TUESDAY: 2 August 2022. Afternoon paper. Time Allowed: 2 hours.
Answer ALL questions. Each question is allocated two (2) marks.
1. The characteristic of valuable information that ensures that the information is correct by checking from many sources of the information is called?
A. Accuracy
B. Reliability
C. Verifiability
D. Relevant
2. _____________ is an integrated set of components for collecting, storing, and processing data and for providing information, knowledge, and digital products.
A. Data system
B. Digital system
C. Information system
D. Computerised system
3. A decision that is made by a manager in an organization through brainstorming and rules can be referred to as?
A. Unstructured decision
B. Structured decision
C. Semi structured decision
D. Complete decision
4. An unordered collection of elements that may contain duplicates is known as?
A. Set
B. Bag
C. List
D. Dictionary
5. Which of the following is NOT an emerging technology in databases?
A. Presentation and display by use of report generators
B. The mode of processing is parallel processing
C. Natural language user interfaces
D. The merging of data models with knowledge representation
6. The following is a characteristic of a weak entity.
A. It has a primary key
B. It is not dependent of the strong entity
C. It has a partial key
D. Weak entity always does not have a total participation
7. Which of the following are the correct steps of a business continuity planning process?
A. Preparedness-Prevention-Response-Recovery
B. Preparedness-Prevention-Recovery-Response
C. Prevention-Preparedness-Response-Recovery
D. Response-Prevention-Preparedness-Recovery
8. “The informative blue book in the modern library is placed on a shiny tall brown cabinet”. Which of the following CANNOT be used as an entity when modeling an Entity-Relationship-Diagram (ERD) as used in database design
A. Book
B. Tall
C. Library
D. Cabinet
9. Which of the following statement best describes invention?
A. Improvement to the existing ideas
B. A new creation never seen before
C. Modification of the exiting artefact
D. Transforming of an idea of an idea or resources into useful application
10. _____________ is the technique that allow data to be changed without affecting the applications that process it such as changing the way the database is physically stored and accessed without having to make corresponding changes to the way the database is perceived by the user
A. Data abstraction
B. Data isolation
C. Data independence
D. Data concurrency
11. Given the relation below, identify the correct option that matches the degree and tuples of the relation respectively
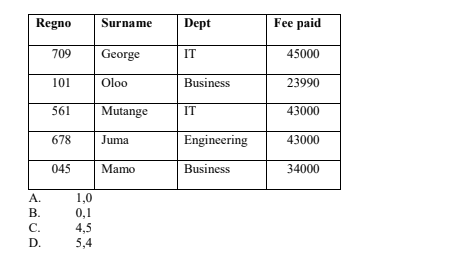
12. Which of the following best describe normalisation as used in database systems
A. It refers to the process where a relational database is restructured in a series known as normal forms designed
to reduce data redundancy and improve data integrity
B. It is a condition that occurs within a database or data storage technology in which, you can find the same
piece of data in two or more separate places
C. It is the process of attempting to optimise the performance of a database by adding redundant data or by
grouping data
D. It is a systematic process to design a database as it would require you to analyse all data requirements before
implementing your database
13. Which of the following statements about the Enterprise Data Warehouse is CORRECT?
A. It has normal
B. It is modelled using E-R modelling technique
C. It has de-normalised tables
D. It is used for online transactions processing
14. __________ is a centralised repository that allows you to store all your structured, semi-structured and unstructured data to store every type of data in its native format. Data is stored as-is, without having to first structure the data, and run different types of analytics
A. Data warehouse
B. Database
C. Data Lake
D. Data Mart
15. SQL allows the use of the absence of information about the value of an attribute. Select from the list below the SQL keyword that enables the absence
A. NIL
B. NULL
C. EMPTY
D. NOT
16. Which of the following is NOT an activity of a transaction processing system?
A. Order processing
B. Payments and receivables processing
C. Inventory records
D. Data analysis
17. The online analytical processing system where a relational database and multidimensional cubes divide the data is called
A. ROLAP
B. MOLAP
C. HOLAP
D. Data Lake
18. Suggest the statement that best describes the overall objective of the data warehouse
A. It enables users to run complex queries on data that transverse diverse enterprise areas
B. Escalates the productivity and effectiveness of decision-making in an organization
C. Used to organise store and store data relevant to enterprises everyday activities
D. It commands the structure of the schemas and tables in an organisation database system
19. Which of the following is a role of Data Manipulation Language as used in database systems?
A. Setting the indices to be used in each schema
B. The security and authorization of each schema
C. The number of rows may be increased or decreased
D. Grant permission to object created by one person to another
20. What name do we give to the condition that occurs when the same data exists in different formats in multiple tables
A. Data redundancy
B. Data inconsistency
C. Data Integrity
D. Data isolation
21. Which of the following term is applied to programming languages, design methods and database systems to mean providing support from constructs such as objects, classes, generalization and aggregation
A. Object modelling
B. Object class
C. Object-oriented
D. Object oriented data model
22. Multi-tenancy is an emerging trend in cloud computing, where a single database is shared by multiple parties Which of the following statement is NOT true about multi-tenancy?
A. Tenant cede to have the control of the database
B. Tenants are logically isolated but physically isolated
C. Tenants have full control of the database
D. The hosting is efficient with a low cost of maintenance
23. The process of extracting the common features from a group of object class and suppressing the detailed differences between the objects is referred to as
A. Inheritance
B. Aggregation
C. Cardinality
D. Generalisation
24. The relational database model that contains data about the dimensions in form of cubes mostly used for analytical purposes is called?
