
TOPIC: SIX: INTRODUCTION TO COMMUNICATION NETWORK
THEORY
Specific Objectives
By the end of this topic, the trainee should be able to:-
- Explain the meaning of a communication network
- Explain the uses and benefits of communication network
- Describe telecommunication technologies
- Describe the types of networks
- Describe network topologies
CONTENT
- Meaning of a communication network
- Uses and benefits of communication networks
- Telecommunication technology
- Types of networks
- Network topologies
Meaning of a communication network
A communication network can be defined as a set of devices (often referred to as nodes) connected by communication links and is used to transfer information between users located at various geographical points.
A communication network can also be defined as a collection of computers, printers and other equipment that is connected together so that they can communicate with each other. Using hardware and software, these interconnected computing devices can communicate with each other through defined rules of data communications. In a network, computers can exchange and share information and resources.
A computer network may operate on wired connections or wireless connections.
Uses/ benefits of communication networks
- Resource sharing. Resource sharing is one of the most popular uses of computer networks in the business applications. For Instance, a printer is shared in a network and hence saves a lot of investment in hardware. Other resources that can be shared include fax machines and modems
- File sharing. A network makes it easy for everyone to access the same file and prevents people from accidentally creating different versions of the same file.
- In a larger office, you can use e-mail and instant messaging tools to communicate quickly and to store messages for future reference.
- Collaboration A network allows employees to share files, view other people’s work, and exchange ideas more efficiently
- Organization: A variety of scheduling software is available that makes it possible to arrange meetings without constantly checking everyone’s schedules. This software usually includes other helpful features, such as shared address books and to-do lists
- Teleconferencing: Teleconferencing allows conferences to occur without the
participants being in the same place. Applications include video conferencing where participants can see as well as talk to one another - Mobile telephony: In the past two parties wishing to use the services of the
telephone company had to be linked by a fixed physical connection. Today’s cellular
networks make it possible to maintain wireless phone connections even while traveling
over large distances. - E-Business. E-business or electronic business refers to conducting business transactions on the internet, not only limited to buying and selling but also servicing customers and collaborating with business partners.
- Online Education. With network connections, online education is made possible. Students at any location around the world can participate in an online classroom, download tutorial questions and submit their assignments.
- E-Banking. E-banking or electronic banking is the most popular banking facility nowadays. It handles all types of banking transactions like account management, fund transfer and payments primarily over the internet. User can pay bills, check the account balance and transfer money to other parties, using e-banking facilities twenty four hours a day and seven days a week.
- Long Distance Communication. Long distance communication is made easy via network availability. Communication is possible via voice, text or video. The cost of having this type of communication is cheaper than making a normal phone call and definitely faster and more effective than corresponding via letters of fax.
- Centralized software management. Software can be loaded on one computer (the file server) eliminating that need to spend time and energy installing updates and tracking files on independent computers
- Workgroup computing. Workgroup software (such as Microsoft BackOffice) allows many users to work on a document or project concurrently
- Interactive entertainment
Disadvantages of networks
- Expensive Set Up: The initial set up cost of a computer network can be high depending on the number of computers to be connected. Costly devices like servers, routers, switches, hubs and cables can add up to the cost of installing a computer network.
- Managing a large network is complicated and requires hiring somebody with technical skills.
- Dependency on the Main File Server: In case the main File Server of a computer network breaks down, the system becomes useless. In case of big networks, the File Server should be a powerful computer, which often makes it expensive.
- Rapid Spread of Computer Viruses: If any computer system in a network gets affected by computer virus, there is a possible threat of other systems getting affected too. Viruses get spread on a network easily because of the interconnectivity of workstations. Such spread can be dangerous if the computers have important database which can get corrupted by the virus.
- There is a danger of hacking, particularly with wide area networks. Security procedures are needed to prevent such abuse, eg a firewall.
- As traffic increases on a network, the performance degrades unless the network is designed properly.
Types of Computer Networks
Below is a list of the most common types of computer networks.
