INSTRUCTIONS TO CANDIDATES
Answer all questions
Select correct answers in the questions below
1. Which of following technologies was used in the first generation of computers?
a. Vaccum tubes and magnetic drum
b. Integrated circuits
c. Magnetic tape
d. Transistors
2. The series of repeatable steps taken by a team to achieve business goal is known as?
a. Business intelligence
b. Business process
c. Quality process
d. Business process re-engineering
3. Choose a programming language that is in the category of low level
a. Procedural language
b. Assembly language
c. Machine language
d. Logic programming
4. In which layer of the client computing architecture does the business logic lie?
a. 1st Tier
b. 2nd Tier
c. 3rd Tier
d. 4th tier
5. Which of the following data processing mode is suitable for data that is required for immediate decision making?
a. Batch processing
b. Electronic data processing
c. Realtime processing
d. Multiprocessing
6. Which of the following is used to link devices of different topology?
a. Switch
b. Router
c. Hub
d. Modem
7. Which of the following is NOT a task in system analysis stage of system development life cycle?
a. Decomposition
b. Problem formulation
c. Creating functional requirements.
d. Creating flowcharts
8. Which of the following is stored in flash memory chip?
a. BIOS
b. Operating system
c. Compiler
d. Application software
9. In which category does android software belong?
a. Application software
b. Firm ware
c. Operating system
d. Kernel.
10. Choose the layer in which Simple Mail Transfer Protocol (SMTP) is found in the TCP/IP protocol?
a. Transport layer
b. Internet layer
c. Network layer
d. Application layer
11. Select from the following a set of processes and procedures that transform data into information.
a. Information system
b. Knowledge system
c. Expert system
d. Operating system
12. Which of the following computers will be the most appropriate for intensive mathematical and scientific application?
a. Mainframe computers
b. Super computers
c. Hybrid computers
d. Mini computers
13. Which of the following programming languages is an Object-Oriented programming language?
a. Pascal
b. LISP
c. JAVA
d. C
14. Which of the following is NOT a technological impact of Covid-19 lock down?
a. Increased eLearning
b. Innovation
c. More use of video conferencing
d. Closure of schools
15. Which of the following is used to design computer programs?
a. Flowchart
b. Loader
c. Editor
d. Debugger
16. Identify the challenges of ring topology in a network.
a. Complexity
b. Any node failure affects the entire network
c. Expensive
d. Insecure.
17. What is the name given to a document used when a company goes outside its organization to develop a new system?
a. Request for expression of interest
b. Request for invoice
c. Request for proposal
d. Request for comments
18. What is equivalent of 5KB into bytes?
a. 1000 bytes
b. 5000 bytes
c. 5120 bytes
d. 40 bytes
19. Which of the following is a programming methodology?
a. Event driven
b. Design
c. Analysis
d. Coding
20. Which of the following is NOT an ethical concern in computer networking?
a. Hardware failure.
b. Hacking
c. Tapping
d. Copyright
21. Which of the following is an advantage of programming using low level languages?
a. Easy to learn
b. Portable
c. Fast processing
d. Compatibility
22. Which of the following determines the speed of a computer?
a. Bus width
b. Manufacturer
c. Motherboard
d. Software.
23. Identify an input device captures data directly from the source
a. Keyboard
b. Mouse
c. Optical character recognition
d. Touch screen
24. Which part of the motherboard allows users to add new devices and capabilities to a computer system?
a. Expansion slots
b. Sockets
c. Ports
d. Chipset
25. Which of the following is a short-range wireless connectivity technology?
a. WIFI
b. Satellite
c. Bluetooth
d. Microwave
26. Which of the following statements correctly defines Sequential file organization technique?
a. Method of storing records in contiguous blocks according to a key
b. Storing records sequentially but using an index to locate records
c. Using an index for each key type
d. Having records placed randomly throughout the file
27. Which of the following is NOT used in a Local Area Network?
a. Computer
b. Frame-Relay.
c. Router
d. Logical Address
28. Which of the following is NOT a system investigation technique?
a. Surveys
b. Observation
c. Review previous studies
d. Consultation
29. A compiler is used to convert the source code written in mnemonics into object code.
a. True
b. False
30. Software that prevents unauthorized access to a network located between a private network and an outer
network on the Internet restricting Internet traffic in, out or within a private network is referred to as?
