BASIC COMPUTER NETWORKING
Definition of a Computer Network
A computer network refers to a group of two or more computers or other hardware devices
connected/linked together for purposes of sharing resources, such as files, programs, printers etc.
The computers on a network may be linked through cables, radio waves, satellites, or infrared light
beams.
Computers on a network use protocols which define a common set of rules and signals to
communicate.
NB/ Computers that are not connected to one another are known as stand-alone computers.
ADVANTAGES OF COMPUTER NETWORKING
i) Facilitating communications. Using a network, people can communicate efficiently and easily
via e-mail, chat rooms, telephony, video telephone calls, and videoconferencing.
ii) Sharing resources and reducing costs. In a networked environment, each computer on a
network can access and use hardware and software on the network. If several computers and a
printer are connected to a network, each user can access the printer on the network, as they
need it instead of buying as many printers. Other resources include files, applications and disk
storage.
Network resources include:
Printers and other peripherals
Files, data and information
Applications/programs
Disk Storage
iii) It enables distributed processing which allows a user at one computer to use a program on
another computer as a “back end” to process and store the information. The user’s computer is
the “front end,” performing the data entry.
iv) Centralized data administration and support. Data from all the user systems can be stored on
one machine where it can be managed in an easy and more secure way.
v) Users can store more information, because they can now store data on other computers on the
network.
vi) They allow users to use programs that would otherwise be too large for their computer to run
by itself.
DISADVANTAGES
| i. ii. |
The cost of hardware, software and cabling might be quite high Complexity of many LANs means that it is often necessary to employ someone to look after |
the network and solve problems relating to the system.
iii. Security of data may be a problem if adequate procedures are not adopted.
iv. Any failure in the system often means that it becomes impossible for users to work.
TYPES OF NETWORKS
Categorization can be based on the following criteria:
• Based on transmission media: Wired (Guided media) and Wireless (Unguided medium)
For guided media, there is a physical path such as a cable for signal propagation, while in
unguided media; the electromagnetic wave is transmitted through air.
• Based on network size: LAN and WAN (and MAN)
• Based on management method: Peer-to-peer and Client/Server
• Based on topology (layout): Bus, Star, Ring …
Networks based Size
i) Local Area Networks (LANs)
The smallest and simplest networks are called local area networks (LANs), which extend
over only a small area, typically within a single office, building or a part thereof. In addition to
operating in a limited space, LANs are also typically owned, controlled, and managed by a
single person or organization. They also tend to use certain connectivity technologies,
primarily Ethernet and Token Ring.
A home network is a type of LAN that is contained within a user’s residence.
ii) Wide Area Networks (WANs)
Wide area networks
(WANs) can extend over a large geographic area e.g. across
metropolitan, regional, national or continental boundaries and are connected via the
telephone network or radio waves. A WAN is a geographically-dispersed collection of LANs.
A network device called a router connects LANs to a WAN. In IP networking, the router
maintains both a LAN address and a WAN address.
A WAN differs from a LAN in several important ways. Most WANs (like the Internet) are not
owned by any one organization but rather exist under collective or distributed ownership
and management.
iii) Metropolitan Area Network (MAN) / Campus Area Network (CAN)
A metropolitan area network (MAN) is designed to serve a town or city, and a campus area
network is designed to serve a university, military base or an educational institution.
A metropolitan area spans a physical area larger than a LAN but smaller than a WAN, such
as a city. A MAN is typically owned and operated by a single entity such as a government
body or large corporation.
iv) Intranet
An intranet is a private network within an organization that uses the same communications
protocols as the Internet (internet protocol). It is sometimes contrasted to extranets. An
Intranet is used strictly within the confines of a company, university, or organization and is
based on the internet standards (HTML, HTTP & TCP/IP protocols). An intranet’s Web sites
look and acts just like any other Web sites, but the firewall surrounding an intranet fends off
unauthorized access.
v) Extranet
This is a computer network that allows controlled access from the outside, for specific
business or educational purposes. It uses Internet technology and the public
telecommunication system to securely share part of a business’s information or operations
with suppliers, vendors, partners, customers, or other businesses. An extranet requires
security and privacy. These can include firewall server management, the issuance and use
of digital certificates or similar means of user authentication, encryption of messages, and
the use of virtual private networks (VPNs) that tunnel through the public network.
Virtual Private Network (VPN)?
A virtual private network (VPN) is a network that uses a public telecommunication
infrastructure, such as the Internet, to provide remote offices or individual users with secure
access to their organization’s network. A virtual private network can be contrasted with an
expensive system of owned or leased lines that can only be used by one organization. The
goal of a VPN is to provide the organization with the same capabilities, but at a much lower
cost
vi) internet/internetwork
An internet (spelt with a lower case i) is a network that is composed of a number of smaller
computer networks.
vii) The Internet
The Internet (spelled with an upper case I) is the world-wide network of interconnected
internets that operates using a standardized set of communications protocols called TCP/IP
(transmission control protocol/Internet protocol), or the Internet protocol suite. This
ultimate internet is vastly larger than any other internet and connects thousands of networks
and hundreds of millions of computers throughout the world. The Internet is, therefore, an
internet.
TCP/IP provides end-to-end connectivity specifying how data should be formatted,
addressed, transmitted, routed and received at the destination. From lowest to highest, the
layers are the link layer, containing communication technologies for a single network
segment (link), the internet layer, connecting hosts across independent networks, thus
establishing internetworking, the transport layer handling host-to-host communication, and
the application layer, which provides process-to-process application data exchange e.g.
HTTP, SMTP, FTP.
Types of Networks based on management method:
PEER-TO-PEER NETWORKS
Peer-to-peer networks are also called workgroups and there exists no hierarchy among computers;
all computers are equal. No administrator is usually responsible for the network. Peer-to-peer
networks are appropriate for small, simple, and inexpensive networks. This type of network is
appropriate where:
• 1 0 or less users
• No specialized services required
• Security is not an issue
• Only limited growth in the foreseeable future

Advantages of peer-to-peer networks/workgroups
• Low cost of implementation
• Simple to configure
• User has full access to computer resources
Disadvantages of peer-to-peer networks
• May have duplication in resources
• Difficult to uphold security policy
• Difficult to handle uneven loading – unequal distribution of tasks among the workstations
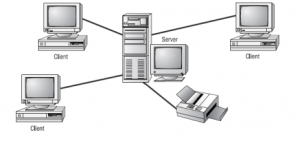
SERVER-BASED NETWORKS (CLIENT/SERVER MODEL)
A computer network in which one centralized, powerful computer (called the server) is a hub to
which many less powerful personal computers or workstations (called clients) are connected. The
clients run programs and access data that are stored on the server. Network Clients (Workstations)
computers request network resources or services while the network Servers provide network
resources and services to clients.
A server usually has more processing power, memory and hard disk space than clients and run
Network Operating System that can manage not only data, but also users, groups, security, and
applications on the network. Servers often have a more stringent requirement on its performance
and reliability.
Server-based networks use a dedicated, centralized server. All administrative functions and
resource sharing are performed from this point. This makes it easier to share resources, perform
backups, and support an almost unlimited number of users. It also offers better security. However,
it does need more hardware than that used by the typical workstation/server computer in a peer-to
-peer resource model.
A good example of a server based network is a domain which refers to a group
of computers and devices on a network that are administered as a unit with common rules and
procedures. Domain-based networks are composed of any number of computers and at least one
Domain Controller (DC). The workstations could be used by employees and users in the
organization, while the Domain Controller, known as a Server, is capable of managing the user
workstations in many different respects.