Local area network (LAN)
A local area network is a computer network covering a small physical area, like a home, office, or small group of buildings, such as a school, or an airport. Current LANs are most likely to be based on Ethernet technology. For example, a library may have a wired or wireless LAN for users to interconnect local devices (e.g., printers and servers) and to connect to the internet.
A metropolitan area network (MAN)
A metropolitan area network is a network that connects two or more local area networks or campus area networks together but does not extend beyond the boundaries of the immediate town/city.
A wide area network (WAN)
A wide area network is a computer network that covers a broad area (i.e., any network whose communications links cross metropolitan, regional, or national boundaries. This is contrasted with personal area networks (PANs), local area networks (LANs), campus area networks (CANs), or metropolitan area networks (MANs) which are usually limited to a room, building, campus or specific metropolitan area (e.g., a city) respectively. The largest and most well-known example of a WAN is the Internet. A WAN is a data communications network that covers a relatively broad geographic area (i.e. one city to another and one country to another country) and that often uses transmission facilities provided by common carriers, such as telephone companies..
OTHERS
Other networks include the following:
A campus area network (CAN)
A campus area network is a computer network made up of an interconnection of local area networks (LANs) within a limited geographical area. It can be considered one form of a metropolitan area network, specific to an academic setting.
In the case of a university campus-based campus area network, the network is likely to link a variety of campus buildings including; academic departments, the university library and student residence halls. A campus area network is larger than a local area network but smaller than a wide area network (WAN).
Personal area network (PAN)
A personal area network is a computer network used for communication among computer devices close to one person. Some examples of devices that are used in a PAN are printers, fax machines, telephones, PDAs and scanners. The reach of a PAN is typically about 20-30 feet (approximately 6-9 meters).
Network topologies
Network topologies refer to the way in which computers in a network are linked together. It determines the data path that may be used between any two communicating computers in the network. The following are the common topologies
Bus Topology
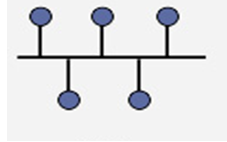
This is a network topology in which all the nodes are connected to a common transmission medium with two endpoints (this is the ‘bus’, which is also commonly referred to as the backbone or trunk). All data that is transmitted between nodes in the network is transmitted over this common transmission medium and is received by all nodes in the network simultaneously.
Note:
The two endpoints of the common transmission medium are normally terminated with a device called a terminator, which dissipates or absorbs the energy that remains in the signal to prevent the signal from being reflected back onto the transmission medium. Otherwise it causes interference resulting in degradation of the signals on the transmission medium.
Advantages of a Linear Bus Topology
- Easy to connect a computer or peripheral to a linear bus.
- Requires less cable length than a star topology.
Disadvantages of a Linear Bus Topology
- Entire network shuts down if there is a break in the main cable.
- Terminators are required at both ends of the backbone cable.
- Difficult to identify the problem if the entire network shuts down.
- Not meant to be used as a stand-alone solution in a large building.
Star
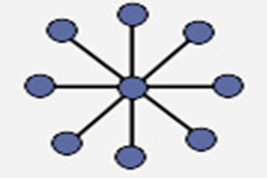
Also known as a star network, a star topology is one of the most common network setups where each of the devices and computers on a network connect to a central hub as shown in the diagram above.
Advantages
- A failure on one link does not affect other links as they use different routes.
- It provides shorter data paths. Since the central site is connected directly to the destination site, data does not have to travel through any intermediate sites, thus providing a shorter data path.
- It is also easier and less expensive to extend a star topology compared to the bus or ring topologies.
- Easy to detect faults and to remove parts.
Disadvantages
- Any failure at the central site or hub can cause the entire network to go down.
- In case the central connection point gets overloaded with data, the performance of the entire network gets affected.
- Requires more cable length than a linear topology.
- More expensive than linear bus topologies because of the cost of the central node
Ring
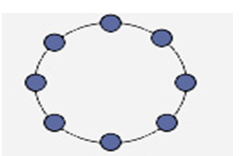
In a ring topology, each node in the network is connected to the next node forming a closed loop giving the appearance of a ring-like structure. Thus each device is connected directly to two other devices, one on each side of it. When this topology is used, it connects nodes using two parallel paths of data.
