Introduction
The objectives of this chapter are:
- To give an overview of the major trends in telecommunications
- To describe the different types of communication networks and technologies
- To illustrate the operation of the Internet and the services that are provided over it
- To describe Intranets and Extranets and their business benefit
- To explain wireless technology and how it can be utilised for business benefit
NETWORKS AND COMMUNICATIONS
Major Trends in Telecommunications The major trends in telecommunications include:
- Rapid technological innovation has resulted in many new forms of business communications, ranging from cell phones with Internet access to Wi-Fi wireless local area networks.
- Continuing deregulation of telecommunications has driven competition leading to lowered prices for telephone services, and an expansion of alternative phone services such as wireless, cable, and Internet telephones.
- The line between telephone, cable television and Internet, has blurred as each different type of network operator (fixed line, mobile and cable TV operator) tries to provide video, voice, and data connectivity on a single network.
- Growing importance of Internet technologies in voice, video, and data communications.
- Increase in speed of broadband connections to homes and businesses.
- Rapid growth in wireless telephones, wireless computer networks, and mobile Internet devices such as smartphones and tablet computers.
- Growth in communication based services and products such as Internet telephone and video and TV over the internet. A new addition is telephone television, which is making its way into the market.
Business Network Infrastructure
The network infrastructure used in businesses today to link departments, offices, and various functions is a combination of many different networks. These include the public switched telephone network, the Internet, wide area networks and local area networks linking workgroups, departments, or office floors. The basic function of any telecommunications networks is the transmission of information from the source device through the network(s) to its correct destination while ensuring that the received message is free of errors.
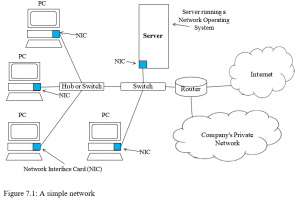
Figure 7.1 shows a simple network that includes the major components found in a company network. These components include:
- Computers (PCs), network interfaces, a connection medium network operating system software, and either a hub or a switch.
- Each computer on the network contains a network interface device (NIC) that the network is connected to.
- Connection medium for linking network components can be a copper wire, coaxial cable, fibre optic cable, or radio signal in the case of wireless
- Network operating systems manage the communications on the network between the different network elements.
- Most networks contain a hub or switch acting as a connection device between the computers or other devices on the network.
- To communicate with another network, the network would use a router which is a special communications device used to route packets of data through different networks, to ensure that any message sent gets to the correct address.
The Complexity of Large Company Networks
Today’s enterprises have large complex networks usually consisting of a number of localarea networks (LANs) linked to enterprise wide area network (WAN) for data and voice communication. Many large servers are utilised for supporting company Web sites, an intranet and extranets. The connect various applications and databases that support services such as sales, ordering, and financial transactions, inventory control etc.. These large enterprises may also have a number of enterprise applications such as supply chain management and CRM systems. A challenge for organisations is the integration of these networks and systems.
Important Telecommunications Technologies
Modern digital networks and the Internet are based on three key technologies: (1) Client/server computing; (2) the use of packet switching; (3) and the development of widely used communications standards such as TCP/IP.
Client/Server Computing
A client/server arrangement involves client computers (PCs) and a server connected across a network. The server has hard disks holding shared data, shared applications and may often have other resources that can also be shared such as printers, etc. The clients are all the other computers on the network. Under the client/server arrangement, processing is usually done by the server, and only the results are sent to the client. However, some of the processing can be shared with the client. For example, the client may request data from a database on the server; the server then processes the request and sends the results to the client, who performs further processing on the data.
The Client/server arrangement can help reduce the amount of data traffic on a network thus allowing faster response for the client computers. Security can be controlled as clients can be forced to authenticate to the server before being given access to resources. Authentication can be achieved using login names and passwords. Because management of the network is centralised, costs are lower. Since the server does most of the intensive processing, less expensive computers can be used by the clients. The main disadvantages of the client server model include the fact that if the server fails, the system fails Packet Switching:
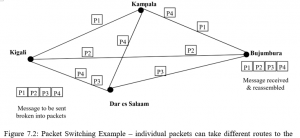
Packet switching makes efficient use of network capacity by breaking messages into small packets that are sent independently along different paths in a network and are then reassembled at their destination (see Figure 7.2).
When a user sends a message to another user on the Internet, the message is first decomposed into packets using the TCP protocol. Each packet contains the destination address of the message and sequence in the overall message. The packets are then sent from the client computer to the network server and from there to various routers on the networks to arrive at a specific destination computer address. The routers use the destination address of the packets to select a route for each packet. At the destination address, the packets are finally reassembled into the original message.
