confidentiality
QUESTION 69
provides backup power when your regular power source fails or voltage drops to an unacceptable level.
A. High-graded multi-meter
B. Spike protector
C. Uninterruptible power supply
D. Power supply unit
QUESTION 70
Which of the following is defined as an attempt by individual to send anonymous messages to Bluetooth-enabled devices within a certain radius.
A. Cyber attack
B. Bluehacking
C. Cryptography
D. Phishing
QUESTION 71
Internal components are devices that are connected to computer’s motherboard or built-in to the motherboard. Among the following which one is NOT an internal component of a computer?
A. Monitor
B. Hard disk
C. Power supply unit
D. Memory card
QUESTION 72
Point-to-Point connection between devices can be connected to a single cable with a minimum of four wires. Identify this cable among the following.
A. IDE
B. ATA Ribbon
C. SAPA
D. SATA
QUESTION 73
A temporary storage location inside the computer central processing unit (CPU) that stores data and addresses is known as
_________________.
A. Control unit
B. Arithmetic and logic unit
C. Register
D. Input/output unit
QUESTION 74
User Integration is designed to manage the organizational changes companies are challenged with on a daily basis. Which of the following is NOT regarded as proper aspect of user integration?
A. Physical Authorization
B. Employee Authentication
C. Access Control
D. User database representation.
QUESTION 75
Which of the following concepts describe the situation when a computer user runs the motherboard or processor at higher speed than the manufacturer specification?
A. Overclocking
B. Throttling
C. Overheating
D. Multi-core processing
QUESTION 76
Which of the following are the three types of motherboard form factors?
A. Mini-ITX, Micro-ATX and ATX.
B. Mini-ATX, Micro-ATX and ATX.
C. Mini-ITX, Macro-ATX and ATX.
D. Mega-ITX, Micro-ATX and ATX.
QUESTION 77
Which one of the following is a benefit of electronic waste management?
A. Existing facilities not designed to handle
B. Heavy, Bulky and complex Waste to process,
C. Requires special logistics and new handling facilities, with new e-waste processing Technology
D. Protects the surroundings
QUESTION 78
Which of the following conforms to the concept of protecting the functionality of support systems and ensuring data is fully accessible at any given point in time?
A. Availability
B. Confidentiality
C. Integrity
D. Authenticity
QUESTION 79
Which one of the following is an element to be used for security operations center?
A. People
B. Data centre
C. Database engine D. Internet Connection
QUESTION 80
Printers can be classified based on printing speed. How is the speed of a dot matrix printer expressed?
A. lines per second
B. lines per minute
C. characters per inch
D. characters per second
QUESTION 81
Which of the following end devices can bring external files and virus along with it to the internal systems?
A. Laptops
B. Smart phone
C. Tablet
D. Pen-drive
QUESTION 82
Mr. Tumbili turned on his tablet and got a message displaying a message indicating that all of his files have been locked. In order to get the files unencrypted, he is supposed to send an email and include a specific ID in the email title. The message also includes ways to use blockchain as payment for the file decryption. After inspecting the message, the network analyst suspects a security breach occurred. What type of malware could be responsible?
A. Trojan horse
B. Adware
C. Spyware
D. Ransomware
QUESTION 83
Never expose laser printer under direct sunlight as heat from sunlight would impact its performance. Identify the part of
the laser printer that should NOT be exposed to sunlight?
A. Transfer corona assembly
B. Printer PC
C. Primary corona wire
D. Toner cartridge
QUESTION 84
Which one of the following gives the assurance that the information is trustworthy and accurate?
A. Authenticity
B. Availability
C. Integrity
D. Confidentiality
QUESTION 85
Printdeal Ltd is a company dealing with a variety of printers. A customer reported that the print quality of a dot matrix printer acquired recently has changed from light to being dark. Identify the possible cause of this problem.
A. Paper slippage
B. Improper ribbon advancement
C. Paper thickness
D. Head position
QUESTION 86
Which one of the following is unwanted software designed to throw advertisements up on your screen, most often within a web browser?
A. Adware
B. Virus
C. Macro virus
D. Bootsector virus
QUESTION 87 Which one of the following refers to the abuse of computers and high-technology appliances to undermine computing resources of an adversary?