a. Firmware
b. Firewall
c. Antivirus
d. Malware
31. What is the name given to the mechanism of protecting critical systems and sensitive information from digital attacks?
a. Protection
b. Encryption
c. Decryption
d. Cybersecurity
32. Which of the following is an example of a control structure? a. Arrays
b. Lists
c. For loop
d. Vector
33. Given that x=2, what is the answer expected from x>5? a. True
b. False
c. Yes/No
d. 0/1
34. Which of the following is the first to be done to a variable? a. Declaration
b. Inputting
c. Outputting
d. Processing
35. Choose the location where a programmer may NOT choose to store program data. a. Text files
b. Databases
c. Memory
d. ROM
36. Match the programs with their functions
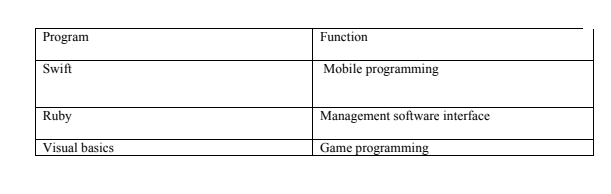
a. C-> y, E->z, d->y
b. C->x,d->z,e->y
c. C->z,d->x,e->y,
d. x->C,d->z,e->y
37. Which of the following is the smallest piece of information in data processing? a. 6 bits
b. Byte
c. Nibble
d. Word
38. Which of the follow technology provides the fastest secondary storage? a. Magnetic storage
b. Optical storage
c. DIMM
d. Flash memory
39. Which of the following is NOT a type of software testing? a. Smoke
b. Troubleshooting
c. Beta
d. Integration
40. Choose the name of the software produced by a proprietary company when testing software. a. Open source
b. Freeware
c. Proprietary
d. End user agreement
41. Which of the following technologies was the first to be widely affected by ICT technology? a. Mailing
b. Welding
c. Weather forecasting
d. Mineral exploitation
42. Below are reasons why companies create new programming languages, which one is not? a. Better performance
b. Increase development costs
c. Security of their software
d. To fit their needs
43. Which of the following is the role of a database administrator in an organization? a. Debugging
b. Set and maintain database standards
c. Creating database programs.
d. Designing software application
44. Why do organizations opt for tailor made software instead of off the shelf software? a. Precise requirements
b. Better documentation
c. Less errors
d. Costs less
45. What is the danger of locating an organization server on a cloud location? a. Availability
b. Security
c. Performance
d. Elasticity
46. Which of the following is LEAST likely to be caused by using a computer? a. Backache
b. Strain Injury
c. Eye problems
d. Hearing problems
47. Which of the following command is used in network troubleshooting? a. Dir
b. Chdir
c. apipa
d. ping
48. Which of the following is a CASE tool?
a. Diagramming tool
b. MYSQL
c. Word processor
d. Corel draw
49. Which of the following tool is the most suitable for prototyping? a. Oracle
b. JAVA
c. Visual Basic
d. C++
50. Which of the following is the MAJOR concern among parents on ICT? a. Time saving
b. Cyber bullying
c. Loss of gadgets
d. Expenses
51. Which level of management uses decision support systems? a. Transaction managers
b. Supervisors
c. Strategic managers
d. Users
52. Which of the following is a part of an expert system? a. Inference engine
b. An expert
c. A database
d. Kernel
53. Which of the following is NOT a type of programming error?
a. Logical
b. Bug
c. Syntax
d. Run-time
54. The process of contracting a certain project or an entire business task to an external service provider that specializes in the service is called______________.
a. insourcing
b. self-sourcing
c. sourcing
d. outsourcing
55. Select the type of information system that stores knowledge from a specific domain
a. Expert system
b. Decision Support System
c. Knowledge Worker System
d. Management of Information System
56. Which one of following is a characteristic of Online Analytical Processing (OLAP)?
a. It allows both read and write operation
b. It allows only read and hardly write operations
c. OLTP employs traditional DBMS
d. It holds current operational data
57. Select the application that is used at the operational level of an information system
a. Payroll system
b. Logistics systems
c. Group decision support systems
d. Budgeting systems
58. Which of following is NOT a problem-solving tool in programming?
a. Decision tree
b. Decision table
c. Algorithm
d. Pivot tables
59. A graphical representation of an algorithm is known as a?
a. Work flow diagram
b. Flowchart
c. Pixel
d. Pseudocode
60. The translator that coverts source code written in a high-level language to the object code by translating all the code at once is called?
