Introduction
The objectives of this chapter are to:
- Describe the Ethics Social and Political Issues of Information Systems
- Describe the impact of modern information systems and the Internet on the protection of individual privacy and intellectual property.
- Give a brief overview of Data Protection legalisation
ETHICAL AND SOCIAL ISSUES RELATED TO SYSTEMS
Ethics creates theories about the nature of right and wrong, duty and obligation that individuals can use to guide their behaviour. Individuals act within a social environment that, in turn, exists within a political environment. Ethical dilemmas are problems that affect society as a whole and are often dealt with in a political setting. The development of Information systems can drive intense social change thereby raising new ethical questions for both the individuals and societies involved. For example, new computer technology makes it easier to gain private information about individuals, such as their shopping preferences, names, addresses, phone numbers and e-mail addresses as well as bank and social security details, creating an ethical dilemma for the potential user of that information (whether or not to invade the privacy of the individual). Society will react by demanding new laws to regulate the use and storage of data.
Ethical, Social, and Political Issues
Introducing a new technology can gives rise to new ethical, social and political issues that must be dealt with on individual, social and political levels. These issues have five moral dimensions: information rights and obligations, property rights and obligations, system quality, quality of life and lastly accountability and control. Introducing a new Information system can affect ethical issues that in turn lead to social issues and these subsequently cause political issues. This demonstrates the tight relationship between ethical, social and political issues in this modern information society and how introducing a new information system can ultimately impact on them all.
Five Moral Dimensions of the Information Age
Laudon and Laudon (2010) describe five moral dimensions of information systems as follows:
- Information Rights: What information rights do individuals and organisations have with respect to information about themselves? There are also moral obligations for those dealing with this information.
- Property Rights: How will intellectual property rights be protected in a digital society, where traditional measures that protect property are no longer applicable?
- Accountability and Control: Who can be held responsible for damage caused to individual information and property?
- System Quality: Data quality and system errors – No software program is perfect, errors will be made, even if the errors have a low probability of occurring
- Quality of Life: What values should be retained in an information society? Which cultural values and practices are supported by the new information technology?
These dimensions pose useful ethical questions that a company should consider when introducing a new technology.
These issues are discussed in more detail in Section 3.3.
Technology Trends That Raise Ethical Issues
There are a number of technological trends that generate ethical concerns including:
- Computing power has doubled every 18 months: This is enables growing numbers of organisations to use information systems in their primary business practices. This is increasing reliance on systems and increases vulnerability to system errors and reduced data quality.
- Rapidly falling data storage costs and developments in data storage techniques: This has led to big increases in the amount of data kept on individuals by private and public organisations – allowing for violation of an individual’s privacy.
- Networking advances and the Internet: This enables personal data to be remotely accessed. It is incredibly easy to copy data from one location to another. This raises the issue of who actually owns the data? Furthermore, how can this ownership be protected?
- Advances in data analysis techniques: This has enabled companies and government agencies to use profiling to establish detailed information about an individual’s behaviour and tastes and to create a record of this personal information.
- Non-obvious Relationship Awareness (NORA) is a new data analysis technology that can locate obscure hidden connections between people or other entities by analysing information from a range of sources to identify relationships. This technology is used by governments and the private sector to provide powerful profiling. NORA can gather information about people from many sources such as job applications, telephone records, customer records, court record, tax records etc. This correlates relationships so that hidden connections can be uncovered that might help identify criminals or terrorists. NORA poses ethical questions in relation to privacy implications for individuals. In other words the information that each of us generates about ourselves every day can be correlated, manipulated, mined and sold, as it is very valuable. This is an intrusion into an individual’s privacy and is a major ethical issue for our society
ETHICAL DILEMMAS IN THE INFORMATION SOCIETY
Responsibility, Accountability and Liability
The term responsibility means that an individual must accept the possible costs and obligations for the decisions they make. Accountability is a feature of systems and social institutions that establishes who is responsible. Liability is an aspect of political systems that allows individuals to recover damages done to them by individuals or organisations that are deemed responsible. Due-process requires that laws are known and understood by all and that individuals can appeal to higher authorities to ensure laws were properly applied.