A. Semantic model
B. Flat model
C. Hierarchical model
D. Multidimensional model
25. The plan that focuses on how your organisation will recover and rebuild following any crisis is known as
A. Business continuity plan
B. Mitigation plan
C. Disaster recovery
D. Strategic plan
26. You are the operator of a database management system that is used to keep information about the employee’s payroll. You perform the calculations of the casual employees paid wages based on the number of days worked. Just before you post the record after calculation, you are required to verify the results. What state of the transaction are you in during the verification stage?
A. Partially committed
B. Committed
C. Active
D. Partially committed and committed
27. Which database object enables the request to access data from a database to manipulate it or retrieve it, allowing us to perform logic with the information is?
A. Form
B. Query
C. Report
D. View
28. Select the correct steps in a business re-engineering process
A. Create a visionpick the processfind a facilitatormanage change
B. Pick the process create a visionfind a facilitatormanage change
C. Find a facilitator pick the processcreate a vision manage change
D. Manage change pick the processcreate a vision find a facilitator
29. Which of the following is a component of a data warehouse as used in applications of database systems?
A. Volume of data
B. Operational data
C. Snowflake
D. Schema
30. The type of the key performance indicator reports focused predominantly on the day to day activities of an organisation is called
A. Strategic reports
B. Operational reports
C. Dashboard reports
D. Analytical report
31. The referential integrity constraints that automatically delete the dependent rows that correspond with the parent side row to be deleted is called______
A. Cascade
B. Set to null
C. Restrict
D. Set to default
32. Which of the following does NOT fall under the cyber-attack or data breaches as used in database security?
A. Malware
B. Phishing attacks
C. Ransom ware
D. Vandalism
33. You have been hired as a database engineer in a data science department in a banking institution. Highlight the data mining technique, that you recommend for use to determine if a particular credit card transaction may be either normal or fraudulent
A. Clustering
B. Association
C. Prediction
D. Classification
34. The information that includes information that describes the file such as the address of the file blocks on disk is called
A. File descriptor
B. Attributes
C. Properties
D. Metadata
35. Given the database schema: student (regno, surname, course, gender). Select the SQL statement to modify the relation and include a new attribute “feepaid”
A. UPDATE TABLE student ADD feepaid FLOAT
B. ALTER TABLE student ADD feepaid FLOAT
C. MODIFY TABLE student ALTER feepaid FLOAT
D. INSERT INTO TABLE student MODIFY feepaid FLOAT
36. What is the name given to the disk performance metric, that determines the speed at which data can be retrieved from or stored to the disk?
A. Access time
B. Latency
C. Seek time
D. Data-transfer rate
37. Which of the following statement is true about the in-memory database systems
A. It uses the disk-based technology
B. It degrades the performance of the system
C. It is faster than disk-based systems
D. It does not allow real-time analytical processing
38. What do we call, a means of expressing that the value of one particular attribute is associated with a single, specific value of another attribute?
A. Relationship
B. Aggregation
C. Functional dependency
D. Cascade
39. Which of the following is NOT a characteristic of an Enterprise Resource Planning System?
A. Real-time
B. Cross-functional
C. Integrated
D. Unilateral
40. ________________ is a transaction state whereby the transaction does not complete and none of its actions are reflected in the database
A. Commit
B. Abort
C. Redo
D. Failed
41. Which of the following property of a relation is CORRECT?
A. Relationship is named
B. There is a significance to order of tuples
C. Every Attribute must be multi valued
D. There is a significance to order of attributes
42. Choose the factor NOT to consider when choosing a database product
A. Budget
B. Availability of support
C. Compatibility with the existing technology
D. Customer taste
43. Modern databases are significant part of modern-day information systems. When developing such systems, we should put into considerations the type of data to be handled by the database system. Modern systems should handle complex data. Which of the following is not a complex data as used in trends in database technology?
A. Video
B. Schema
C. Audio
D. Images
44. Which if the following statements best describes the situation when vertical partitioning is necessary as used in database performance
A. It is used when different users need access to different records
B. It is used when different users need access to different attributes
C. It is used when different users need access to both records and columns
D. Used to distribute rows in several files
45. Data model enables the database to be treated as an abstract machine. There are various data models used in database systems. Which database model applies formal logic using propositions data elements to problems of data definition, manipulation and integrity
A. Relational data model
B. Deductive data model
C. Object-oriented data model
D. Semantic data model
46. Select the name given to the minimum number of times an instance in one entity can be associated with an instance in a related entity.
A. Relationship
B. Cardinality
C. Association
D. Modality
47. Denormalisation is a technique used in database design to allow the addition of duplicated data to relations. Which of the following is NOT an advantage of denormalisation in database systems?
A. Minimise joins in relational database
B. Decrease performance
C. Reducing the number of relations
D. Date retrieval is faster
48. The aggregate SQL function that returns the number of rows in a table satisfying the criteria specified in the WHERE clause is
A. GROUBY
B. COUNT
C. HAVING
D. CASE
49. The core component of the DBMS that interacts with the file system at an OS level to store data is called________
A. Query Processor
B. Log manager
C. Optimisation engine
D. Storage engine
50. Which of the following facts is TRUE about physical data independence as used in databases
A. It is concerned with conceptual schema
B. An example is deletion on an attribute
C. It is mainly concerned with the storage of data
D. It is concerned with the structure or changing the data definition