Packet Switching technology allows greater utilisation of available links and capacity
Communications Standards – Protocols
A protocol is a standard set of rules and procedures for the control of communication in a network. Having a standard set of protocols provides a universally agreed upon method for data transmission and supports communications between diverse hardware and software equipment. Examples of protocols are:
- TCP/IP: Transmission Control Protocol/Internet Protocol is a suite of protocols that is used on the Internet (and other networks) to control how the packets of data are sent and received.
- Ethernet: The Ethernet protocol is widely used in networking. It specifies rules that govern the communications between computers on a network.
TCP/IP is discussed in more detail later in this chapter.
COMMUNICATION NETWORKS
WANs, MANs and LANs
Wide Area Network (WAN): A WAN is a wide area telecommunications network, spanning a large geographical distance. WANs may use a variety of media and a combination of switched and dedicated lines.
Metropolitan Area Network (MAN): A MAN is a metropolitan area network that spans an urban area, usually a city and its major suburbs.
Local Area Network (LAN): A LAN is a network that encompasses a limited distance, usually one building or several buildings in close proximity. A router connects the LAN to other networks (such as a WAN or MAN), so that the LAN can exchange information with external networks.
Network Topologies
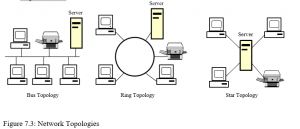
There are three main types of network topologies as shown in figure 7.3:
- In a star topology, all devices on the network connect to a single hub and all network traffic flows through the hub.
- In a bus topology, one station transmits signals, which travel in both directions along a single transmission segment. All of the signals are broadcast in both directions to the entire network, with special software to identify which device should receive each message.
- A ring topology connects network devices in a closed loop. Messages pass from computer to computer in only one direction around the loop and only one station at a time may transmit.
Transmission Media
Networks use different types of physical transmission media to carry messages from one device to another, these include the following:
- Twisted pairs: Twisted pairs of copper wires are used mostly for analogue voice signals but also for data.
- Coaxial cable: Coaxial cable consists of a single, thickly insulated and shielded copper wire, which can transmit a large volume data than twisted pair.
- Fibre optic cable and Optical networks: Fibre optic cable is made up of strands of glass fibre, each about the thickness of a human hair. The data is transformed into pulses of light which are sent through the fibre optic cable at very high speed using a laser light.
Optical networks are networking technologies for high-speed transmission of data in the form of light pulses. They are becoming important because they can transmit all types of traffic (voice, data, and video) over fibre cables and provide the massive bandwidth for new types of services and software. One advantage of this type of network is that there is very little degradation in quality, unlike transmission over copper wire.
Wireless Transmission Media and Devices
Wireless transmission involves sending signals through the air or space without the need for a physical line. Each type of wireless transmission uses specific frequency ranges. Microwave systems transmit high-frequency radio signals through the atmosphere. Other types of wireless transmission such as cellular telephones are assigned a specific range of frequencies by national regulatory agencies in line with international agreements.
Microwave systems transmit high-frequency radio signals through the atmosphere and are widely used for high-volume, long distance and point-to-point communications. Microwave signals follow a straight line and do not bend with the curvature of the earth. Therefore long distance microwave transmission systems require transmission stations to be located approximately 37 miles apart to increase the expense of microwave.
This problem can be solved by bouncing microwave signals off communication satellites, enabling them to serve as relay stations communication satellites are used for geographically dispersed organisations. However, using satellite communications can be very expensive for a business.
Comparing the speed and cost of the different transmission media
Table 7.4 summarises typical speeds for the different telecommunications transmission media.
Table 7.4: Telecommunications media
| Medium | Speed |
| Twisted wire | Up to 100 Mbps |
| Microwave | Up to 600+ Mbps |
| Satellite | Up to 600+ Mbps |
| Coaxial cable | Up to 1 Gbps |
| Fiber-optic cable | Up to 6+ Tbps |
Broadband (High Speed) Network Service Technologies
There are a number of services available to organisations that require high speed or broadband transmission capabilities or access to the Internet. These include:
- Asynchronous Transfer Mode (ATM): ATM connects all the different parts of a network into what will appear to the user as one network. It parcels data into uniform cells for high-speed transmission. It can transmit data, video, and audio over the same network. ATM equipment is expensive and as a result its popularity is declining.
- ISDN: Integrated Services Digital Network, an international communications standard for sending voice, video, and data over digital telephone lines. ISDN supports data transfer rates of 64 Kbps (64,000 bits per second). There are two types of ISDN:
- Basic Rate Access, which consists of two 64-Kbps B-channels and one Dchannel for transmitting control information.
- Primary Rate Access, which consists of 30 B-channels and one D-channel (Europe) or 23 B-channels and one D-channel (U.S.).