Ethical Analysis
If faced with a situation that poses ethical issues and dilemmas, the following five-step analysis can be applied:
- Identify and explain the facts clearly
- Define the conflict or ethical dilemma posed and recognize the higher order values concerned
- Identify the stakeholders
- Assess the options that can be reasonably taken 5. Identify the possible consequences of these options.
Ethical Principles
Once the 5-step analysis above has been carried out, the following six ethical principles can be applied to aid in decision making:
- The Golden Rule: It suggests doing unto others, as you would have them do unto you. This ethical guideline is found in all major religions and traditions.
- Immanuel Kant’s Categorical Imperative: Act on rules that you wish to apply to yourself and universally. This suggests that if an action is not right for everyone to take, then it is not right for anyone.
- Descartes’ Rule of Change: This rule also known as the slippery slope rule, suggests that if an action cannot be taken repeatedly, then it is not right to be taken at any time.
- Utilitarian Principle: The Utilitarian Principle suggests taking the action that overall achieves the higher or greater value. An action is good if it promotes ‘happiness’ over ‘pain’ between those affected by it.
- Risk Aversion Principle: The Risk Aversion Principle suggests taking the action that produces the least harm or the least potential cost
- The Ethical “no free lunch rule”: This rule says that practically all tangible and intangible objects are owned by someone unless there is a specific declaration to state otherwise. If someone has created something of value to you, that person probably wants some form of payment for your use.
Code of Conduct for Professionals
In declaring one-self to be a professional, special rights and obligations are taken on. Being a professional, involves entering into constrained relationships with employers, customers, and society due to special claims to knowledge, wisdom and respect. Professional codes of conduct are propagated by associations of professionals in order to regulate entrance qualifications and competencies and to establish codes of ethics. Codes of ethics are applied by professions to regulate themselves in the general interest of society. For example honouring property rights and including intellectual property rights.
Examples of Ethical Dilemmas – related to IT systems
The following are some real world examples of ethical dilemmas:
- Using IT systems to increase efficiency can have the knock-on effect of causing layoffs and personal hardships
- Using IT systems to monitor employee e-mail in order to protect valuable company assets, is coupled with the ethical dilemma of invading employee privacy
- Monitoring employees’ use of the Internet at work similarly decreases employee privacy
THE MORAL DIMENSIONS OF INFORMATION SYSTEMS
Information Rights
Privacy is defined as a state in which an individual is not being observed or disturbed by other people or organisations. Claims to privacy involve the workplace as well as the home. Information technology threatens the individual’s claims to privacy by making the invasion of privacy cheap, profitable and effective. An example of Information technology affecting the individual’s claims to privacy is the controversy related to Google Street view where pictures of people’s homes and individual were displayed on the internet without their consent.
Most European and American privacy law is based a set of principles called the Fair Information Practices (FIP) which govern the collection and use of information about individuals. The five FIP principles are:
- Notice/awareness;
- Choice/consent;
- Access/participation;
- Security;
For more details on the Fair Information Practices (FIP), see section 14.1 in Appendix 1
Data Protection For example:
Privacy protection in Europe is far stricter than in the United States. In contrast to the US, European countries do not permit the use of personally identifiable information by businesses without the consumer’s prior consent.
How the Internet is challenging the protection of individual privacy
Internet technology creates new obstacles to the protection of an individuals’ privacy. When information is sent over the Internet it may pass through a variety of different computer systems before it finally reaches its intended destination. Each of these systems may jeopardise the individuals’ privacy as they are capable of monitoring, recording and storing information that pass through them.
Web sites can uncover an individual’s identity if they register on the web site in order purchase a product or utilise a free service. Web sites can capture information about individuals that visit their site without their knowledge using a technology called cookies (see Figure 4.3).
Cookies are small files sent by a Web site to the user’s browser, which are subsequently used to identify the visitors Web browser and track visits to the Web site. In this way the site can customise its content to the interests of each particular visitor. For example if you purchase a book on Amazon the Website will be able to recommend other books of interest based on previous purchases. Most modern Web browsers allow users to decide whether to accept cookies or not. However rejecting cookies may make some websites unusable.