| Peer-to-Peer Networks vs Client/Server Networks | |
| Peer-to-Peer Networks | Client/Server Networks |
| 1 . Easy to set up | More difficult to set up |
| 2. Less expensive to install | More expensive to install |
| 3. Can be implemented on a wide range of operating systems |
A variety of OSs can be supported on the client machines, but the server needs to run an Operating System that supports networking i.e NOS. |
| 4. More time consuming to maintain the software being used (as computers must be managed individually) |
Less time consuming to maintain the software being used (as most of the maintenance is managed from the server) |
| 5. Very low levels of security supported or none at all. |
High levels of security are supported, all of which are controlled from the server including access to individual workstations. Such measures prevent the deletion of essential |
| system files or changing of settings. | |
| 6. Ideal for networks with less than 1 0 computers |
No limit to the number of computers that can be supported by the network |
| 7. Does not require a server | Requires a server running a network operating system |
| 8. Demands a moderate level of skill to administer the network |
Demands that the network administrator has a high level of IT skills with a good working knowledge of a server operating system |
NETWORK COMPONENTS
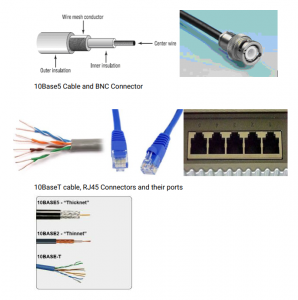
(a)Networking Cables
The two most popular types of network cabling are the 1 0BaseT (also known as twisted pair
or Cat5), 1 0Base5 (also known as Thicknet) and thin coax (also known as 1 0Base2 or
Thinnet). The “1 0” in 1 0Base5 stands for the 1 0 Mbps transmission rates while the “5”
stands for the maximum distance of 500 meters to carry transmissions. The pairs are
twisted together for the purposes of cancelling out electromagnetic interference (EMI) from
external sources
1 0BaseT cabling looks like ordinary telephone wire, except that it has 8 wires inside instead
of 4, transmits at 1 0Mbps, with a maximum distance of 1 00 meters and physical star
topology with a logical bus topology. There are basically two types of twisted-pair cabling:
unshielded twisted-pair (UTP) and shielded twisted-pair (STP). UTP is simply twisted-pair
cabling that is unshielded. In STP cables, each of the pair or collection of pair of wires that
are twisted together are coated with an insulating coating that functions as a ground for the
wires which protects the transmission line from electromagnetic interference leaking into or
out of the cable.
Thin coax looks like the copper coaxial cabling that’s often used to connect an aerial
antenna to a TV set. The 1 0baseT/Cat5 cables have connectors that resemble a phone cord
connector, only larger. These are called RJ-45 connectors. Coaxial cables are connected
using BNC connectors.
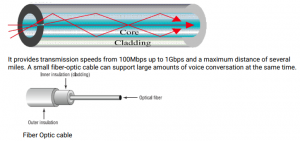
Fiber Optic Cables– signals are converted to light form and fired by laser or LEDs in bursts
through insulated, thin glass or plastic fiber. Light bounces back and forth along the core. The
pulses of light represent the ‘on’ state in electronic data representation. An optical fiber consists of
a core (denser material) and a cladding (less dense material)
Advantages of Fiber
Noise resistance ― external light is blocked by outer jacket.
Less signal attenuation ― a signal can run for miles without regeneration (currently, the
lowest measured loss is about 4% or 0.1 6dB per km).
Higher bandwidth ― currently, limits on data rates come from the signal
generation/reception technology, not the fiber itself.
Completely immune from wiretapping.
Disadvantages
Cost – Optical fibers are expensive.
Installation/maintenance – any crack in the core will degrade the signal, and all connections
must be perfectly aligned.
Wireless Technology
i. Microwave Communications
Information is converted to a microwave signal, sent through the air to a receiver, and
recovered. They use line-of-sight devices which must be placed in relatively high locations.
Microwaves are electromagnetic waves which are “small” compared to waves used in
typical radio broadcasting, in that they have shorter wavelengths.
ii. Satellite Transmission
Communications satellites are relay stations that receive signals from one earth station and
rebroadcast them to another
They use microwave signals
iii. Infrared transmission
Involves sending signals through the air via light waves and requires line-of-sight and short
distances (a few hundred yards). It is used to connect various computing devices. Infrared
waves are electromagnetic radiation with longer wavelengths than those of visible light.
iv. Bluetooth
Bluetooth is a specification (IEEE 802.1 5.1 ) for the use of low-power radio communications
to link phones, computers and other network devices over short distances without wires.
Bluetooth technology was designed primarily to support simple wireless networking of
personal consumer devices and peripherals, including cell phones, PDAs, and wireless
headsets. Wireless signals transmitted with Bluetooth cover short distances, typically up to
30 feet (1 0 meters). Bluetooth devices generally communicate at less than 1 Mbps.
(b)Hub
The central connecting device is called a hub. A hub is a box that is used to gather groups of
PCs together at a central location using cables. A hub simply passes all the information it
receives so that all the devices connected to its ports receive the information. Hubs are
mostly used in a small network (usually less than 30 hosts). Hubs connect LANs of similar
technology or to extend the distance of one LAN. They can be called repeaters or amplifiers.
Advantages of using Hubs
i. They are inexpensive
| ii. | Easy to install |
| iii. | Can connect different media |
| iv. | Very little delay |
| Disadvantages | |
| i. | Limited distance between devices |
| ii. | No protocol or rate conversion |
| iii. | No error detection |
| iv. | Does not filter packets |
(c) SWITCH
The Switch is a more advanced unit over the basic hub. Unlike a hub, a switch will forward
information/packets to the appropriate machine or port according to the address
information on a particular packet. Switches are used on large networks in order to cut
down the amount of unnecessary traffic being generated. They can use the same or different types of cable.
Advantages
i. Can convert protocols
| ii. | They enhance network performance |
| iii. iv. |
Can be configured Enhances security- only destined device receives the packet. |
| Disadvantages | |
| i. | More expensive than hubs |
| ii. | Higher maintenance demands |
| iii. | It does filter packets |
| iv. | Does error detection |

Router
Routers are highly intelligent devices that connect multiple network types and determine the
best path for sending data. They can route packets across multiple networks and use
routing tables to store network addresses to determine the best destination.
They can segment large networks and can filter out noise. However, they are a bit slow
because they are intelligent devices; as such, they analyze every packet, causing packetforwarding delays. Because of this intelligence, they are also more expensive.
Routers are normally used to connect one LAN to another. Typically, when a WAN is set up,
there will be at least two routers used.
Routing moves data on a hop-by-hop basis, what is often called ‘hot potato’ routing. If a set
of routers ends up passing the data around in a circle, without reaching the destination, it’s
called a ‘routing loop’. Packets get tossed around the loop until they die of old age: their
‘Time To Live’ counter in the IP datagram is decremented as it passes through each router
and eventually it reaches zero and is discarded.

Network Adapter Card
A computer is connected to the network through a network interface card, (also called a
“NIC”, “nick”, or network adapter). Network cards convert the binary data generated by the
computer into electrical voltages or optical signals in the case of fiber optic NICs and
converts received signals to binary data for use by the computer.

Servers
A sever is a computer system that provides essential services across a network, to private
users inside a large organization or to public users in the internet. They typically are
configured with additional processing, memory and storage capacity to handle the load of
servicing clients.
Servers offer networks the capability of centralizing the control of resources and can thus
reduce administrative difficulties. Servers perform several tasks. For example, servers that
provide files to the users on the network are called file servers. Likewise, servers that host
printing services for users are called print servers.
Servers can be multi-purpose or single-purpose. If they are multi-purpose, they can be, for
example, both a file server and a print server at the same time. If the server is a singlepurpose server, it is a file server only or print server only.
Another distinction we use in categorizing in categorizing servers is whether they are
dedicated or non-dedicated. Dedicated Servers are assigned to provide specific applications
or services for the network, and nothing else. Non-dedicated Servers are assigned to
provide one or more network services and local access.
(g) Network Operating Systems (NOSs)
PCs use a disk operating system that controls the file system and how the applications
communicate with the hard disk. Networks use a network operating system (NOS) to control
the communication with resources and the flow of data across the network. The NOS runs
on the server. Some of the more popular network operating systems at this time include
Unix, Novell’s NetWare, and Microsoft’s Windows NT Server (or Windows 2000).
(h) Gateways: A gateway is a device used to connect networks using different protocols.
Broadly, a gateway is any connection point or node on a network that provides access to a
larger one and therefore a router is a gateway. They translate one network protocol and data
formats to another. They can translate from network-to-network, system-to-network and
system-to-system. Another example of gateway is a bridge.
(i) Workstations or Client Computers
Workstations are the computers that the users on a network do their work on, performing
activities such as word processing, database design, graphic design, e-mail, and other office
or personal tasks. Workstations are basically nothing more than an everyday computer,
except for the fact that they are connected to a network that offers additional resources.
Workstations can range from a diskless computer system to a desktop system. In network
terms, workstations are also known as client computers.
(j)Terminal
This is the hardware, usually made up of a monitor, keyboard, mouse, etc, used to
enter, retrieve and display electronic data from a computer/server through a network.
(k) Repeaters
These are network devices used to regenerate or replicate a signal distorted by
transmission loss. They allow a cabling system to extend beyond its maximum allowed
length by amplifying the network voltages so they travel farther. Repeaters are amplifiers
and, as such, are inexpensive. Repeaters can only be used to regenerate signals between
similar network segments.
(l) Bridges
A bridge is a hardware device for linking two networks that work with the same protocol.