a. Assembler
b. Loader
c. Interpreter
d. Compiler
61. ___________ is the programming paradigm that focuses on the logic of computation while neglecting the control.
a. Declarative
b. Imperative
c. Procedural
d. Object-oriented
62. Select the name of the condition caused by excessive use of the computer causing a series of eye problems due to staring at the monitor of a computer for a long period of time.
a. Repetitive Strain Injury
b. Carpal Tunnel Syndrome
c. Computer Vision Syndrome
d. Blindness
63. Select the type of testing that takes place at the end users’ site by the end users to validate the usability, functionality and compatibility of software.
a. Unit testing
b. Stress testing
c. Beta testing
d. Alpha testing
64. The problem-solving technique, that is concerned with the breaking down a task into smaller manageable tasks that are easier to debug is referred to as?
a. Abstraction
b. Decomposition
c. Module
d. Algorithm
65. Which programming control structure is used for executing repetitive statements in programming?
a. Iteration
b. Recursion
c. Selection
d. Sequential
66. The study of the sitting posture when using computers is known as?
a. Egocentric
b. Gymnastic
c. Econometric
d. Ergonomics
67. The application area of computing that tries to mimic the reasoning of a human being in problem solving is known as?
a. Virtual reality
b. Artificial intelligence
c. Augmented reality
d. Machine learning
68. The system program that takes the object code of a program as input and prepares it for execution is called?
a. Compiler
b. Debugger
c. Loader
d. Linker
69. Which of the following can cause eye strains when using computers monitors?
a. Use of antiglare screen
b. Using computers with flickers
c. Use a wrist rest
d. Using adjustable chairs
70. Which of the following is the correct steps for program life cycle?
a. Analysis- Coding -Design- Testing-Maintenance
b. Analysis-Design-Coding-Testing-Maintenance
c. Analysis-Design- Maintenance -Coding-Testing
d. Analysis- Maintenance -Design-Coding-Testing
71. Working from a location other than an office using modern technology and telecommunications to remain in touch with your employer is called?
a. Teleconferencing
b. Outsourcing
c. Telecommuting
d. Teamworking
72. The diagram below represents a typical computer network.
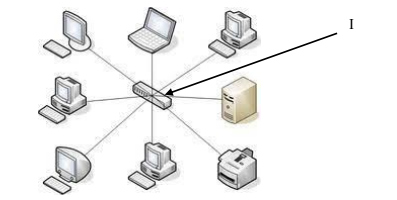
Suggest the name of the part labeled I on the diagram.
a) Controller
b) Node
c) Bus
d) Hub
73. The following is a list of disadvantages of a Star topology. Which one is NOT?
a) Not easy to extend the network
b) Expensive to install
c) Extra hardware is required adding to the cost.
d) Requires more cable
74. Match each of the following types of computer files with their corresponding descriptions
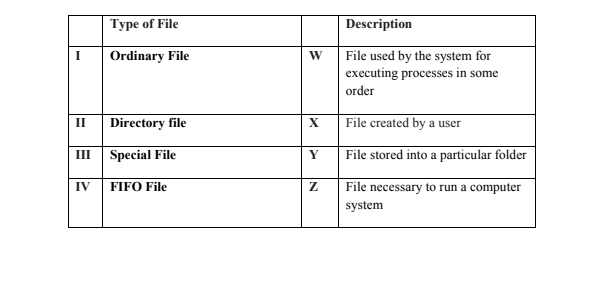
a) I -W, II -X, III -Y, IV-Z
b) I-X, II -Y, III -Z, IV -W √
c) I -Z, II -Y, III -X, IV-W
d) I -Y, II -W, III -X, IV -Z
75. When is it necessary to use rapid application development method of information system development in an organization?
a) When there is no need to encourage customer feedback
b) When there is no need of increasing reusability of components
c) When there is scarcity of qualified designers.
d) When the system is required in a short duration
75. Given below are importance of Online Analytical Processing (OLAP) in a business data warehouse. Which one is NOT?
a) Finding some clusters and outlier data is easy
b) It avoids analyzing time series data which is not necessary to a business
c) Provides building blocks for business modeling tools
d) Quickly create and analyze ‘what if’ scenarios.