- Leased Line: This is a permanent connection between two points normally set up by a telecommunications company. Typically, leased lines are used by businesses to connect geographically distant offices. Unlike normal dial-up connections, a leased line is always active. The fee for the connection is a fixed monthly rate. The primary factors affecting the monthly fee are the distance between end points and the speed of the circuit. Because the connection doesn’t carry anybody else’s communications, the carrier (supplier) can assure the business (customer) a certain level of quality.
- Digital Subscriber Line (DSL) Broadband: DSL technologies use sophisticated modulation schemes to send data at high speeds over standard copper telephone wires. DSL can be used to provide high-speed connection to the Internet. The term Broadband is used to refer to a high-speed, high-capacity transmission mechanism that can be used to carry voice, data or video.
- Cable modem is service for high-speed transmission of data over cable TV lines that are shared by many users.
Connectivity to these different network transmission services are normally provided by the telecommunications service provider.
Other Networking Terms
Bandwidth
Bandwidth describes (a) the speed of data on a given transmission path and (b) the width of the range of frequencies that an electronic signal occupies on a given transmission medium. The term bandwidth is applied to both digital and analogue signals.
Bandwidth is normally measured in the amount of data transmitted per second. For example: it requires more bandwidth, to download a picture in one second than a one-line document. In digital systems, bandwidth is measured in bits transmitted per second (BPS). The higher the bandwidth, the more messages that can be transmitted or messages can be transmitted faster. Some applications working over a network will require different bandwidth than others. For example, the bandwidth required to view a video over a network is far higher than that required to view a text document.
Bandwidth can be affected by many factors – the physical media that makes up the network, the amount of network traffic, and the software protocols of the network and the network connection. To increase bandwidth, we can have higher capacity media (normally cables), or we can increase traffic speed.
Broadband
Broadband is a term used to refer to the high-speed transmission technology that can generally transmit multiple channels of data simultaneously.
Converged Network
A converged network is a network that provides technology to enable voice and data to run over a single network. These multi-service networks can potentially reduce networking costs by eliminating the need to provide support services for each different type of network. Multimedia networks can be attractive solutions for companies running multimedia applications such as video, voice-data call centres, unified messaging or for firms with high costs for separate voice and data services.
Peer to Peer Network
A peer-to-peer network is a group of computers that basically operate as equals. Each computer is called a peer. The peers share resources, such as files and printers, but no specialised servers exist. Each peer is responsible for its own security, and effectively each peer is both a client (because it requests services from the other peers) and a server (because it offers services to the other peers). Small networks may work well in this configuration. An example might involve a company in which each department wants to maintain its own files on its own computer, but allow other department to access these files.
The main disadvantages of a peer-to-peer network include lack of speed – as the number of computers on the network grows, the performance decreases because of heavy traffic. Security is also a problem as is the management of the network. Each computer owner is responsible for the management of his or her machine.
Centralised and Distributed Processing
Centralised processing is where data processing is carried out at one point. The data for processing can be gathered from several different locations. The output can then be distributed over a wide area.
Distributed processing on the other hand, allows the data processing to be distributed. There are several independent but interacting processors. These processors can be used to process the data near the source. Processors’ workloads can be balanced so if one processor is overloaded and then the load can be redistributed to another processor. Because the processing is spread between several points, if a processor fails, the other sites can continue working independently. It might be possible to off-load the work of the affected processor to the other processors in the system, thus minimising downtime.
Router
A router is a network communications device that routes messages through different network and ensures that it gets to the correct address.
THE INTERNET
The Internet, which is the largest computer network in the world, is actually a network of networks. It is a collection of hundreds of thousands of different individual network owned by governments, universities, and businesses. These interconnected networks interchange information seamlessly by using the same open, non-proprietary standards and protocol. The Internet has opened up new possibilities that challenge the existing ways of interacting, communicating and doing business.
Operation of the Internet
The Internet is a packet switched network where each message is broken into packets. Each packet contains the address of the sending and receiving machine as well as sequencing information about its location relative to other packets in the message. Individual packets may follow different routes across the network but when all the packets arrive at the receiving computer they are reassembled into the complete message.
Connecting to the Internet
The most common methods of connecting to the Internet include DSL, Leased Line, cable modem, dial-up access using a modem, and Wireless access to an Internet Service Provider (ISP).
How the Domain Name and IP Addressing System works
A domain name system converts IP addresses to domain names. A name identifies one or more IP addresses. For example, the domain name Microsoft.com represents about a dozen IP addresses. Domain names are used in Uniform Resource Locators (URLs) to identify particular Web pages. For example, in the http://www.cpaireland.ie, the domain name is cpaireland.ie. Every domain name has a suffix that indicates which top-level domain (TLD) it belongs to. There are only a limited number of such suffixes. For example:
- gov – Government agencies
- edu – Educational institutions
- org – Organisations (non-profit)
- mil – Military
- com – commercial business
- net – Network organisations
An IP addressing system is an identifier for a computer or device on a TCP/IP network. Networks using the TCP/IP protocol route messages based on the IP address of the destination. The format of an IP address is a 32-bit numeric address written as four numbers separated by periods. Each number can be zero to 255. For example, 1.10.10.220 could be an IP address.