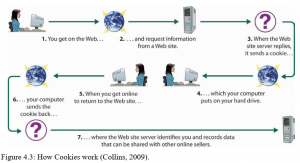
Figure 4.3: How Cookies work (Collins, 2009).
Other malicious tools include Web bugs, which are small graphic files embedded in e-mail messages and Web pages that record who is reading the e-mail message or Web page and communicates this information to another computer.
Protecting the Individual privacy of Internet users
There are a range of approaches that can be implemented to protect the privacy of Internet users, these include the following:
- Informed consent means that an individual visiting a Web site knowingly consents to the collection of their data upon visiting the company’s Web site. Federal privacy laws in United States help mediate the correct collection, usage and disclosure of information. Similar laws exist in the majority of European countries.
- Self-regulation: Businesses have taken some steps to enhance protection of Internet users privacy, including publishing statements regarding how their information will be used and sometimes offering an opt-out right. However, few businesses offer an opt-in approach, which is far more favourable for protection of privacy, whereby it is prohibited to collect personal data unless the individual approves it.
- Laws and privacy legislation: These can help regulate the collection, usage, and disclosure of information.
- Technical solutions: Several technology tools are available to combat privacy invasion including e-mail encryption, anonymous e-mailing and surfing, cookie rejection and Spyware detection. The Platform for Privacy Preferences (P3P) is a benchmark for relating a Web site’s privacy policy to its visitors to enable them to select the level of privacy they desire to maintain while using the Web site.
Intellectual Property Rights
Intellectual property describes intangible property created by individuals or businesses. Developments in Information technology has created obstacles to the protection of intellectual property because of the ease with which information can be copied and circulated over networks such as the Internet. Described below are three legal mechanisms that protect property rights are trade secret, copyright and patent.
Protecting Property Rights
A trade secret is any intellectual work product used for a business purpose that can be classified as belonging to that business, provided it is not based on information available in the public domain. An obstacle to trade secret protection is that once an idea enters into the public domain, it can no longer be protected as a trade secret.
A copyright is a statutory grant that protects creators of intellectual property against their work being copied by others for any purpose.. A patent allows the owner a monopoly on the ideas behind an invention for 20 years. While patent protection does grant a monopoly on the underlying concepts and ideas, there is a challenge to passing stringent criteria of nonobviousness, originality and novelty. The Internet makes it very easy to widely distribute and reproduce intellectual property.
Challenges posed to Intellectual Property Rights
Digital media and software can now be so readily copied, altered, or transmitted, that it is becoming increasingly difficult to protect with existing intellectual property safeguards. Illegal copying of software and music and video files is a widespread problem with no immediate solution or prevention.
While it is possible to protect against copying of software program code, copyright protection can’t prevent another person from using the underlying ideas behind a piece of software and subsequently developing new software that follows the same fundamental concepts. Patent protection protects the underlying ideas behind software. However a very limited amount of software has received this protection because the software must first pass very stringent criteria concerning the originality and novelty of the ideas involved in its design. The Internet poses a huge challenge to Intellectual Property Rights because it makes it even easier to copy intellectual property and transmit it freely around the world.
The Business Software Alliance (BSA) is a registered, non-profit trade association composed of the worlds leading IT organisations and majors software publishers (such as Microsoft and Oracle). The principle aims of the BSA involve promoting awareness among both the public and businesses of proper software management practices and the value of software compliance.
Methods are being developed for the sale and distribution of books, articles and other intellectual property legally on the Internet. The Digital Millennium Copyright Act (DMCA) of 1998 is supplying some copyright protection. The DMCA put into practice a World Intellectual Property Organisation Treaty that makes it illegal to ignore technology-based protection of copyrighting.
SOFTWARE PIRACY
Software piracy encompasses the unauthorised copying, distribution and/or use of copyrighted software products. Huge financial loses occur each year to the software industry as a result of software piracy.
FORMS OF SOFTWARE PIRACY
The following are the primary forms of software piracy:
- Illegal use by End users: This involves the use of copyrighted software without an appropriate licence or allowing more users of the software than the licence permits.
- Illegal Copying: This consists of making unauthorised copies of software for installation on other computers and also producing copies for private sale.
- Illegal Bundling: This is where hardware vendors without proper licensing install copyrighted software onto computers they are selling to increase revenue.