Unlike a repeater, which works at the physical level, a bridge works at both the physical and
the logical levels (on layer 2 in the OSI model), which means that it can filter frames so that
it only lets past data whose destination address corresponds to a machine located on the
other side of the bridge.
How to configure a computer to work in a network.
1 . First attach the RJ-45 connector to the Ethernet network port on your PC.
2. Go to Start Button, Control Panel, Network and Internet and then Network and Sharing Center.
3. Click on Change Adapter Settings on the left panel which will display several network
connection icons e.g. Local Area Connection or Wireless Network Connection
4. Right click on the appropriate adapter, choose Properties to display Connection Properties
window.
5. For most LANs, select the Internet Protocol 4 (TCP/IPv4). Highlight the protocol and choose
Properties.
6. Select Obtain IP address and Obtain DNS Server Address both Automatically or enter the
settings manually by clicking the radio button for Use the Following IP Address and enter the IP
Address, Subnet Mask, and Default Gateway settings. You will also need to enter in your DNS
server addresses as well.
7. Click on Ok button to apply the settings.
NOTE: Internet protocol 6 (TCP/IPv6) is also available in Windows Vista/7.
Internet Protocol address (IP Addresses)
An Internet Protocol address (IP address) is a numerical label assigned to each device (e.g.,
computer, printer, router) participating in a computer network that uses the Internet Protocol for
communication. IP addresses are binary numbers, but they are usually stored in text files and
displayed in human-readable dotted decimal notations, such as 1 72.1 6.254.1
An IP address has two components, the network address and the host address. For example,
consider the IP address 1 50.21 5.01 7.009. Assuming this is part of a Class B network, the first two
numbers (1 50.21 5) represent the Class B network address, and the second two numbers (01 7.009)
identify a particular host/device on this network.
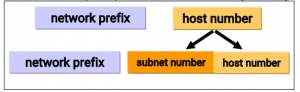
Subnetting
Organizations have multiple networks which are independently managed and each is allocate a
separate network address. Therefore, the host number portion of an IP address is split into a
subnet number and a (smaller) host number. This result is a 3-layer hierarchy
BASIC NETWORK COMMANDS
1 . Ping:
Ping sends an ECHO_REQUEST packet to the specified host. If the host responds, you get an
ICMP packet back which means the machine is up and connected to the network. You can
“ping” an IP address to see if a machine is alive. If there is no response, you know something is
wrong. E.g.
C:\>ping xxx.xxx.xxx.xxx e.g. ping 1 92.1 68.1 .1 0
Allows you to ping another computer (the x’s represent the IP address of the computer you are
attempting to ping). If this is not able to complete, this should relay back an unsuccessful message,
which could be an indication of cable issues, network card issues, hub issue, etc
C:\>ping localhost
Pings the local host, this will allow you to see if the computer is able to send information out and
receive the information back. Note that this does not send information over a network but may
allow you to see if the card is being seen.
2. IPCONFIG
Ipconfig displays the network settings currently assigned and given by a network such as IP
address, subnet mask and default gateway for each adapter bound to TCP/IP. This command can
be utilized to verify a network connection as well as to verify your network settings.
To get all local network information for your computer use the /all switch as shown below,
network prefix subnet number host number
network prefix host number
followed by the results that would be seen when using this command.
C:\>ipconfig /all
3. Pathping/Tracert
Pathping is designed for environments in which one or more routers exist between hosts. It sends
a series of packets to each router that’s in the path to the destination host in an effort to determine
whether the router is performing slowly or dropping packets.
E.g. pathping 1 92.1 68.1 .1 0
Example Results might be:
1 3ms 1 ms 1 ms 1 92.1 68.0.1 (to the router)
2 4ms 1 ms 1 ms 1 92.1 68.1 .1 0 (to the proxy server)
NETWORK TOPOLOGIES
The devices on a network are referred to as nodes. Nodes can be connected using any of the
various types of media, including twisted pair copper wire cable, optical fiber cable, coaxial cable
and radio waves. The nodes in a network can be arranged according to several basic topologies
(i.e., layouts).
A network topology can be physical or logical. Physical Topology is the actual layout of a network
and its connections. Logical Topology is the way in which data accesses the medium and packets
are transmitted/ travel.
Physical Topologies
There are several physical network topologies:
Star Topology
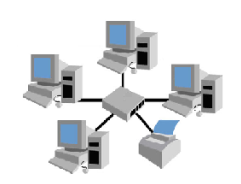
The most commonly used topology in LANs is the star topology. All the nodes in a star topology
are connected to a central device like a hub, a switch or a router with a point-to-point connection.
The hub acts as a signal repeater. The hub or switch manages and controls all functions of the
network. Star topologies can be implemented at home, offices or even in a building.
Advantages
The star topology is considered the easiest topology to design and implement.
The failure of a node or cable in a star network will not take down the entire network
as compared to the Bus topology.
Signals do not get transmitted to all the workstations if a switch is used and
therefore better performance.
It is also easier to monitor due to the centralized management. Centralization allows
inspection of the traffic through the network which makes detection of suspicious
behaviour on the network easy.
It is very easy to add additional nodes.
It is easy to troubleshoot (detect faults) and to remove parts.
Data is safer as the packets only move through three points; originator-central device destination.
Disadvantages
The network is highly dependent on the central connecting device. If the central
connecting device such as a hub, a switch or a router fails due to any reason, then
ultimately the whole network can come down or collapse.
As compared to the bus topology, a star network requires more devices & cables to
complete a network.
The performance as well as the number of nodes that can be added in such a
topology depends on the capacity of the central device.
Physical Bus Topology
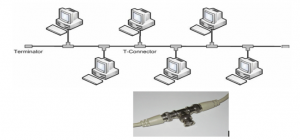
Bus topology uses a common backbone/trunk to connect all the network devices in a
network in a linear layout. A single cable functions as the shared communication medium
for all the devices attached to this cable with an interface connector or T-connector. The
device, which wants to communicate, sends the message/signal to all the devices attached
to the shared cable but only the intended recipient actually accepts the message. A
terminator is added at both ends of the central cable, to prevent bouncing of signals.
1 0Base-2 and 1 0BaseT are two popular types of the Ethernet cables used in the Bus
topology.
Advantages
Bus topologies are easy to implement
It is easy to extend the network
They are inexpensive to install and do not require much cabling.
Disadvantages
Bus networks work with very limited devices. Performance issues are likely to occur
in the Bus topology if more than 1 2-1 5 computers are added in a Bus Network.
Dependency on the central cable is risky. If the Backbone cable fails then the whole
network becomes useless and communication fails among all the computers.
It is difficult to detect faults at individual station and addition of new devices can be
difficult
Data can be transmitted only in one direction and is then destroyed when it reaches
the end of the line else it will lead to repetition.
Security is very low because all the computers receive the sent signal.
Because the bus network is just a collection of cable, connectors, and terminators,
there is no amplification of the signal as it travels on the wire. This means that the
size of the network will be limited by the maximum distance the cable type can
actually move the signal that holds the data.
Physical Tree Topology
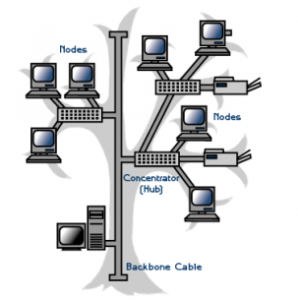
Tree topologies are comprised of multiple star topologies on a bus i.e. it is a bus/star hybrid
topology. Only the hub devices can connect directly with the tree bus and each hub functions as
the root of a tree for the network devices. The concentrator hub is a communications device
that multiplexes (combines) several signals for transmission over a single medium.
Advantages
This bus/star hybrid combination supports future expandability of the computer
networks, much better than a bus or star.
The fact that the network is divided into segments makes the network more manageable
hence easier fault identification and isolation (maintenance).
If one segment is damaged, other segments are not affected.
The hybrid system overcomes the limitations of both the star and the bus topology. It
doesn’t have the limitation of hub connection points that a star has and also does not
have the limitations of the broadcast traffic and overall dependency on a single bus of
the bus topology.
Disadvantages
Maintenance and management of the network may be an issue when the network spans
a great area.
Since it is a variation of the bus topology, if the backbone fails, the various star networks
will not be able to communicate
Mesh Topology
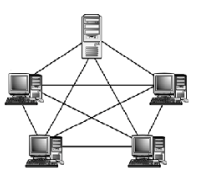
This is a type of network in which devices are connected with many redundant
interconnections between network nodes such as computers, routers and switches. Every
node not only sends its own signals but also relays data from other nodes i.e. must
collaborate to propagate the data in the network. Mesh topologies work on the concept of
routes. The message sent to the destination can take any possible, shortest, easiest route to
reach its destination. Mesh networks are typically wireless.