Because the Internet is based on IP addresses not domain names, every Web server requires a Domain Name System (DNS) server to translate domain names into IP addresses. When a user sends a message to another user on the Internet, the message is first decomposed into packets using the TCP protocol. Each packet contains its destination IP address. The packets are then sent from the client to the network server and from there to the next server until it arrives at its destination address. At the destination address, the packets are reassembled into the original message.
TCP/IP
Transmission Control Protocol/Internet Protocol (TCP/IP) is the basic communication language or protocol of the Internet. It can also be used as a communications protocol in a private network (either an intranet or an extranet). Every computer with direct access to the Internet will have a copy of the TCP/IP program running on their computer.
TCP/IP is a two-layer protocol. The higher layer, Transmission Control Protocol, manages the assembling of a message or file into smaller packets that are transmitted over the Internet and received by a TCP layer at the distant machine which reassembles the packets into the original message. The lower layer, Internet Protocol, handles the address part of each packet so that it gets to the right destination. Each gateway computer on the network checks this address to see where to forward the message. Even though some packets from the same message are routed differently than others, they are reassembled at the destination. TCP/IP uses the client/server model of communication in which a computer user (a client) requests and is provided a service (such as sending a Web page) by another computer (a server) in the network. TCP/IP communication is primarily point-to-point, meaning each communication is from one point (or host computer) in the network to another point or host computer.
Internet Services
This section provides an overview on some of the main internet services and communications tools.
Communication Services
ELECTRONIC MAIL
Electronic mail systems are used by most organisations to send and messages. The Internet is the most important e-mail system because it connects so many companies and individuals. Users can attach text files, graphics, spreadsheets or even application files to a mail message. Not all networks use the same e-mail format so a computer called a gateway translates the email message to a format that the next network understands.
The components of a typical e-mail address are: Individual Name @ Domain.Function/location joeblogs@gmail.com
NEWSGROUPS
Newsgroups are international discussion groups in which people share information and ideas on a particular topic. Many newsgroups exist on the Internet. Discussion in newsgroups takes place on electronic bulletin boards where anyone can post messages for others to read.
CHATTING
Chatting allows two or more people who are simultaneously connected to the Internet to hold live interactive written conversations. Chat groups are divided into channels, each assigned its own topic of conversation.
Note: Both newsgroups and chat groups have decreased in popularity with the phenomenal growth in social networking.
TELNET
Telnet is a protocol that establishes a link between two computers. Telnet allows users to be on one computer while doing work on another. Users can log on to their office computer from their home. Also users can logon to, and use, third party computers that have been made accessible to them.
INTERNET TELEPHONY
Internet telephony (also called Voice over IP or VoIP) lets users talk across the Internet to any personal computer equipped to receive the call for the price of only the Internet connection. However sound quality can be poor due to delays in the transmission process when large amounts of data clog the Internet at certain times.
STREAMING AUDIO AND VIDEO
Streaming allows Internet users to see and hear data as it is transmitted from the host server instead of waiting until the entire file is downloaded.
Streaming audio enables the broadcast of radio programs, music, press conferences, speeches and news programs over the Internet.
Streaming video has business application including training, entertainment, communication, advertising and marketing.
Information Retrieval
Information retrieval over the Internet allows users to access thousands of online library catalogues and databases that have been opened to the public by companies, government agencies and academic intuitions. Also many users can download free software made available over the Internet.
File Transfer Protocol (FTP) enables users to access a remote computer and retrieve files from it.
The World Wide Web
While the Internet and the World Wide Web are closely related they are not the same thing. The Internet functions as a transport mechanism and the World Wide Web (also called the Web and WWW) is an application that uses those transport functions. Other applications such as e-mail also run on the Internet.
The Web is a system with universally accepted standards for storing, retrieving, and displaying information via client/server architecture. The technology supporting the World Wide Web was created by Timothy Berners-Lee who in 1989 proposed a global network of hypertext documents that would allow physics researchers to work together.
HYPERTEXT
The Web is based on a standard hypertext language called Hypertext Markup Language (HTML), which formats documents and incorporates dynamic hypertext links to other documents, which can be stored on the same or different computers. To use a hypertext link a user clicks on the highlighted word (usually coloured blue and underlined) and is then transported to another document.
HYPERMEDIA
Hypermedia is a term created by Ted Nelson in 1970. It is an extension of the term hypertext, in which graphics, audio, video, plain text and hyperlinks are intertwined in the same medium of information. Hypermedia also involves hyper-linked pages. The World Wide Web is an example of hypermedia.