A. Information Warfare
B. Electronic Warfare
C. Cyber Crime
D. Cyber Reconnaissance
QUESTION 88
Which of the following is NOT a good proposal towards dealing with the challenges of e waste?
A. Discourage investment in this sector.
B. Promote recycling units to ease process and to encourage generators to have proper e-waste disposal.
C. Impart training to generators on e-waste handling.
D. Tax incentives for scrap dealers.
QUESTION 89
Which one of the following identifies the actual sender and recipient of a message alongside information such as date/time of transmission and intention of sender?
A. Database Forensics
B. Malware Forensics
C. Email Forensics
D. Network Forensics
QUESTION 90
________________is an updated system for booting computers that include support for 64bit systems.
A. CMOS
B. BIOS
C. UEFI
D. POST
QUESTION 91
What is the name of the term that describes a sudden increase in voltage that lasts for a short period and exceeds 100 percent of the normal voltage on a power line?
A. Power Surge
B. Spike
C. Hypertransport
D. Serial ATA (SATA)
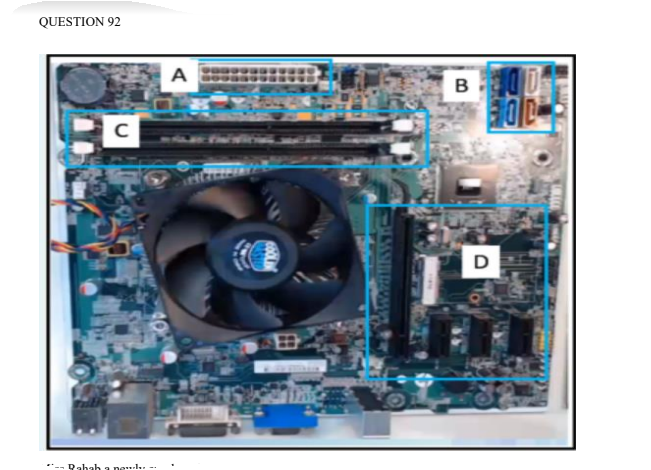
Miss Rahab a newly employed technician is installing a second SATA hard drive. Which section of the following sections on the motherboard can be used to connect the SATA cable?
A. SECTION D
B. SECTION A
C. SECTION B
D. SECTION C
QUESTION 93
____________________CPU architecture that uses a broad set of instructions, resulting in fewer steps per operation.
A. Hyperthreading
B. Complex Instruction Set Computer (CISC)
C. Hypertransport
D. Safety Data Sheet (SDS)
QUESTION 94
Which one of the following uses NAND, a type of flash memory named after the NAND logic gate to hold some important data in solid state storage on a hard disk drive device?
A. Solid state Hybrid Drive (SSHD)
B. Hard Disk Drive (HDD)
C. Solid state Drive (SSD)
D. Nonvolatile memory express (NVMe)
QUESTION 95
Which one of the following best describes direct consequence of identity theft?
A. Your keyboard or mouse may stop working
B. Your email account may be accessed by someone else.
C. Your computer may take longer to start.
D. Your broadband connection may suffer from reduced speed
QUESTION 96
Which of the following is a type of electronic surveillance that is used in criminal investigations?
A. Wiretapping
B. Network tapping
C. Switchport analyzer
D. Port Mirroring
QUESTION 97
Over time different technologies and solutions have been proposed to secure users’ information online or offline. Which one of the following is considered to be a traditional authentication method?
A. Secure socket layer
B. Transport Layer Protocol
C. Password-based authentication
D. Secure Socket Shell
QUESTION 98
Which of the refers to the use of ICT to introduce, reinforce, supplement and extend skills?
A. Integrity
B. Objectivity
C. Integration
D. Confidentiality
QUESTION 99
Which one of the following is not a technique used to obfuscate data?
A. Encryption
B. Tokenization
C. Cryptography
D. Data Masking
QUESTION 100
Mr.Lidibwe downloaded a free game app for her daughter. He discovered a malware hidden inside that runs at the background of the device. Which type of security flow occurred to his device?
A. Filejacking
B. Spyware
C. Adware
D. Trojan