Routers work in finding the routes for the messages and in reaching them to their
destinations. The topology in which every device connects to every other device is called a
full Mesh topology unlike in a hybrid/partial mesh in which some nodes are connected to all
the others, but some of the nodes are connected only to those other nodes with which they
exchange the most data.
Advantages
A mesh network is reliable and offers redundancy. If one node can no longer operate,
all the rest can still communicate with each other, directly or through one or more
intermediate nodes.
The network can withstand high traffic and data can be transmitted from different
devices simultaneously.
Expansion and modification can be done without disrupting existing nodes.
Point-to-point connections make identification and isolation of faults easy.
Messages travel through a dedicated line, directly to the intended recipient and
therefore privacy and security are thus enhanced.
Disadvantages
It is expensive to implement due to the amount of cabling and the number of
hardware ports it will require in order to ensure the redundancy. It is therefore mostly
used in wireless networks.
Setup and maintenance is very difficult.
Physical Ring Topology
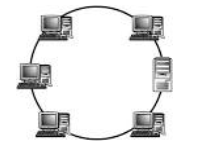
In a ring topology, all the nodes are connected to each other in such a way that they make a
closed loop/ring. Each workstation is connected to two other components on either side
and it communicates with these two adjacent neighbours. Data travels around the network
in one direction and sending and receiving of data takes place by the help of a Token. A
token contains a piece of information which is sent along with the data by the source
computer. Once a node receives a packet, it sends a confirmation to the source machine.
Each node gets to send data when it receives an empty token.
NB: Token Ring Networks
Advantages
The topology is very organized and eliminates chances of collision since only one
token is usually in circulation.
Additional nodes on the network do not affect the performance of the network.
Each computer has equal access to network resources.
It is easy to add devices to the network due to the point-to-point line configuration.
It is easy to identify and isolate faults due to the point-to-point line configuration.
Disadvantages
Each packet of data must pass through all the computers between source and
destination. It is therefore slower than a star topology.
If one workstation goes down, the entire network gets affected.
Logical Topologies
There are three logical topologies (bus, ring, and switching) which are usually implemented as a
physical star.
Logical Bus Topology
Modern Ethernet networks are Star Topologies (physically) but logically they are bus topologies.
The Hub is at the centre, and defines a Star Topology.
In any network, computers communicate by sending information across the media as a series of
signals. In a logical bus topology, the signals travel along the length of the cable in all directions
until they weaken enough so as not to be detectable or until they encounter a device that absorbs
them. This traveling across the medium is called signal propagation
When a computer has data to send, it addresses that data, breaks it into manageable chunks, and
sends it across the network as electronic signals
All computers on a logical bus receive them
Only the destination computer accepts the data
All users must share the available amount of transmission time, implying network
performance is reduced
Collisions are bound to occur since all nodes are sharing same bus.
Logical Ring Topology
Data in a logical ring topology travels from one computer to the next computer until the data
reaches its destination. Token passing is one method for sending data around a ring
Token is a small packet which passes around the ring to each computer in turn.
If a computer (sender) has packets to send, it modifies the token, adds address and data, and
sends it around the ring. The receiver returns an acknowledgement packet to the sender.
Upon receiving the acknowledgement packet, the sender releases the token and sends it around
the ring for another sender to use.
Logical ring can be implemented on a physical star. Modern logical ring topologies use smart hubs
that recognize a computer‘s failure and remove the computer from the ring automatically. One
advantage of the ring topology lies in its capability to share network resources fairly.
Switching
A switch takes a signal coming from a device connected and builds a circuit on the fly to forward
the signal to the intended destination computer
Switching is superior to other logical topologies because unlike bus and ring, multiple computers
can communicate simultaneously without affecting each other. Switching is the dominant logical
topology in LAN design.
NB: Advantages and disadvantages of a certain topology depend on the following factors:
Ease of management, Performance, Troubleshooting (maintenance), ease of design and
implementation, safety of data, cost , expandability and robustness.
NB: The BASE is for baseband operation. Baseband is an adjective that describes signals and
systems whose range of frequencies is measured from close to 0 hertz to a cut-off frequency (a
maximum bandwidth or highest signal frequency); it is sometimes used as a noun for a band of
frequencies starting close to zero.
INTERNET AND WORLD WIDE WEB
Specific Objectives:
By the end of this topic, the trainee should be able to:
a) Define the Internet
b) Explain the applications of the Internet
c) Explain the challenges in the use of the Internet in the business environment
d) Explain the need for Internet security
e) Open the browser
f) Surf the net
g) Create e-mail accounts
h) Use e-mail
i) Use search engines
j) Print documents
Task 1 Defining the Internet and applications
Definition of the Internet
The Internet is a global system of interconnected computer networks that use the standard
Internet Protocol Suite (TCP/IP) to serve billions of users worldwide. It is a network of networks
that consists of millions of private and public, academic, business, and government networks of
local to global scope that are linked by a broad array of electronic and optical networking
technologies. The Internet carries a vast array of information resources and services, most notably
the inter-linked hypertext documents of the World Wide Web (WWW) and the infrastructure to
support electronic mail.
History of the Internet
In the 1 960s, one of MIT’s projects Mac was funded by ARPA (Advanced Research Projects Agency)
of the department of defense. During one of its conferences, ARPA rolled out the blueprints for
networking the main computers of about a dozen ARPA-funded universities institutions. They were
to be connected with communication lines at then-stunning 56 Kbps. Shortly after the conference,
ARPA proceeded to implement the ARPAnet, the predecessor of today’s Internet.
Things worked out differently from what was originally planned. Rather than the primary benefit of
researchers sharing each other’s computer, it rapidly became clear that enabling the researchers to
communicate among themselves via electronic mail (e-mail) was the key benefit of ARPAnet. One
of the primary goals for ARPAnet was to allow multiple users to send and receive information
simultaneously over the same communication paths. The network operated with a technique called
packet switching, in which digital data was sent in small packages called packets. The packets
contained data addresses, error control and sequencing information. The address information
allowed packets to be routed to destinations. The sequencing information helped reassemble the
packets into their original order for presentation to the recipient since they could arrive out of order.
The protocols for communicating over the ARPAnet became known as TCP (Transmission Control
Protocol). TCP ensured that messages were properly routed from sender to receiver and that those
messages arrived intact. As the internet evolved, organizations worldwide were implementing their
own networks for both intra-organization and inter-organization communications. A wide variety of
networking hardware and software appeared. One challenge was to get these networks to
communicate. ARPA accomplished this with the development of IP – the Internetworking Protocol,
truly creating a network of networks, the current architecture of the Internet. The combined set of
protocols is now referred to as TCP/IP.
The history of the TCP/IP protocol suite can be traced back to one of the first WANs consisting of
computers from different manufacturers running different operating systems. Before ARPAnet,
most computer networks were homogeneous, consisting of computers from the same hardware
manufacturer running the same operating system.
The ARPAnet’s popularity became apparent, and in 1 975, it was converted from an experimental
research network into a fully operational network. Research into network protocols continued and
the Internet Protocol Suite resulted. The TCP/IP protocols were adopted as Military Standards in
1 983, and all computers connected to the ARPAnet were required to adopt the new protocol. The
ARPAnet was then split into two networks: the MILNET, used for military communications, and the
new, much smaller ARPAnet, used for further research. MILnet and ARPAnet together became
known as the Internet. Initially, Internet use was limited to the universities, research institutions and
the military, but eventually with time Internet has incorporated commercial applications.
The term internet (notice the lower case i) is now used to refer to any collection of physically
separate networks that share the same communication protocols (not necessarily TCP/IP) to
appear as a single logical network. The term Internet (notice the upper case I) is used to refer to
the worldwide collection of interconnected computer networks that run the TCP/IP protocols.
Internetworking evolved as a solution to three key problems which are as follows:
| i) | Isolated LANs It made electronic communication between different offices or departments impossible. |
ii) Duplication of Resources
The same hardware and software had to be supplied to each office or department, as did
separate support staff.
iii) Lack of Network Management
No centralized method of managing and troubleshooting networks existed.
Web related terminologies
• Web browsers
Web browsers are software applications that are used to retrieve web pages from the Internet onto
your PC. They let you surf (or browse) through information on the Web. Information on the Web is
structured into pages. Each page has a specific address that is used to locate and access
information on that page.