WEB SITES AND HOME PAGES
Organisations or individuals who wish to offer information on the Web need to establish a home page. A home page is a text and graphical screen display that explains the organisation that has established the page and provides links to other pages. All the pages of a particular organisation or individual are known as a Web site. The person in charge of the Web site is called the Webmaster.
URLS AND HTTP
To access a Web site a user must specify the uniform resource locator (URL), which points to the address of a specific resource on the Web. The HTTP stands for Hypertext Transport Protocol, which is the transport protocol, used to transfer pages across the WWW portion of the Internet. HTTP defines how messages are formatted and transmitted and what action Web servers and browsers should take in response to various commands.
BROWSERS
Users will normally access the Web through software applications called browsers. The browser is capable of communicating via HTTP, managing HTML and displaying graphical data types such as GIF (Graphical Interchange Format) and JPEG (Joint Photographic Expert Group).
There are a number of popular browsers such as Internet Explorer from Microsoft, Firefox, Safari and Google Chrome.
SEARCH ENGINES
‘Search’ is one of the Webs most popular activity. Search engines are programs that return a list of Web sites or pages that match the selected criteria. To use a search engine a user will navigate to the search engines Web site and enter the details of the subject to be searched for. The search engine will then return the URLs of sites that match the subject entered by the user. Some of the most popular search engines are Google and Yahoo.
Unified Communications (UC)
In the past each of a firm’s networks for wired, wireless, voice and data operated independently of each other and had to be management separately by the IT department.
Now organisations are able to merge different communication modes into a single universally accessible service using Unified communications.
Unified communications technology integrates separate channels for voice communications, data communications, instant messaging, e-mail, and electronic conferencing into a single experience where users can switch back and forth between different communications modes.
Presence technology can show whether a person is available to receive a call or is occupied. Firms will need to examine how this technology can be incorporated into work flows and business processes and what alternations are needed.
Rather than having separate systems for voice mail, e-mail, conference calling, and instant messaging, the Unified communications technology can bring everything together into a more cohesive package.
Unified communications can help accelerate information sharing and allows everyone to make faster, better decisions.
Web 2.0
A Web 2.0 site allows users to interact with other users or to change website content, in contrast to non-interactive websites where users are limited to the passive viewing of information that is provided.
Web 2.0 refers to second-generation, interactive Internet-based services, such as:
- Blogs: Informal yet structured Web site where subscribing individuals can publish stories, opinions, and links to other Web sites of interest
- RSS: RSS (Rich Site Summary, or Really Simple Syndication) technology pulls specified content from Web sites and feeds it automatically to users’ computers, where it can be stored for later viewing
- Wikis: Collaborative Web sites where visitors can add, delete, or modify content on the site, including the work of previous authors
Services such as the photo sharing website Flickr, the social networking site Facebook, video-sharing site YouTube and the collaborative encyclopaedia Wikipedia are all examples of Web 2.0.
VIRTUAL PRIVATE NETWORK
A Virtual Private Network (VPN) is a secure network that uses the Internet (or a public network owned by a telephone company) as the backbone network but uses firewalls and other security features to secure connections between distant locations. A VPN offers the advantages of a private network but at a cheaper cost.
A VPN can be a private network of computers linked using a secure “tunnel” connection over the Internet. It protects data transmitted over the public Internet by encoding the data to hide its content, to provide what is a virtual private connection that travels through the public Internet.
Intranets and Extranets
Intranets
An Intranet is a private network inside an organisation that uses Internet technologies such as web browsers and servers, TCP/IP network protocols, HTML hypermedia document publishing and databases. Companies use Intranets to provide an Internet-like environment within the enterprise for information sharing, communications, collaboration, and the support of business processes.
USE OF INTRANETS IN ORGANISATIONS
In sales and marketing, intranets help oversee and coordinate the activities of the sales force. The sales force can obtain updates on pricing, promotions, rebates, customers, or information about competitors. The sales force can also access presentation and sales documents, which they can customise for specific customers.
In the human resources area, intranets keep employees informed of company issues and policies, allow employees to access and update their personnel records, and take online competency tests. Further, job postings and internal job information can be made available to employees. Employees can enrol in health care, benefit plans, or company training seminars.
In finance and accounting, intranets provide an online, integrated view of financial and accounting information in an easy-to-use format.
In the manufacturing area, intranets integrate complex information across the plant floors or many plants, particularly in managing work flow and process control.
Business Value of Intranets
There are a number ways in which an intranet can provide business value which include:
- Intranets can significantly improve communications and collaboration within an enterprise. Regardless of location, intranets allow organisational members to exchange ideas, share information, and work together on common projects and assignments.
