KCSE Past Papers Computer Studies 2013
5.9.1 Computer Studies Paper 1 (451/1)
1. (a) CAD – Computer aided design.
(b) DVD – Digital video disk digital versatile disk.
(c) WORM – Write once read many.
(d) POS – Point of sale/point of sale terminal.
2. – Indexing becomes easier.
- Minimises on memory used.
- Ease of data entry.
- Reduces redundancies/double entry.
- Speedy searches due to shortened comparisons
- Simplifies validation
3. In cc, all the recipients of the mail are able to see other recipients of the same mail.
Bcc: In Bcc, all recipients of the mail are not able to see other recipients. 2 marks
4. – Risk of electric shocks to the users.
- Risk of fire outbreaks in the laboratory.
- Risk of tripping and injuries.5. List two career opportunities associated with computer networking.
- Network administrators
- Network engineers – Network technicians6. (a) Row 1 or 1
(b) = D2 * E2; = product (D2. E2)
OR = Product (D2: E2)
2 marks
7. – Customised to suit business needs of the organisation.
- It can be upgraded as needed by the organisation.
- The organisation can have a module that the competitors don‘t have.
- The organisation develops only the modules needed/memory eptimization. or storage/space.2 marks
(a) Hybrid topology/tree/hierarchical (1 mark)
(b) Star and Bus topologies (line/linear) (2 marks)
9. (a) The implementation strategy is:
- phased change-over/modular(1 mark) (b) Reasons for partial approach.
- It gives employees opportunity to learn
- Organization can revert to old system in case of failure.
- Reduces resistance by employees.
l0. (a) Importance of disk partitioning.
- Disk partitioning enhances logical management of files since files can be grouped into partitions based on their roles.
- Enhances disk maintenance since partitions can be formatted, deleted or modified individually without affecting files stored in other partitions.
- Partitioning helps in virus management. This is done by keeping system files in one partition with limited access rights. Viruses would therefore lack access to the system files.
- Enables installation of more than one operation system. (2 marks)(b) Difference between pull-down and pop-up menus
A pull-down menu is a list of commands that appears as a list from the menu bar going down which is invoked by the click or alt key whereas a pop-up menu is a list that appears anywhere on the screen when there is a click.
(2 marks)
11. Negative social impact of ICTs
- lntemet addiction
- Privacy violation
- Exploitation (sexual) through Ponography
- Crime – fraud on the intemet
- Cyber terrorism
- Recuirtment to drug trafficking/drug abuse
12. Explanation of DTP preference over word processor in designing a publication. DTP is designed with facilities to support and manipulate graphics that are not found in traditional wordprocessors. eg. the facilities are such as page layout, colour libraries and object layering.
(2 marks)
13. Possible causes of Hard disk blinking.
- Virus executing itself.
- Updating of some software applications.
- Network access taking place.(2 marks)
14. Compatibility factors on computer choice.
- Compatibility with available software. Being able to have the available software installed.
- Having the available peripherals in the market being able to be connected.. (2 marks)
15. Appropriate output devices
(i) Carbon copies – impact printers e.g.dot matrix.
(ii) Architectural design – plotter
(iii) Visual impairment – speakers brailles.
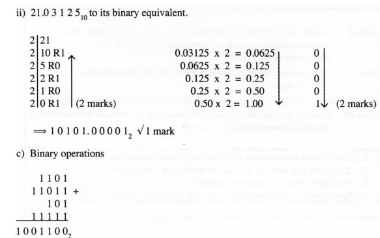
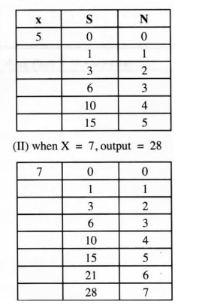
16. (a) (i) Output from the flow chart if:
(l) when X = 5,output = I5 (2 marks)
- (b) Language translators
- Assemblers
- Compilers
- Interpreters
SECTION B
l7 (a) Validation checks u
- Range checks: checks that data lies within a range of values.
- Presence checks: checks that data is there and has not been missed out.
- Length checks: checks that fields are of the right number of characters.
- Type checks: checks that the data is of the right type.
- Format checks: checks whether data is in the correct format.Any 3 x 2
(b) Methods to prevent unauthorised access:
- Password: A secret word; a string of characters known only to a restricted group for authentication.
- User Access levels: A case where each group is granted different levels of BCCCSS
- User Access rights: An individual is granted access or denied access to (c) (i) (I) Real-time
ln a real-time processing, there is a continual input. process and output of data instantaneously upon receipt of command. (11) Interactive processing
A computer processing in which the user can modify the operation appropriately while observing results at critical steps.
(ii) Application area for real-time mode
Airline booking. medical system, car tracking system, hotel booking system, banking system.
Definition of a laptop computer
12 (a) (i) ls a portable computer small enough to be used on laps.
(evidence of portability, mobility, small size) l7″ screen (ii) Diagonal length of the screen. An indication of the size of the screen. (mention of size only 1 mark)
(b) Advantages of the following:
(i) modem
- For internet connectivity
- Converts analog signal to digital signals and vice versa.
- It is wireless technology of internet at any point. (ii) USB
- Most peripheral devices are connected to the computer via USB ports.
- Has high speed rate.
- Supports both power and data transmission.
- One USB can support 127 devices at a time.(iii) Free suite:
The user is not required to buy a licence for use of the software. (several software packed as one) (c) Package suitability
(i) Computing budgets – spreadsheets.
(ii) Creating documents – word processor.
(iii) Designing brochures < DTP.
(iv) Records management – Databases/spreadsheet.
(d) (i) Three advantages of using a computer for designing an advert such as the one in fig. 4
- Advert can be stored for future use.
- Modification of the advert is easy.
- Ease of design due to tools and template availability advantages/does not require an expert.
- Ease of upload.
- Can be electronically sent. (ii) 2 benefits of Intemet advertising as in figure 4.
- Wider coverage.
- Feedback from viewers/ visitors can be received instantly.
- Service is throughout.
- cost is low.
19. (a) E-mail: – used to send and receive electronic documents to/from the office.
- receive instructions from the supervisor or co-workers. (any e-mail related work)
- Fax: – Used to send documents which are in non-electronic format (any fax related work)
- Digital camera – Used to capture images in picture form/video conferencing.
- Firewall – Used to prevent intrusion to the home computer because telecommuting involves connection to the intemet.(b) – Communication systems may fail/communication channel may fail.
- The document sent may get lost due to sending to wrong address.
- The documents may be re-used or updated.
- Malfunctioning of either sending/ receiving computers (failure of DTE).
(c)
- Employer will only pay for work done.
- The working time is not limited to official working hours/office available 24 hours.
- Employer saves on office space.
- Does not have to pay for commuter allowance.
- Employer may not require permanent employees.
- Employer may outsource expert skills that are not available locally.
(a) (i) In one‘s complement, a negative number is represented by taking all its bits in the positive number and inverting them. In two’s complement, you start with one’s complement but add 1 to the results.
In two’s complement, there are no two ways of presenting a zero. In one’s complement, overflow bit is added back to the answer but ignored in two’s complement.
OR
(ii) Binary number system over decimal
- it is easy to program.
- uses bi-state devices which can either be ON or OFF.
- Binary can be used to represent all types of data.(b) (i) Subtract l 000112 from 0100102 using one’s complement method.