The three browsers that particularly dominate the Internet market are:
– Microsoft’s Internet Explorer
– Mozilla Firefox
– Netscape’s Navigator
• Modem (Modulator / Demodulator)
On the Internet, computers exchange information via telephone lines. A modem is a device that
enables you to connect to the Internet and access information. As a transmitting modem, it
translates computer information into a form that can transmit over telephone lines (this is the
process of modulation).
As a receiving modem, it translates the information in a form that your computer can understand
(this is the process of demodulation).
A fast modem is essential. It will reduce the amount of time spent waiting for web pages, files, or
messages from the Internet. Modem speeds are quoted in ‘bps’ (bits per second).
Typical speeds are 9600 bps, 4.4 Kbps (Kilobits per second), 28.8
Kbps, 56 Kbps, etc.
• Internet Service Provider (ISP)
This is a commercial organization that provides Internet connections, along with a set of support
services for a fee.
Most people and organizations get a connection to the Internet over a telephone line through an
ISP, though some larger businesses and institutions (such as universities) have their own internet
connections.
An ISP will usually have a number of host computers. These hosts will typically provide storage
space for electronic mail messages for their users, users’ own web sites and a set of related
facilities such as advice, support software and appropriate security.
Examples of local ISPs include Africa Online, Kenya Web, ISP Kenya, Swift Kenya and Inter-Connect.
When you open an account with an ISP you will be provided with a user name and a password:
Username – Every time you get connected, you require a name to identify yourself on the Internet.
Password – This is needed for security purposes. This ensures that your Internet account is secure.
NB: ISPs charge for the services rendered.
The World Wide Web
The World Wide Web is also known as the Web, WWW or W3. The Web is a part of the Internet.
The WWW is a collection of hyperlinked web pages published on the Internet. This huge collection
of documents is stored on computers, called hosts, around the world. The documents may contain
text, pictures, sounds, small programs or forms to be completed by a user.
Web Page
Web pages are documents published by organizations and individuals interested in putting
themselves on the Web. Web pages can include text, pictures, sound and video.
Each web page has an address on the Internet. This address is called a Uniform Resource Locator
(URL). Web pages are created using Hypertext Markup Language.
Web Site
A collection of web pages belonging to an organization or individual is called a website. These
organizations or individuals maintain the website.
Hyperlinks
All web pages have hyperlinks. These links connect:
1 : One web page to another part of the same web page. This is useful if it is a really large
page.
2: One web page to another website somewhere on the Web.
3: A page to a file, such as a sound clip, video, a spreadsheet or a Word document.
These links to other pages can be links to objects stored anywhere on the Internet. Hypertext links
are indicated by underlined text highlighted in blue (usually).
Hyperlinks are also represented by buttons, graphics or pictures.
An example of hyperlinks
To find hyperlinks on a page, move your mouse pointer over the page and where there is a
hyperlink the mouse pointer will change into a hand with a pointing finger.
As you surf around the web, Internet Explorer stores the sites and pages that you visit. You will
notice that the hyperlinks you previously selected are colored differently. Internet Explorer does this
to remind you that you have already visited the page identified by this link.
Web Hosting
A World Wide Web server is a computer with programs that answer requests for documents from
clients (browsers) over the Internet. Files containing web sites are placed on these servers also
known as host computers. A host computer is any computer connected to the Internet and has
stored information that has been made available to the Web.
Home Page
The Home page is the web page loaded when Internet Explorer is first started i.e. when you access
the Web. You can set any web page as your home page.
The home page is also the first page of a company or an individual’s website on the Web.
Note: Do not confuse your home page with the home page of the websites you visit. Your home
page is set through Internet Explorer.
The home page of a website is the introductory page for the site.
If you click a hyperlink such as Home on a web page, you will jump to the website’s home page, not
yours.
To access your home page, click the Home button on the Explorer toolbar.
Web Address (Uniform Resource Locator (URL))
Each web page has a unique address or location, called the Uniform Resource Locator (URL).
You can instantly display any Web page if you know its URL. For example, http://www.compaq.com
You can include wildcards in a URL in cases when you may not know the full path. For example:
http://www.mars.superlink.net/~zorro/humor.com
The wild card (~) is used to represent character(s). In the above example, sites that have Azorro,
Thezorro etc instead of ~Zorro will be displayed.
A wrongly entered character can result in an invalid URL, e.g. a comma instead of a full stop or a
dash instead of an underscore.
Search Engines/Search Services.
A search engine is software that helps you locate information in the Web. There are several search
engines such as Google search engine, Yahoo, Infoseek, Lycos, Web Crawler, and Excite that offer
different kinds of searching capabilities.
Spam
Unwanted internet mail and ads.
Applications of the Internet
Once you’re connected to the Internet, there are limitless possibilities. You can send messages to
users in other countries, join a chat group, or try out new games. Some of the services offered on
the Internet include the following:
1 . Electronic Mail (e-mail)
Email is a system for transmitting messages between computers. Exchanging electronic
mail is the most popular feature on the Internet. With Internet email you can send messages
to people all over the world including friends, customers and even people you meet on the
Internet. Electronic mail is faster than ordinary mail, easy to manage, inexpensive and saves
paper.
2. Information
The Internet gives you information on virtually any subject. This is because of the World
Wide Web. The World Wide Web (www) is a global system of linked web pages containing
information – text, pictures, sound and video.
You can review newspapers, magazines, academic papers and much more. Governments,
colleges, universities, companies and individuals all offer free information on the Internet.
For example, you can inquire about universities in Britain or America.
3. Programs
Thousands of programs are available on the Internet. These programs include word
processors, spreadsheets, electronic cards and much more. You can look for the latest
software over the Internet. For example, you can get the latest Anti-Virus software available
and in addition, retrieve a free trial issue.
4. Entertainment
Hundreds of simple games are available on the Internet, including racing cars, chess, poker,
football and much more. The Internet also lets you review current movies and hear television
theme songs.
5. Discussion Groups (Chat groups/Rooms)
You can join discussion groups on the Internet and meet people around the world with
similar interests. IRC (Internet Relay Chat) is a chatting system on the Internet that lets you
chat privately or in groups. You can ask questions, discuss problems and read interesting
stories. There are many discussion groups on various topics.
6. Online Shopping/trading and advertising
You can order goods and services on the Internet without leaving your desk. For example,
you can view a catalogue of a certain clothes shop over the Internet and fill in an online
order form.
7. Newsgroups
These are discussions on a range of topics from recreational activities to scientific research.
Any Internet surfer can access some of these newsgroups, while others will need
subscription. You can read any articles or write articles and post them.
8. Social Networking
By far the most popular and fastest growing communication method made possible by
broadband Internet service, social networking started out as a way for people to find old
friends, stay in touch with current ones, and meet new ones. It has now grown into a prolific
communication tool for both personal and business use. You can organize groups, notify
people of events, send mass email messages, chat, and so much more. Facebook, Twitter,
and MySpace are currently the most popular social networking sites, and have attracted
billions of users. Many businesses have used social networking for advertising and
marketing purposes and seen great results.
9. As a research tool
To learn about new developments or products, competitors, market news and customer
opinions.
The challenges in the use of the Internet in a business environment
Explaining the need for Internet security
With the number of businesses that are connecting to the Internet and using cable modems, DSL
lines, and T1 circuits, the need to secure their connections is not only necessary but also simply
due diligence on the part of the company. Businesses rely on their Internet connection to send
credit card payments through, to run their VoIP phones, and even to host their webpage. If Internet
connectivity is disrupted then business can not operate as usual.
In order to insure that the connection to the Internet is secure there are some basic methods that
can be utilized that are fairly cheap and will more than pay for themselves with the increased
security and uptime of the Internet connection. A business does not need to make sure their
network is as tight as an Army base; they just need to make sure they are more secure than others
so that attackers will target the easier sites and leave theirs alone.
The very first thing that needs to be put in place at each and every Internet connection is a firewall.
All businesses should have a hardware firewall that protects and separates their business from the
Internet. A cable modem with built-in firewall may be adequate for a household, but a business
should look at a commercially available firewall such as a Juniper firewall 5 series, a SonicWall
firewall, or even a Cisco SOHO. These are all inexpensive and are easy to manage and configure. A
firewall is the first step of protection that keeps out those who do not need to have access to the
internal business network. Essentially installing a firewall is similar to installing locks on a house.
Only those with the proper keys can access the house just as only those who have been
specifically granted access can access the network behind the firewall.