Advantages
- It also offers high bandwidth and can span long distances
Disadvantages
- It is expensive when it comes to expanding the topology
- It may also be difficult to install.
- Ring topology is suitable for only a few node
Tree
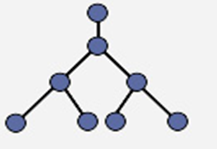
A tree topology combines characteristics of linear bus and star topologies. It consists of groups of star-configured workstations connected to a linear bus backbone cable (See fig. 4). Tree topologies allow for the expansion of an existing network, and enable schools to configure a network to meet their needs.
Advantages of a Tree Topology
- Point-to-point wiring for individual segments.
- Supported by several hardware and software venders.
Disadvantages of a Tree Topology
- Overall length of each segment is limited by the type of cabling used.
- If the backbone line breaks, the entire segment goes down.
- More difficult to configure and wire than other topologies.
Combined (Hybrid) (Check if it is similar to mesh topology)
Hybrid Topology
A hybrid topology is a combination of any two or more network topologies in such a way that the resulting network does not have one of the standard forms. For example, a tree network connected to a tree network is still a tree network, but two star networks connected together exhibit hybrid network topologies. A hybrid topology is always produced when two different basic network topologies are connected.
Advantage
Hybrid topology allows coexistence and cohabitation by integrating different network topologies to work together.
Disadvantage
it is costly to support and maintain them.
Telecommunications technology
Telecommunications is the exchange of information over significant distances by electronic means. Telecommunications technology includes anything used by humans to communicate information over a distance. The concept has been around since the early days of human history, when smoke signals and drums were used to inform a person or groups of people of an event or situation. However, major breakthroughs since the late 1800s have brought the field of telecommunications into the modern age. More recent developments include the telephone, radio, television, fax machine and computer, each with its own unique properties to benefit the information exchange of mankind.
A basic telecommunication system consists of three elements:
- a transmitter that takes information and converts it to a signal;
- a transmission medium that carries the signal; and,
- a receiver that receives the signal and converts it back into usable information.
Common Telecommunication Technologies
- Telephone
One of the most prevalent telecommunications devices is the phone, an instrument which transfers vocal information from place to place. Two main types of phones are used in modern society: the analog-based fixed-line telephone and the satellite-based cellular phone.
- Radio and Television
The broadcast system, which features the radio and television networks, uses a different format to transmit information. Both systems use electromagnetic waves that send audio and video information from one location to another. This can either be accomplished through an analog or digital method.
- Computer Networks
Networked computers are very common in the modern world and are either connected to a local-area network or the world wide web. This telecommunications technology allows users to send and receive a variety of formatted information such as text via emails or video with webcams. Different types of connections are available to make this technology function. Early connective techniques included fixed-line analog-to-digital modems, while newer methods including Ethernet lines and wireless connections utilizing electromagnetic waves.
Transmission Media
For effective communication to take place, communication media is required to connect the transmitter and the receiver. The diagram below gives a clear picture of different type of transmission media.
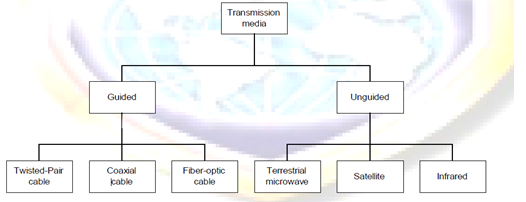
Guided Transmission Media
Guided/physical/non-wireless/bounded media have a physical link between sender and receiver. There are three categories of guided media: twisted-Pair, coaxial and fiber-optic.
Twisted-Pair Cable
A twisted consist of two conductors (usually copper), each with its own colored plastic insulation. In the past, two parallel wires were used for communication. However, electromagnetic interference from devices such as a motor can create over noise those wires. If the two wires are parallel, the wire closest to the source of the noise gets more interference than the wire further away. This results in an uneven load and a damaged signal.
If, however, the two wires are twisted around each other at regular intervals (between 2 to 12 twist per foot), each wire is closer to the noise source for half the time and the further away the other half. With the twisting interference can be equalized for both wires. Twisting does not always eliminate the impact of noise, but does significantly reduce it
Twisted cable comes in two forms: unshielded and shielded.
