WEDNESDAY: 3 August 2022. Afternoon paper. Time Allowed: 3 hours.
This paper has two sections. SECTION I has twenty (20) questions of forty (40) marks. SECTION II has three (3) practical questions of sixty (60) marks. All questions are compulsory. Marks allocated to each question are shown at the end of the question.
SECTION I
1. What is the name of the media used to transmit data that is encoded as pulses of light? (2 marks)
2. An IPv6 _____________is an address that is assigned to a set of interfaces that typically belong to different nodes. (2 marks)
3. Which category of network devices performs the following functions?
• Regenerate and transmit communication signals
• Maintains information about what pathways exist through the network and internetwork
• Notify other devices of errors and communication failures. (2 marks)
4. Which communication term is used to describe the piece of information sent between one sender and one receiver? (2 marks)
5. The term____________is used to describe a piece of data at any layer of a networking model. (2 marks)
6. What is the name given the process of placing one message into another message format for transfer from source to destination? (2 marks)
7. Mr. Shawn a newly employed Network administrator is troubleshooting network connectivity issues on a server. He noticed signals generated by the server NIC using a tester were distorted. Which layer of the OSI reference model is associated with the error? (2 marks)
8. ______________refers to the amount of data that can flow from one place to another in a given amount of time (2 marks)
9. What is the measure of the transfer of bits across the media over a given time period? (2 marks)
10. Computer systems were created to understand binary addressing. Which IPv4 address format was created for ease of use by people ? (2 marks)
11. What is the name given to the data transmitted over the network and can flow in one direction at a time? (2 marks)
12. The data link layer of the Open System Interconnection Model (OSI) describes media access and physical addressing where the encoding of a MAC address on a Network Interface card is placed. Which layer of the OSI model is the Internet Protocol (IP) Address placed? (2 marks)
13. You have been tasked to develop a physical topology network for an upcoming cement industry that provides a high level of redundancy. Which physical topology interconnects multiple groups that are located on the separate layers to form a larger network? (2 marks)
14. An IPv4 address of 192.168.60.255 on 192.168.60.0/24 network is considered to be ___________ address, which is statically mapped to ff-ff-ff-ff-ff-ff in the ARP table (2 marks)
15. Which message attributed to IPv6 is sent by a node to determine the link-layer address of a neighbor is still reachable via a cached link-layer address? (2 marks)
16. __________allows a laptop or PC to use the Internet connection of a mobile device such as a cell phone, usually through a cellular data connection. (2 marks)
17. A WAP is a device that allows different types of wireless network cards connect without cables, hence wireless, to connect to LANs and access resources, including the Internet. Which feature of 802.11n wireless access points allows them to transmit data at faster speeds? (2 marks)
18. Internet access is the ability of individuals and organizations to connect to the Internet using computer terminalsand other devices. Which type of telecommunication technology is used to provide Internet access to vessels at sea and airplanes in flight. (2 marks)
19. Which type of IPv6 address can only be used for communication on a single network and NOT other networks using routed protocol? (2 marks)
20. Which IPv4 subnet mask would be used if 2 host bits are available? (2 marks)
SECTION II
21. Create word processing document named Question 21 and use it to save solution to questions (i) to (iv) below in form of screenshots.
Network administrator’s use /24 network address to subdivide a network using longer prefix lengths by borrowing bits from the fourth octet in order to assign network addresses to a smaller number of end devices. Analyse the diagram below and answer the following questions:
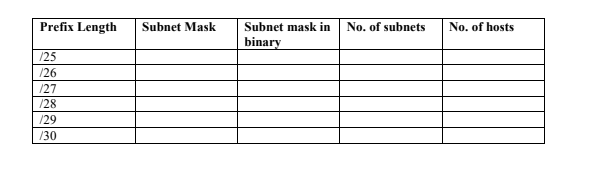
Required:
1. Compute the subnet mask for each prefix length. (4 marks)
2. Compute the subnet mask in binary for each prefix length. (4 marks)
3. State the Number of subnets for each prefix length. (6 marks)
4. State the number of hosts for each prefix length. (6 marks)
Upload Question 21 document.
(Total: 20 marks)
22. Create a word-processing document named Question 22 use it to save solutions to question 1 to 6 below in form of screenshots.
Required Resources
PC (Windows/Linux with internet access and Wireshark installed)
Data flows down the Open System Interconnection (OSI) layers when upper layer protocols communicate with each other and is encapsulated into layer 2 frame. Use Wireshark to examine Ethernet frames of the topology you are using. The topology is represented by the diagram below.
Required:
1. Examine and record the network configuration of your host PC (4 marks)
2. Using Wireshark capture the following:
Frame details of the ARP Request (3 marks)
Frame details of the ARP Reply (3 marks)
3. Identify and list the significance about the contents of the destination address field. (2 marks)
4. Capture details showing the MAC address of the source in the first frame. (2 marks)
5. Capture details showing the MAC address of the destination in the first frame. (2 marks)
6. Capture details showing the Vendor ID (OUI) of the Source NIC in the ARP reply. (4 marks)
Upload question 22 document.
(Total: 20 marks)
23. Create a word-processor document named Question 23 use it to save solutions to question 1 to 6 below in form of screenshots.
Use a simulator to design the topology as shown below:
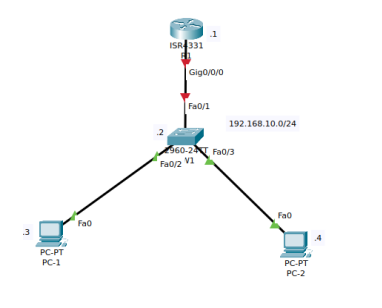
Required Resources
Packet Tracer/GNS3 simulator
Required:
1. Configure appropriate names to the Router (3 marks)
2. Configure a warning banner (3 marks)
3. Configure appropriate interface descriptions (3 marks)
4. Configure unicast IPv4 addresses as shown in the topology (4 marks)
5. Disable DNS lookup (3 marks)
6. Configure encrypted privileged execution password (4 marks)
Upload question 23 document.
(Total: 20 marks)