Once a firewall has been installed, configured, and is working properly a business is going to want
to look at the computers themselves. There are two things that need to be done on all the
machines that will insure that the machines stay up and operational longer than those that are left
unprotected. The two things are necessary are: patching the machines for the latest updates for
both the operating system (OS) and the applications, and then installing antivirus software.
The patching of the systems will insure that the vulnerabilities that virus/worm writers are using to
exploit and take over machines will not be effective against a patched machine. By patching the
machine the entry door is closed and the worm will not be able to gain access. Application patches
update their tools and software being used on the machine. With the latest patches this too will
make it more difficult for attackers to exploit machines and gain entry to them.
Antivirus software is an absolute necessity on machines. System administrators and users can
become annoyed with it as it is a resource hog but that is because the software is tasked with
protecting the system and they continually scan the system for infections. When used in “real-time”
mode each file is scanned before downloading, uploading, or being saved to the disk. This is
important when reading emails, sending emails, or even surfing on the Internet.
There are many other steps that can be taken to give a business a stricter security posture.
However, by taking the above steps a business can rest assured that they have taken the due
diligence and installed the most basic security measures in their business that will make it difficult
for an attacker to gain unauthorized access to a business’s network.
Task 4 Opening the browser and surfing the internet
There are several ways to start Internet Explorer.
1 . To start Internet Explorer from the Windows desktop, double-click the Internet
Explorer icon.
OR
1 . On the Windows taskbar, click Start.
2. Select the Programs menu item.
3. From the submenu displayed, select Internet Explorer from the Internet Explorer group.
You may be required to make a connection through your ISP in order to log on to the Internet.
4. Click in the User name: box and enter your user name.
| 5. | Type in your password in the Password box. The password appears in asterisk format (*) for added privacy and security. |
6. Click Connect to access the Internet.
Note: The Dial-up Connection dialog box will not be displayed if you are connected to the ISP
via a proxy server. A proxy server allows several users to access the Internet account using
a single account.
Upon successful logging on, the Internet Explorer displays the ‘home page’ and a Connection
Indicator appears on the Taskbar to indicate that you are online.
NB: All the time you are connected, you incur a local telephone charge to the local phone company
and access time to the ISP.
Connection indicator
You can find out at what speed you are receiving data, how much time you have spent online etc.,
by double-clicking the Connection Indicator.
Other browsers have a similar procedure for opening.
CUSTOMIZING THE WEB BROWSER.
Purpose.
Moving from site to site can be slow if the ISP or Internet lines are busy, if the host server (the
server storing the site you are trying to access) is busy or if you are using a slow modem.
The volume of traffic is also growing on the Internet and so web designers are constantly looking
for ways in which they can make their pages load faster.
If a site contains graphics (or other multimedia content like video, audio etc) you can prevent the
1 26
graphics from downloading so as to speed up browsing.
Step-by-Step.
1 . From the View menu, select Internet Options….
2. Click the Advanced tab.
3. Scroll down to the Multimedia section.
4. Deselect the options or content that you want turned off e.g Show
Pictures, Play Animations or Play Videos.
5. Click OK.
NB: If the Show pictures check box is cleared, you can still view an individual picture on a
web page by right-clicking its icon and then clicking Show Picture.
Information and Communication
ELECTRONIC MAIL (E-MAIL)
One of the common services provided by the Internet is electronic mail, also known as e-mail. This
is a worldwide system for sending and receiving electronic messages from one computer to
another.
E-mail is a much faster, economical and convenient way of sending messages to family, friends
and colleagues than the old fashioned mail called “snail mail”. With “snail mail” a message or letter
is sent to the recipient through the post office and takes days or weeks before reaching the
destination. An e-mail message can travel around the world in minutes.
For one to be able to communicate using email, the following components are needed:
1 . A computer where you will send or receive the e-mail messages.
2. Your e-mail address and that of the receiver.
3. An ISP company who will deliver your message to the receiver.
4. An e-mail program that lets you send, receive and manage your e-mail messages, e.g.
Microsoft Outlook, Outlook Express, Lotus Notes, Eudora.
Once you send a letter, it travels from your computer, through a modem, which connects your
computer to the Internet via the telephone network. The mail travels through various computers,
1 27
until it reaches the final destination.
Components of an e-mail address:
An e-mail address consists of two parts separated by the @ symbol.
If your e-mail address is drg@tropicalheat.com:
i) The first part refers to the person’s identity or log-in name, e.g.
“drg”
ii) The second part following the “@” symbol is usually made up of
two to three sub-parts to further identify the individual,
organization or ISP. In this case:
• ‘Tropical heat’ identifies the business.
• ‘. com’ is the extension and this identifies the type of the
organization.
The table below shows some extensions and what they represent: –
Extension Represents
| .org .edu .ac |
non-profit making organization an educational institution/organization an academic institution |
| .com a commercial organization | |
| .net .mil .gov |
network military government |
Sometimes the name of the country is included in the e-mail address
e.g. skynews@sky.co.uk or nation@africaonline.co.ke. Here ‘.co.uk’ refers to a company in the
United Kingdom whilst ‘.co.ke’ refers to one in Kenya.
Examples of E-mail Addresses:
Smith@compuserve.com
Iat@africaonline.co.ke
Were@ku.ac.ke
Hr-manager@kplc.org
Bridge@arcc.or.ke
Tim@yahoo.com (free e-mail address)
Douglas@hotmail.com (free e-mail address)
Advantages of emails over Traditional Paper-Based Mail
Emails are fast. They are delivered at once around the world. No other form of written
communication is as fast as an email.
When you reply to an email you can attach the original message so that when you answer
the recipient knows what you are talking about. This is important if you get hundreds of
emails a day.
It is possible to send automated emails with a certain text. In such a way it is possible to tell
the sender that you are on vacation. These emails are called auto responders.
Emails are easy to use. You can organize your daily correspondence, send and receive
electronic messages and save them on computers.
Emails do not use paper. They are environment friendly and save a lot of trees from being
cut down.
Emails can also have pictures in them. You can send birthday cards or newsletters as emails.
Products can be advertised with emails. Companies can reach a lot of people and inform
them in a short time.
It is possible to tell whether an email has been delivered or not.
Disadvantages of emails
Emails may carry viruses. These are small programs that harm your computer system. They
can read out your email address book and send themselves to a number of people around
the world.
Many people send unwanted emails to others. These are called spam mails. It takes a lot of
time to filter out the unwanted emails from those that are really important.
Emails cannot really be used for official business documents. They may be lost and you
cannot sign them.
Your mailbox may get flooded with emails after a certain time so you have to empty it from
time to time.
EMAIL SYSTEMS
1 . POP3
Its full name is Post Office Protocol 3. With a POP3 email service, email messages are downloaded
to the computer and then usually deleted from the central email server.
If one uses POP3 to receive business email, they are usually restricted to using one computer for
the email. (Each person can have their own email account, but everyone will be restricted to their
own computer.)
Most email addresses that come as part of the internet connection package are POP3 accounts.
2. IMAP
IMAP stands for Internet Message Access Protocol. It’s an alternative to POP3 which keeps
messages stored on a central business email server, along with information about whether each
message has been read or replied to.
With IMAP, you can log in from any computer and see your whole inbox, complete with the status
of messages – so you can see which you’ve read, which you’ve replied to, and so on.
IMAP is a good way to add extra flexibility to your business email. It’s a well-established technology
and you’ll find many entry-level email services (like those from web hosting companies) will include
IMAP as standard.
3. Microsoft Exchange
The majority of companies use Exchange Server to store email and Outlook as the client. Like
IMAP, Exchange stores messages centrally, so you can log in from different places. But it also
offers lots of extra functions, including centrally stored calendars, task and contact lists.
Exchange and Outlook integrate well with Windows, but make less sense in a mixed environment
1 29
with many Apple desktops and iPhone / Android mobile users. Often used to create a closed email
environment out of security concerns, where it can be hard to get your email to outside systems.
4. Webmail or HTTP
As the name suggests, webmail services require you to use a web browser (like Internet Explorer or
Firefox) to log in and access your business email. Some people call them HTTP email services.
Many free business email services – including Hotmail, Yahoo Mail and Google Mail – are webmail
services.
To send or receive email, you visit a specific website and log in with your username and password.
Webmail is convenient because you can log in from anywhere. However, it’s useless unless you’re
connected to the internet, meaning most companies prefer to use another business email service
which also offers webmail as an option.
For instance, Microsoft Exchange includes a webmail interface, so you can check your business
email if you’re not at your own computer. So do many of the IMAP and POP3-based services
available.
Reading e-mail messages.
Once an e-mail message that has been sent to you arrives at your computer, to read the contents
you must open it using the program you have installed for sending e-mail, e.g. Microsoft Outlook.