Unshielded Twisted Pair (UTP) cable
UTP consists of a number of twisted pairs with simple plastic casing. UTP is commonly used in telephone system.

Shielded Twisted Pair (STP) cable
STP includes shielding to reduce cross talk as well as to limit the effects of external interference. For most STP cables, this means that the wiring includes a wire braid inside the cladding or sheath material as well as a foil wrap around each individual wire. This shield improves the cable’s transmission and interference characteristics, which, in turn, support higher bandwidth over longer distance than UTP.

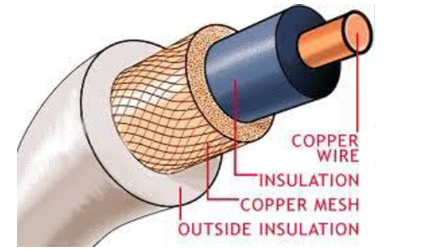
Coaxial Cable
Coaxial cable, commonly called coax, has two conductors that share the same axis. A solid copper wire runs down the center of the cable, and this wire is surrounded by plastic foam insulation. The foam is surrounded by a second conductor, wire mesh tube, metallic foil, or both. The wire mesh protects the wire from EMI. It is often called the shield. A tough plastic jacket forms the cover of the cable, providing protection and insulation.
Fiber Optic Cable: fiber optic cable transmits light signals rather than electrical signals. It is enormously more efficient than the other network transmission media. As soon as it comes down in price (both in terms of the cable and installation cost), fiber optic will be the choice for network cabling.
A light pulse can be used to signal a ‗1‘ bit; the absence of a pulse signals a ‗0‘ bit. Visible light has a frequency of about 108 MHz, so the bandwidth of an optical transmission system is potentially enormous.
An optical transmission system has three components: the transmission medium, the light source and the detector. The transmission medium is an ultra-thin fiber of glass or fused silica. The light source is either a LED (Light Emit Diode) or a laser diode, both of which emits light pulses when a electrical current is applied. The detector is a photo diode, which generates an electrical pulse when light falls on it.
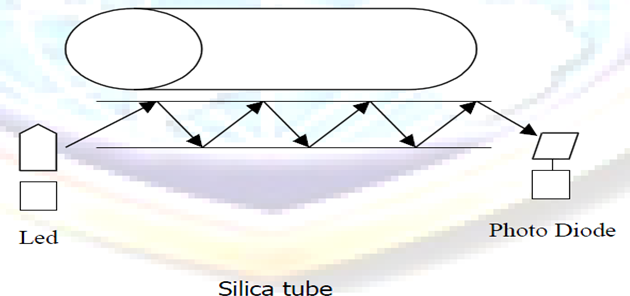
A cable may contain a single fiber, but often fibers are bundled together in the center of the cable. Optical fibre are smaller and lighter than copper wire. One optical fiber is approximately the same diameter as a human hair.
Advantages of Fiber Optic
- Noise resistance: it is immune to Electromagnetic Interference (EMI)
- Less signal attenuation: signal can run for miles without requiring regeneration
- Higher bandwidth: fiber optic cable can support dramatically higher bandwidths (and hence data rate) than all other cables. Currently, data rates and bandwidth utilization over fiber-optic cable are limited not by the medium but by the signal generation and reception technology available. A typical bandwidth for fiber optic is 100Mbps to 1Gbps.
Disadvantages of Fiber Optic
- Cost : most expensive among all the cables
- Installation / maintenance: is high
- Fragility : glass fiber is more easily broken than wire
Unguided Transmission Media
Unguided/non-physical/wireless/unbounded media have no physical link between sender and receiver.
There has been increasing need for mobile users to connect to a network. The answer for their needs is wireless. In wireless communications, space (air) is the medium for the signals.
Wireless networking has some advantages over wired networking:
- No wires needed. Running wires can be difficult in some cases; such as wiring an existing building, wiring between buildings, wiring across mountains, etc.