- Professional Counterfeiting: This involves the illegal copying and sale of software along with imitation logos, manuals and licences to disguise the illegal product.
SOURCES OF SOFTWARE PIRACY
The main sources of software piracy are the following:
- End users who purposely disobey the law or are ignorant of it
- Organisation that ignore the law
- Unprincipled hardware or software dealers
- Internet sites that sell counterfeit software or make them available for illegal download Accountability, Liability and Control
As well as acting as obstacles to both privacy and property rights, modern information technologies are challenging existing liability laws and social practices for holding individuals and institutions accountable.
It is very difficult, if not impossible, to hold software producers liable for their software products as it is only when software acts as a part of a defective product that stringent liability pertains. However, if the software is strictly a service (not part of a product) these laws do not apply.
Other interesting ethical issues are: Should an Internet Service Provider (ISP) be held liable for the material that users transmit, when telephone companies are not held liable for the messages that users transmit over the phone? Should the providers of online bulleting boards (and blogs) be held liable for the content posed on these sites? Also should authorities do more to control the cumbersome amounts of Spam in circulation? Spam is described as unrequested junk e-mails sent to thousands of Internet users. The primary ethical issues raised by new technology are whether or not the individuals and organisations that create, produce and sell systems are morally responsible for the consequence of their use. Furthermore, what liability should the users assume and what liability should the provider assume?
Note: A Blog is defined as a form the online diary or journal where people provide commentary or articles on a particular subject. Blogs are continuing to grow exponentially in number, popularity and content.
Causes of System Quality Problems
The primary sources of system quality problems are hardware and facility failures, software bugs and errors, and low data quality. It is of note that while software companies generally try to de-bug their products before releasing them to the public marketplace, they may knowingly ship products with bugs due to the fact that the time and cost required to fix all minor errors would prevent the product from ever being released as it would no longer be financially viable. However while these software errors and bugs are a source of many system quality problems, the most common cause is in fact data quality.
Quality of Life Impacts of Computers and Information Systems
Laudon and Laudon (2010) identified a number of quality of life impacts of computers and information systems as described below:
- Balancing power depicts the shift toward highly decentralised computing, coupled with an ideology of “empowerment” of workers and decentralisation of decision making to lower organisational levels. The problem with this idea is that the lower-level worker’s involvement in decision-making still tends to be minor or trivial. Key policy decisions largely remain as centralised as they were in the past.
- The rapidity of change impact suggests that information systems have increased the efficiency of the global marketplace. As a result of this efficiency, businesses no longer have many years to adjust to competition. This has the negative effect of many businesses being wiped out very rapidly before they can develop, meaning that jobs are lost.
- The maintaining boundaries impact proposes that the development of laptops and telecommuting have created a situation where people can take their work anywhere with them and do it at any time. This has negative connotations, for example workers may find that their work is cutting into family time, vacations and leisure, weakening the traditional institutions of family and friends and blurring the line between public and private life.
- The dependency and vulnerability impact indicates that businesses, governments, schools and private associations are becoming increasingly dependent on information systems leaving them highly vulnerable to the failure of those systems.
- The computer crime and abuse impact suggests that computers have created new medium for committing crimes and subsequently have themselves become the target of criminal acts.
- The employment impact implies that redesigning business processes may lead to countless middle level managers and clerical workers losing their jobs. Worse still, if the proposed re-engineering works as claimed, these workers will be unable to find similar employment as the need for their skills will decline.
- The equity and access impact proposes that access to computers and information resources, like wealth, is not equally distributed throughout society. Access is distributed inequitably along racial, economic and social class lines (in the same way as many other information resources).
- Health risks have been attributed to computers and information technologies. For instance, businesses are reported to now spend $20 billion a year to compensate and treat victims of computer-related occupational diseases. The most important occupational disease today is repetitive stress injury (RSI). The largest single source of RSI is considered to be computer keyboards. However, RSI is avoidable; workstations can be designed for a neutral wrist position, with a wrist rest to support the wrists, proper monitor stands and footrests. These measures collectively contribute to proper posture and reduced incidence of RSI and should be enhanced with frequent rest breaks and rotation of employees to different jobs.