Step-by-Step.
1 . Launch the e-mail program Microsoft Outlook from the Start menu or a shortcut on the
desktop.
2. Enter the password if prompted and click OK.
Alternatively, you may need to select your profile from the Choose
Profile dialog box that appears.
3. In this case, select your profile by clicking the down arrow key of the Profile Name dialog
box and click OK.
NB: A User Profile is a group of settings that define how Outlook is set up for a particular
user. It also defines through the information services how a user can send, store, and
receive messages.
4. The Inbox is where all incoming messages are stored when you connect to Outlook.
Displayed are the e-mail messages that you have received.
Unopened mail
Opened mail
A list of e-mail messages
5. To open and read e-mail messages in the Inbox, choose the message that you want to read.
Then, double click on it to open it.
Message
The lower grid of your screen will have the full message. As you read the items in your Inbox,
you can reply to, forward, or file them in other folders that you create.
When you have finished reading a message, you can close the window by selecting the File
menu, then choosing Close. This will take you back to the Outlook window.
When you do not need to use any other e-mail services, you can exit the Outlook program by
selecting the File menu, then choosing Close.
If there are any e-mail messages in the Outbox that have not been sent, a message will
appear prompting you to send the e-mail(s) at that particular time or you can choose to send
it later.
Reply to e-mail messages.
If you have read a message, you may want to send a reply to the original sender.
If the original message that you are replying to was also copied to a number of other people, you
may want to send a reply to all of them.
Step-by-Step.
When replying to a mail message, you can choose to reply with or without the original message
insertion. The original message, sometimes referred to as the history, appears in the body of the
message. This is just for reference purposes and can be removed by selecting the text and
pressing the Delete key or setting options in the
Options dialog box.
Reply and include the original message
1 . If the message you want to reply is not open, select it and open it.
2. Click the Reply button in the Mail window. The Reply message window appears. This window
contains the message you are replying to at the bottom.
The Reply button
History/Original
Message part
3. Type the reply where the insertion point is.
4. When you have finished typing and editing the reply, click the Send button if you are on-line to
send the message. Send button
NB: If you click the Send button while you are offline, the mail will be placed in the Outbox folder
and will automatically be sent the moment you go online.
Reply without including the original message
1 . From the Tools menu, click Options.
2. Click the Preferences tab, and then click Email Options.3. In the On replies and forwards section,
click the down arrow key under When replying to a message box.
4. Select Do not include original message.
5. Click OK.
6. Open the mail message you want to reply to.
Information and Communication Page 45
7. Click the Reply button in the Mail window. The Reply message window appears. This
window does not contain the message you are replying to at the bottom.
8. Type the reply where the insertion point is.
9. When you have finished typing and editing the reply, click the Send button.
Notes:
Working Off-line Connection to the Internet usually means that you are using telephone lines, and
therefore incurring telephone charges and usage on your ISP account. Once you have launched the
Mail program, it is not necessary for you to be connected directly so that you can read and write
your e-mail messages. You may choose to work offline to save on costs and when you are ready to
send your messages you can connect and send them all at once.
1 . On the Task bar, click on the Status button.
2. Choose Disconnect.
Connection Indicator
3. The Connection Indicator disappears from the Taskbar showing that you are now working offline. Some services like Internet, Usenet, newsroom, or shopping will not be available when you are
off-line.
To use these services, you need to re-establish the connection.
Sending an e-mail message.
1 . To communicate with another user who has an e-mail address. This is cheaper than sending fax
or using the telephone especially for long distance calls.
2. It is also faster to send e-mail than to post a letter.
For example, to send a letter around the world using e-mail is just a matter of minutes as
compared to the weeks ordinary mail takes.
For this reason, most Internet users refer to ordinary mail as ‘snail mail’.
Step-by-Step.
1 . From the Outlook window, click the New Mail Message button.
The New Mail Message button
The message composition window is displayed:
Subject box
Message area
2. In the To… box, type the e-mail address (or select one from the address book by
clicking on the To… button) of the recipient of your e-mail.
3. If you want copies of the message to be sent to other people, type in their e-mail
addresses in the Cc… box. Be sure to separate each address with a semi-colon.
You can also send a Blind Carbon Copy (Bcc). Here, the recipients entered receive the
message but their names are hidden from other recipients of the message. To add a Bcc
field, click the View menu and select Bcc field.
Cc: stands for “carbon copy”. Anyone listed in the Cc: field of a message will receive a copy
of that message when you send it. All other recipients of that message will be able to see
that the person you designated as a Cc: recipient has received a copy of the message. The
Cc: field is useful in instances when you wish to share a message with someone but are not
requesting that they reply or take any direct action in response.
Bcc: stands for “blind carbon copy”. This is similar to the Cc: feature, except that Bcc:
recipients are invisible to all of the other recipients of the message (including other Bcc:
recipients). For example, if you send a message To: johndoe@yahoo.com and Bcc:
janedoe@yahoo.com, then johndoe will see himself as the message’s only recipient, while
janedoe will see that you have also sent the message to johndoe. The Bcc: field is useful in
instances when you don’t wish to share your recipients’ email addresses with everyone who
receives your message.
To send a message, you must always specify at least one recipient in the To: field. If you
don’t, an error message will appear when you attempt to send the message.
4. Type the subject or topic in the Subject box.
5. In the lower grid of the message composition window, type in the message that you want
to send as seen in the illustration above.
You can format the email message using the formatting tools like
Bold, Font size, Underline etc.
When you have finished typing the message, editing, and spellchecked it, click the Send button.
NB: A message that returns to the sender because it cannot reach its destination is referred to as a
bounced message.
To display the Formatting toolbar
If the formatting toolbar is not visible, you will need to display it.
1 . Click the View menu from the menu bar, highlight Toolbars then click the Formatting option.
Formatting toolbar
• You can add Smiley/Smilies to your messages. These are special symbols used to express
emotions in messages. These characters resemble human faces if you turn them sideways as
shown in the table below:
Smiley Represents
: `-(Cry
🙁 Frown
:-I Indifferent
😮 Surprise
🙂 Smile
Spell-Checking Mail Messages.
Before sending a mail message you can spell check it to correct any spelling mistakes in the mail.
1 . From the Tools menu click Spelling.
2. The Spelling dialog box appears as shown below. The misspell words are highlighted and shown
in this dialog box. Choose the correct word
by selecting it and clicking the Change button.
3. If the word or phrase is correct but is not in the dictionary, click
Ignore.
4. Once the spell check is complete, click OK.
Set up view options.
To make the Microsoft Outlook screen comfortable and convenient to your individual preferences.
For example, if you usually receive a lot of mail you may prefer to see the mail grouped by sender’s
name, or you can preview the contents of an e-mail message before opening it.
Step-by-Step.
1 . Load Microsoft Outlook.
2. From the View menu highlight Current View.
The submenu displays the various view options that can be selected:
3. As an example, highlight the By Sender option and click.
Grouped messages
4. The mail messages are then grouped by the sender. To display the contents of a group click the
plus button of the group.
To remove folder listing.
The folder list is displayed by default. However if you do not want to view the folder list you can
remove it, by selecting Folder List from the View menu.
To redisplay the folder list, repeat the same step outlined above.
Using the Address Book.
The Address Book is a directory of personal details, including email
addresses, for the people to whom you send messages (called contacts).
You can store such addresses in the Address Book so as to address mail more easily i.e. each time
you want to send email messages you simply select the names from the list of addresses.
This will save the time used to enter lists of email addresses as well as help maintain their
accuracy.
For example, the email address ‘njiiri.mworia@mit.edu.uk’ can be
difficult to remember. Besides, one can easily make a typing error
when typing it in. If you store this address accurately in the Address
Book then you will not worry about remembering it or typing it wrongly.
Step-by-Step.
To Add a Contact to the Address Book
1 . To open the Address Book, click on the Address Book button.
Address Book button
There may be several types of address books in the Address Book dialog box including
the Personal Address Book and other Address
Books created by the administrator.
2. Select the type of address book that you want to use in the Show names from the:
box.
The Personal Address Book is the address book used to store personal distribution lists you
frequently address messages to, such as a list of your friends.
The Global Address List (or other listed address books) is the address book that contains
all e-mail addresses for users, groups, and distribution lists in your organization that you can
address messages to. It is the network administrator who creates and maintains this
address book.
3. Click on the New Entry button.
New Entry button
4. Specify the entry type of the contact i.e. whether it is a Private
Address Book Mail Recipient or an entry for a Distribution List.