- Staying connected is important for mobile users. Wireless networks allow users stay connected more hours each day. Users with laptops may roam their work space without losing network connection and without logging into another machine. This increases the productivity of workers.
- Wireless networks can grow without much difficulty compared with wired networks. Making a wired network larger often involves wiring and usually costly.
- Wireless networks are not confined to an area. There is no long term commitment as in the wired networks.
Categories of unguided media
There are two categories of unguided media. These are:
- Radio transmission: These are systems for AM or FM radio. They are one form of communications and not used for computer networks.
- Microwave transmission: We can classify them into three categories; Terrestrial microwave, Satellite and Infra Transmission
Terrestrial Microwave
Microwaves do not follow the curvature of the earth therefore require line of sight transmission and reception equipment. The distance coverable by line of sight signals depends to a large extend on the height of the antenna: the taller the antenna, the longer the sight distance. Height allows the signals to travel farther without being stopped by the curvature of the earth and raises the signals above many surface obstacles, such as low hills and tall buildings that would otherwise block transmission.
Microwave signals propagate in one direction at a time, which means that two frequencies are necessary for two ways communication such as telephone communication. One frequency is reserved for transmission in one direction and other for transmission in other. Each frequency requires its own transmitter and receiver. Today, both pieces of equipment usually are combined in a single piece of equipment called transceiver, which allows a single antenna to serve both frequencies and functions.
Terrestrial microwave systems are typically used when using cabling is very costly and difficult to set.
Satellite Communication
Satellite transmission is much like line of sight microwave transmission in which one of the stations is a satellite orbiting the earth. The principle is the same as terrestrial microwave, with a satellite acting as a super-tall antenna and repeater. Although in satellite transmission signals must still travel in straight lines, the limitations imposed on distance by the curvature of the earth are reduced. In this way, satellite relays allow microwave signals to span continents and ocean with a single bounce.
Satellite microwave can provide transmission capability to and from any location on earth, no mater how remote. This advantage makes high quality communication available to undeveloped parts of the world without requiring a huge investment in ground based infrastructure. Satellite themselves are extremely expensive, of course, but leasing time or frequencies on one can be relatively cheap.
Infrared Transmission
Infrared media uses infrared light to transmit signals. LEDs transmit the signals, and photodiodes receive the signals. The remote control we use for television, VCR and CD player use infrared technology to send and receive signals.
Because infrared signals are in high frequency range, they have good throughput. Infrared signals do have a downside; the signals cannot penetrate walls or other objects, and they are diluted by strong light sources.
With any communication system, there is a high possibility that the signal that is received will differ from the signal that is transmitted as a result of various transmission impairments. For analog signals, these impairments introduce various random modifications that degrade the signal quality. For digital signals, bit errors are introduced: A binary 1 is transformed into a binary 0, and vice versa.
The most significant impairments are the following:
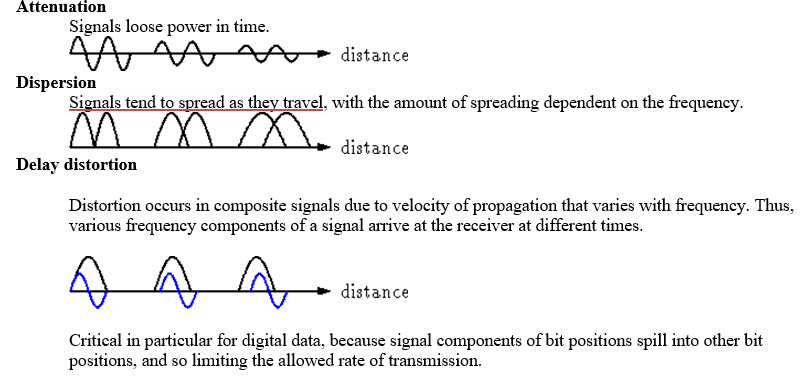
Noise
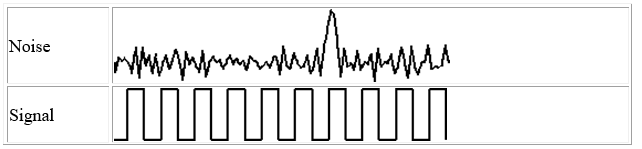
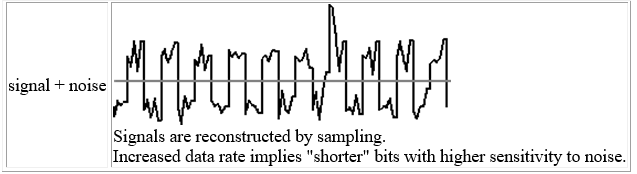
Noise refers to any unwanted signal. For any data transmission event, the received signal will consist of the transmitted signal, modified by the various distortions imposed by the transmission system, plus additional unwanted signals that are inserted somewhere between transmission and reception; the latter, undesired signals are referred to as noise-a major limiting factor in communications system performance.