- Intranets lower cost of publishing and accessing multimedia business information internally via intranet web sites. Examples include: employee manuals, documents, company policies, business standards, company news, staff directories, product information including pricing, competitor profiles and even training material, can all be accessed using browser software on a standard computer. This is one of the main reasons for the rapid growth in the use of intranets in business.
- Intranets can be used to integrate information from different sources into a common view.
- Intranets are being used as the platform for developing and implementing business applications to support business operations and managerial decision making. Employees within the company, or external business partners can access and run such applications using web browsers from anywhere on the network.
- A company’s Intranet can also be accessed through the Intranets of customers, suppliers, and other business partners via extranet links.
Extranets
An extranet is a type of inter-organisational information system. Extranets enable people who are located outside a company to work together with the company’s internally located employees. Extranets are network links that use Internet technologies to interconnect the Intranet of a business with the Intranets of its customers, suppliers, or other business partners. The word extranet comes from extended intranet. The main purpose of extranets is to foster collaboration between selected suppliers, customers and other business partners.
Companies can:
- Establish direct private network links between themselves, or create private secure Internet links between them called virtual private networks.
- Use the unsecured Internet as the extranet link between its Intranet and consumers and others, but rely on encryption of sensitive data and its own firewall systems to provide adequate security.
Business Value of Extranets
The business value of extranets is derived from several factors:
- The web browser technology of extranets makes customer and supplier access of intranet resources a lot easier and faster than previous business methods.
- Extranets enable a company to offer new kinds of interactive Web-enabled services to their business partners. Thus, extranets are another way that a business can build and strengthen strategic relationships with its customers and suppliers.
- Extranets enable and improve collaboration by a business with its customers and other business partners.
- Extranets facilitate an online, interactive product development, marketing, and customerfocused process that can bring better designed products to market faster.
Extranets provide the privacy and security of an Intranet with the global reach of the Internet. Extranets are becoming the major platform for B2B (Business-to-Business) electronic commerce, replacing or supplementing Electronic Data Interchange (EDI).
Electronic Data Interchange (EDI)
Electronic Data Interchange (EDI) is a communications standard that enables businesses to exchange business documents such as purchase orders, invoices, and shipment schedules electronically with other businesses. EDI formats the documents according to an agreed data standard and transmits the message. The messages can be sent over a value added network (VAN) or over the Internet. The transaction data is sent automatically from the computer systems of one business to the computer of the other business, eliminating the handling of paper and the manual re-input of data. EDI offers a number of benefits over manual systems such as reduced data entry error, better security, increased productivity and improved customer service.
WIRELESS TECHNOLOGY
Wireless communications helps businesses stay in touch with customers, suppliers and employees and supports more flexible arrangements for organising work. Wireless technology has also led to the creation of new products and services.
The Growth in Wireless Communications
Increasingly individuals and businesses are turning to wireless devices such as cell phones, wireless handheld devices, and laptops with wireless network connections to communicate and to obtain information and data.
Mobile phones are cheaper, more powerful and usage has exploded world wide. According to the International Telecommunication Union (ITU); as of Dec 2010, there are some 5.5 billion mobile subscribers worldwide, as well as about 1.268 fixed access lines, with the vast majority of new subscriptions being mobile as opposed to fixed. The number of mobile subscribers is expected to top 6 billion in 2012.
Mobile phones are no longer used exclusively for voice communications; they have become mobile platforms for delivering digital data, used for recording and downloading photos, video and music, Internet access and sending and receiving e-mail. An array of technologies are available that provide high-speed wireless access to the Internet for PCs, mobile phones and other wireless handheld devices. Businesses are increasingly using wireless networks and applications to cut costs, increase productivity and flexibility, and create new products and services.
Business Value of Wireless Networking
There are a number ways in which wireless technology can provide business value which includes:
- Wireless technology helps businesses stay more easily in touch with customers, suppliers, and employees and provides more flexible arrangements for organising work.
- Wireless technology increases productivity and worker output by providing anytime, anywhere communication and access to information.
- Companies can save on wiring offices and conference rooms by using wireless networks because they do not have to pull cables through walls. Wireless networks also make additions, moves, and changes much easier.
- Wireless technology has also been the source of new products, services, and sales channels in a variety of businesses.
Devices for Wireless Transmission Devices for wireless transmission include:
E-mail hand held devices: These devices include a small display screen and a keypad for typing short messages. Some versions of these devices have a built in organiser, web and voice transmission features and the ability to integrate with corporate applications. An example of an E-mail wireless handheld device is the Blackberry.
Cellular telephones (Cell phones): These work by using radio waves to communicate with radio antennas (usually located in towers or masts) placed within adjacent geographical areas called cells. A telephone message is transmitted to the local cell by the cellular telephone and then passed to the cell of its destination where it is transmitted to the receiving telephone. As the cellular signal travels from one cell into another (as the location of the mobile phones moves) a computer that monitors signals from the cells switches the conversation to a radio channel assigned to the next cell.