5. Type in the names for the contact as well as the full email address.
6. Complete the dialog box with the rest of the contact details using
the other tabs e.g. Work or Home information.
7. Click on OK.
The contact or address is added to the Address Book.
To Edit a Contact in the Address Book
You may want to edit a contact’s details. You can do this from the
Address Book.
1 . Open the Address Book.
2. Select the contact that you want to edit.
3. From the File menu, select Properties.
4. Make the necessary changes to the information and click OK.
To Create a Contact from a Mail Message
When you receive a mail message, you can add the sender’s details (name and email address) to
your Address Book in these steps.
1 . Open the e-mail message that contains the name you want to add to your contact list.
2. In the From field, right-click the name you want to make into a contact, and then click Add to
Contacts on the shortcut menu.
Or from the shortcut menu, select Add sender to Address
Book.
To Delete a Contact from the Address Book
1 . Open the Address Book and select the address that you want to remove.
2. Click on the Delete button.
Delete button
3. Click Yes to confirm that you want to delete the name or entry.
To Create a Distribution List
If you send mail to the same group of people frequently, you can create
a group address list. When you address a message to that group, each individual in the group
receives it. Group address lists are known as distribution lists.
You must have a Personal Address Book set up in order to be able to create a personal distribution
list.
1 . On the File menu, point to New, and then click Distribution List.
2. In the Name box, type a name.
The distribution list is saved in your Contacts folder by the name you give it.
3. Click Select Members.
In the Show names from the list, click the address book that contains the e-mail addresses
you want in your distribution list.
4. In the Type name or select from list box, type a name you want to include. In the list
below, select the name, and then click Add.
To add members who are not on the address books, click on Add
New and type in the details and click OK.
The list of members in the distribution list is displayed.
5. Click on Save and Close to exit.
There is another method of creating a distribution list. In this method, you use the New Entry
button.
6. Then select the entry type box, click Private Address Book
Distribution List and then click OK.
7. In the Distribution List Name box, type a name for the group and click OK.
The limitation with this method is that you have to involve the administrator when adding
names to the group.
8. Once this is done, the contact is copied to the Private Address Book
Distribution List box.
Repeat this process until you have all the names you want in your group in the Personal
Distribution List.
9. Click OK.
The group or distribution list is now listed in the Address Book.
A group icon showing a distribution list
To Send a Message using the Address Book or Distribution List
1 . In Outlook, select the New Mail Message option from the File menu.
2. Click on the To… button to open the Address Book.
3. Select the contact names from the list or select the distribution list and click on To ->.
NB: To see the full email addresses select the name of the person from the list and click on
Properties button.
4. Click OK to return back to the Message Composition dialog box.
5. Type out the rest of the message and click on Send.
Attaching files to email messages.
You can attach any type of file such as a document, spreadsheet, graphic image or presentation to
your email messages.
When you attach a file, you’re actually attaching a copy of the file, so the original is not affected.
Step-by-Step.
1 . Click the New Message button.
2. In the Message Composition dialog box enter the email address and type in the
message to be sent. Then click where you want the file attachment to appear.
3. Click on the Insert File button.
Insert File button
4. The Insert File dialog box is displayed. Locate the file’s folder and then select the file.
You can select multiple files by pressing the
CTRL key while clicking once on the file names.
However, when attaching several files take care not to attach too many large files or they
will take a long time to send and receive.
5. Click OK.
The attached file is displayed as an icon in the body of the message.
The icon indicates the file type and name. For example, shown below is an icon for an Excel
workbook file attachment:
6. Click on Send.
To Open or View an Attachment
Documents that contain file attachments display a paper clip image in the
view or folder next to the document title.
Once the document is open, Outlook displays an icon representing the attachment.
1 . In the Inbox, select the message that contains the attachment and open it.
2. Double-click the icon that represents the attachment.
You must have the application in which the attachment was composed in order to open it. The
MIME (Multipurpose Internet Mail Extension) type of file enables Internet browsers to access an
Internet mail file without prompting the user to specify the program used to create the attached file.
As a precaution, do not open file attachments unless you are sure you know where they came from.
There have been several cases of entire hard disks getting damaged due to viruses sent via e-mails.
Examples of email viruses are ‘Melissa’, ‘Bugbear’, ’Sasser’ etc.
Deleting an Attachment
1 . Open the message that has the attachment you want to delete.
2. Select the file (attachment) icon and press the Delete key.
Organizing e-mail messages.
You can use Outlook to organize your incoming messages and make it easy to send mail.
There are some messages that you would like to keep for future reference. Instead of letting them
clutter the Inbox, you can make them easier to find by storing them in folders you create.
Step-by-Step.
Organizing the Inbox
You can organize the messages in your Inbox quickly by sorting them.
To quickly sort messages by subject, sender or the date received, click on the respective column
header.
For example, to sort your messages in alphabetical order by sender, you can click on From in the
column header.
To Create a Mail Folder
1 . From the File menu, choose New then Folder.
2. Enter the name of the folder in the Name box, e.g. Personal Stuff.
3. Select the Inbox folder so that the mail folder created will become a subfolder of the
Inbox.
4. Click OK.
To Move Messages
1 . Select the message(s) you want to move.
2. Using the drag and drop method move the mail into the new folder created.
3. In the pop-up menu, select Move.
OR
From the Edit menu, select the Move to Folder option then select the folder you want to move the
message to.
4. Click OK.
Task 6 Using search engines
SEARCHING THE WEB.
1 . If you want to get some information concerning an area or subject of interest over the Web but
you do not know where to find it, you can use a search engine or service to locate sites that contain
that information.
2. Locate particular information in a web site, e.g. you can load a web site like
http://www.cnn.com/ and wish to read the sports news.
You can use a search engine within that site to locate information on sports.
How Search Engines find Web Pages.
Hundreds of thousands of new web pages are created each day, it is almost impossible for a
search engine to catalog every new page on the
Web. There are two ways that search engines use to locate web pages:
a) Spiders / Robots
Automated robots called spiders travel around the Web looking for new pages, creating links to
them.
b) Submissions
These are derived from people who have created new web pages and then submit information
about pages they have created.
Step-by-Step.
1 . Select a search engine, e.g. Yahoo, and type its address in the Address box, i.e.
http://www.yahoo.com. Once the search engine home page appears, type a keyword
or phrase in the Search box, e.g. Kenya, then click the Search button. The steps may
vary depending on the search engine you are using.
2. As soon as the search is completed, you will be presented with a list of sites that
contain the keyword or phrase you are looking for. Select a site whose description
comes closest to the information you desire and click on its link.
3. If there are many sites, not all links will be displayed. However there will be an option
that allows you to view the next 1 0 or so matches. Click on this if necessary to view
the next set of links. Information and Communication Page 24
NB: If there are too many matches you may want to use an additional keyword to
narrow down the search. Type the additional key word in the search box e.g. “Kenya
AND Economy” to narrow down to sites that contain information about the economy
in Kenya.
4. Click Search.
5. From the search results, select the links that may help you get the information you
require. You may need to click on a number of links to get your exact requirement.
Information and Communication Page 25
Locate information within a website.
Once you access a website, you can search for specific text or information on that site or page.
Unlike search engines like Yahoo,
Infoseek, Lycos, Web Crawler, and Excite that present you with the
URLs or links of sites that hold information you are looking for, search engines within a web page
locate information within that web page.
Step-by-Step.
1 . Load the web page to browse. In the example below, the following website is used:
http://www.carleton.ca.
NB: The steps involved in searching are not standard, they differ from one web page to another.
2. Position the cursor within the Search box and type a keyword(s), e.g. International AND Student.
NB: When typing in a keyword you can use logical words or operators like AND (when you want to
display results that meet both criteria) and OR (when you want to display results that meet one of
the two criteria).
3. Click the go button to begin the search.
4. From the Search Results screen, click on a link that is closest to your requirements.
Task 7 Printing documents
PRINTING WEB PAGES.
To obtain a hard copy of the information that you have researched on and collected, for the
purposes of reviewing later or filing.
Step-by-Step.
Setting Page Setup options.
Before printing a web page it is advisable to check the settings in the
Page Setup dialog box. This will ensure that the right paper size, margins and orientation of the
page are set correctly. You can also add headers and footers to a web page.
1 . From the File menu click Page Setup….
2. In the Margins boxes, type the margin measurements.
3. In the Orientation area, select either Portrait or Landscape.
4. In the Headers & Footers section, specify the information to be printed.
5. Click OK.
Printing the web page.
1 . From the File menu select Print.
2. The Print dialog box appears.
3. Set the print options if necessary to print