76. Below is a list of drawbacks of mobile commerce. Which one is NOT?
a) Data privacy concerns
b) Internet connectivity
c) Shipping costs
d) Size of the gadget
77. Information technology raises a number of legal and ethical issues. Which among the following is a legal issue raised by information technology?
a) Access right
b) Personal privacy
c) Trade Secrets
d) Data protection
78. The following is a list of types of decision support system. Which one is NOT?
a) Menu-driven
b) Communication-driven
c) Data-driven
d) Knowledge-driven
79. Information and communication technologies (ICT) have impacted entertainment and leisure activities in different ways. Choose one entertainment and leisure activity from the list below.
a) Video production
b) Video conferencing
c) News editing
d) Swimming lessons
80. Which of the following types of file correctly matches with its corresponding application software
a) Kasneb.xlsx – Microsoft Text
b) Kasneb.txt – Notepad
c) Kasneb.pdf – Microsoft PowerPoint
d) Kasneb.pptx -Microsoft publisher
81. Which of the following is NOT an arithmetic operator in programming?
a. ==
b. >=
c. >
d. =
82. What is the result of the operation 5%2
a. Invalid
b. 0
c. 2.5
d. 1
83. Which of the following stores historical data?
a. Database
b. Operational data
c. Data warehouse
d. Online database
84. Which of the following is NOT a system software?
a. Utility
b. Operating system
c. Spreadsheet
d. Language translator
85. A business professional who uses analysis and design techniques to solve business problems by using information technology and requires more in-depth technical knowledge is called?
a. Business analyst
b. System analyst
c. Programmer
d. System Programmer
86. Which of the following is proprietary Operating System?
a. UNIX
b. Android
c. Windows
d. CENTOS
87. In a computer architecture, a bus is a group of wires that connects different components of the computer. Which of the following is a computer bus?
a. Control
b. Register
c. Link
d. Width
88. Computing system can be used as more general term to describe a system that is used to solve problems and interact with the environment. Which of the following is NOT a component of the computing system?
a. Procedures
b. Orgware
c. Data
d. Reports
89. ____________is a diagram that depicts the interactions between the system and external system users
a. Use-case
b. Activity diagram
c. Flowchart
d. UML
90. The technology that superimposes information such as text, image, sound on the real world and enhances a part of the user’s physical world with computer-generated digital information is known as?
a. Virtual Reality
b. Computer Graphics
c. Augmented Reality
d. Animation
91. A type of software that is burnt into a hardware is called?
a. Operating system
b. Firmware
c. Freeware
d. Shareware
92. The natural counting numbers are to base?
a. 10
b. 2
c. 8
d. 7
93. A network device that BEST broadcasts information to the correct network segment is called?
a. Switch
b. Hub
c. Bridge
d. Router
94. Which of the following is the main shortcoming of outsourcing ICT services?
a. Speed
b. Location
c. Performance
d. Data security
95. Identify the correct statement about information systems
a. Different information systems types are used by different levels of management
b. All parts of an information system are used by any group of users
c. All information can be stored in any location.
d. Security is more important that access in a system
96. Which of the following application does NOT use artificial intelligence?
a. Robotics
b. Face recognition
c. Natural language processing
d. Smart card authentication
97. Consider the code below
While (i<=5){
x=x+2
print i
}
If x is 3, what is the output?
a. 5,7
b. 3,5
c. None
d. 3,3
98. Which of the following displays has the LEAST favourable output?
a. Gas plasma
b. Cathode Ray Tube
c. Light Emitting Diode
d. Liquid Crystal Display
99. Identify the address that is inbuilt in a physical computing device?
a. IP address
b. Routing table
c. MAC address
d. Subnet mask
100.Which of the following is the MOST effective method of securing organization data?
a. Employing watchmen
b. Using firewalls
c. Using identification badges
d. Using grills on doors