Short message service (SMS) is a text message service used by a number of digital cell phone systems to send and receive short alphanumeric messages less than 160 characters in length. Like e-mail, SMS messages can be forwarded and stored for retrieval later.
Smart phones: This class of digital communications device combine the functionality of a Personal Digital Assistant (PDA) with a digital cell phone and require a cellular phone service connection. These smart phones can handle voice transmission and e-mail, save addresses, store schedules, access a private corporate network, and access information from the Internet. Smart phones include Web browser software that enable digital cellular phones to access Web pages formatted to send text or other information that is suitable for small screens. Increasingly smartphones are also fitted with built in WiFi which can be used to provide high speed access to the Internet at a designated WiFi enabled location.
Personal computers are also starting to be used in wireless transmissions – most new laptops are now Wi-Fi enabled.
Cellular Network Standards and Generations
Major cellular standards include Code Division Multiple Access (CDMA), which is used primarily in the United States, and Global System for Mobile Communication (GSM), which is the standard in Europe and much of the rest of the world.
Cellular networks have evolved from slow-speed (1G) analogue networks to high-speed highbandwidth digital packet-switched third-generation (3G) networks with speeds ranging from 144 Kbs to over 2 Mbps for data transmission. Second-generation (2G) cellular networks are digital networks used primarily for voice transmission, but they can also transmit data at ranges from 9.6 to 14.4 Kbps. 2.5G networks are packet-switched, use many existing infrastructure elements and have data transmission rates ranging from 50 to 144 Kbps. A 2.5G service called General Packet Radio Service (PRS) transports data over GSM wireless networks and improves wireless Internet access. 2.5G also improves data transmission rates for CDMA. See figure 7.5 for a summary of these generations.
| Generation | Capacity | Description |
| 1G | Low | Analogue cellular networks for voice communication |
| 2G | 10 to14Kbps | Digital wireless networks, primarily for voice communication; limited data transmission capability |
| 2.5G | 50 to144 Kbps | Interim step toward 3G in the US similar to GPRS in Europe |
| 3G | 144 Kbps to 2+ Mbps | High speed, mobile, supports video and other rich media, always on for e- mail, Web browsing, instant messaging |
| 4G | Up to 100Mbps | This is the next evolution of wireless cellular networks |
Figure 7.5: Wireless Cellular Generations
Wireless Computer Networks and Internet Access
This section discusses the major standards for wireless networks and for wireless Internet access. The Institute of Electrical and Electronics Engineers (IEEE) has established a hierarchy of related standards for wireless computer networks. These include:
- Bluetooth (802.15) for small personal area networks,
- Wi-FI (802.11) for Local Area Networks (LANs),
- WiMax (802.16) for Metropolitan Area Networks (MANs).
Bluetooth
Bluetooth is a telecommunications industry specification that describes how mobile phones, computers, and personal digital assistants (PDAs) can be easily interconnected using a shortrange wireless connection. Bluetooth can link up to eight devices within a 10-meter area using low-power, radio-based communication and can transmit up to 722 Kbps in the 2.4 GHz band. Wireless phones, keyboards, computers, printers, and PDAs using Bluetooth can communicate with each other and even operate with each other without direct user intervention. Through this technology, users of cellular phones, pagers, and personal digital assistants can buy a three-in-one phone that can double as a portable phone at home or in the office, get quickly synchronised with information in a desktop or notebook computer, initiate the sending or receiving of a fax, initiate a print-out, and, in general, have all mobile and fixed computer devices coordinated completely.
Bluetooth is designed for personal area networks that are limited to a 10-meter area. It has low power requirements, so it is better for battery-powered appliances.
Wi-Fi
Wi-Fi stands for Wireless Fidelity and refers to the 802.11 family of wireless networking standards.
The 802.11a standard can transmit up to 54Mbps in the unlicensed 5GHz frequency range and has an effective distance of 10 to 30 meters. The 802.11b standard can transmit up to 11 Mbps in an unlicensed 2.4 GHz band and has an effective distance of 30 – 50 meter area, providing a low-cost flexible technology for creating wireless LANs and providing wireless Internet access.
A Wi-Fi system can operate in two different modes:
- Infrastructure Mode: In this mode, wireless devices communicate with a wired LAN using access points. An access point is box consisting of a radio receiver/transmitter and antennas that link to a wired network, router, or hub. Each access point and its wireless devices are known as a Basic Service Set (BSS).
- Ad-hoc Mode: In this mode, also known as peer-to-peer mode, wireless devices communicate with each other directly and do not use an access point. Most Wi-Fi communications use an infrastructure mode.
Wi-Fi hotspots which are located in hotels, restaurants, airports, libraries, college campuses, and other public places provide mobile access to the Internet. Hotspots generally consist of one or more access points positioned on a ceiling, wall or other spot in a public place to provide maximum wireless coverage for a specific area. Users within range of the hotspot can then access the internet from their laptop or mobile device. Most laptops, smart phones and tablet computers come equipped with wireless network interface card (NIC) built–in radio that can send and receive Wi-Fi signals.
Wi-Fi networking costs have declined so that a basic network can be setup relatively cheaply.
Benefits of Using Wi-Fi The benefit of Wi-Fi include:
- Can be used create low-cost wireless LANs and to provide Internet access from conference rooms and temporary workstations.
- Helps individual companies extend their networking to new areas and obtain Internet services at a low cost.
Challenges of Using Wi-Fi
The challenges of using Wi-Fi include:
- Transforming Wi-Fi from a wireless hit-or-miss phenomenon into a sustainable business.
- Users cannot freely roam between hotspots if they use different Wi-Fi network services.
- Public and private hotspots need to be transformed into interoperable, dependable networks with billing systems, roaming agreements, and technical standards that will enable users to plug into hotspots at will.
- Overcoming weak security features that make Wi-Fi wireless networks vulnerable to intruders.
- Susceptibility to interference from nearby systems operating in the same spectrum.
WiMax
WiMax, which stands for Worldwide Interoperability for Microwave Access, is the popular term for IEEE Standard 802.16, which is known as the “Air Interface for Fixed Broadband
Wireless Access Systems.”
WiMax antennas are able to beam high-speed Internet connections to rooftop antennas of homes and businesses that are miles away. WiMax has a wireless access range of up to 31 miles and a data transfer rate of up to 75 Mbps, making it suitable for providing broadband Internet access in areas lacking DSL and cable lines. Whereas Wi-Fi is vulnerable to penetration by outsiders, WiMax (802.16) has robust security and quality of service features to support voice and video.
Radio Frequency Identification (RFID)
Radio frequency identification (RFID) systems use tiny tags that have embedded microchips that contain data about an item and its location. The tag transmits radio signals over a short distance to special RFID readers. The RFID readers then pass the data over a network to a computer for processing (As shown in Figure 5.6). This technology provides value to a business by capturing data on the movement of goods as these events take place and by providing detailed, immediate information as goods move through the supply chain.
RFID and Privacy Issues
Privacy activists have objected to RFID technology applications that could lead to more tracking and monitoring of individual behaviour. They fear it could someday enable marketers, the government, or insurers to compile details about individuals’ shopping habits or even assist in tracking people’s movements.
Wireless in Health Care
Health care systems have traditionally been dominated by paper based processes. The vast majority of hospitals have communications networks but still have problems getting essential information to the right place at the right time.
Mobile technology can provide some solutions. Some Hospitals are installing wireless LANs in emergency rooms and treatment areas and are equipping staff with Wi-Fi enabled laptop computers or wireless handheld devices and Smart phones.
MANAGEMENT OPPORTUNITIES AND CHALLENGES
Some businesses will benefit from incorporating wireless technology into their business strategy, while others may not. Before investing heavily in wireless technology, firms must address a series of technology and organisational issues.
Opportunities
Wireless technology opens up new opportunities to business which include:
- Wireless technology gives firms more flexibility and the ability to innovate.
- Wireless systems support business processes that are not limited by time or location, extending the company’s reach and saving employees and customers substantial amounts of time.
- The technology provides a new channel for connecting with customers.
- It can also be a source of exciting new products and services.
Management Challenges
The principal challenges posed by wireless technology are integrating this technology into the firm’s IT infrastructure and maintaining security and privacy.
Integrating Wireless Technology into the Firm’s IT Infrastructure
A large enterprise may have hundreds of wireless access points and many thousands of wireless devices to configure and monitor, similar to a desktop environment. It will be a challenge to integrate this new network infrastructure with the firm’s existing infrastructure and applications. Central coordination and oversight are required.
Some companies have found that the savings they expected from using wireless technology did not materialise due to unexpected costs. Gains in productivity and efficiency from equipping employees with wireless mobile computing devices must be balanced with increased costs associated with integrating these devices into the firm’s IT infrastructure and providing technical support.
Maintaining Security and Privacy
Maintaining security and privacy poses special challenges for users of wireless technology. Wi-Fi security is not well developed, making such systems especially vulnerable to infiltration from outsiders. Wireless systems are easily susceptible to interference from other devices in the same bandwidth.
One of the unique benefits of wireless technology is its location-tracking capability. However, this same capability worries privacy advocates who fear the technology could be used to continuously monitor where users are going and what they are doing. These privacy issues are particularly relevant to RFID technology and mobile phones.