TOPIC NINE: ICT ETHICS AND LEGISLATIONS
THEORY
Specific Objectives
By the end of this topic, the trainee should be able to:-
- Explain the meaning and importance of ICT ethics
- Describe unethical behavior in ICT
- Explain reasons for unethical behavior in ICT
- Explain the measures for controlling unethical behavior in ICT
- Explain the sources of ICT legislations
- Describe ICT legislations and policies
- Explain enforcement measures for ICT legislation and policies
CONTENT
- Meaning and importance of ICT ethics
- Unethical behavior in ICT
- Software piracy
- Unauthorized access
- others
- reasons for unethical behavior in ICT
- Measures for controlling unethical behavior in ICT
- Sources of ICT legislation
- ICT legislations and policies
- ICT policy
- Data Protection
- Copyright
- Information Privacy
- Others
- Enforcement measures for ICT legislation and policies
Meaning of ICT ethics
Ethics is a set of moral principles that govern the behavior of a group or individual. Therefore, ICT ethics is set of moral principles that regulate the use of ICT. Ethics
are grounded in the notion of responsibility (as free moral agents, individuals,
Organizations, and societies are responsible for the actions that they take) and
Accountability (individuals, organizations, and society should be held accountable
to others for the consequences of their actions).
The Importance of Ethics in ICT (Check)
Information is a source of power and, increasingly, the key to prosperity among those with access to it. Consequently, developments in ICT also involve social and political relationships. This makes ethical considerations on how important information is used.
Electronic systems now reach into all levels of government, into the workplace, and into private lives to such an extent that even people without access to these systems are affected in significant ways by them. New ethical and legal decisions are necessary to balance the needs and rights of everyone.
As in other new technological arenas, legal decisions lag behind technical developments. Ethics fill the gap as people negotiate how use of electronic information should proceed. The following notes define the broad ethical issues now being negotiated. Since laws deciding some aspects of these issues have been made, these notes should be read in conjunction with Legal Issues in Electronic Information Systems.
Unethical behavior in ICT
Unethical behavior in ICT is the incorrect use of ICT in a way that disturbs privacy of others or their intellectual property rights thereby creating ethical dilemmas. Unethical behavior in ICT includes:
- Software piracy
Software piracy is the unauthorized copying of software. Most retail programs are licensed for use at just one computer site or for use by only one user at any time. By buying the software, you become a licensed user rather than an owner. You are allowed to make copies of the program for backup purposes, but it is against the law to give copies to friends and colleagues. Another type of software piracy is software counterfeiting which occurs when fake copies of software are produced in such a way that they appear to be authentic.
- Unauthorized access or Hacking
Hacking or unauthorized access is breaking into computer systems, it entails approaching, trespassing within, communicating with, storing data in, retrieving data from, or otherwise intercepting and changing computer resources without consent. These break-ins may cause damage or disruption to computer systems or networks.
- Plagiarism check)
Plagiarism is the practice of taking someone else’s work or ideas and passing them off as one’s own. Plagiarism was around long before the Internet but the advent of the internet has increased cases of plagiarism and made it difficult to detect.
- Spamming
Spamming is flooding the Internet with many copies of the same message, in an attempt to force the message on people who would not otherwise choose to receive it. It is normally done through unsolicited bulk emails. Most spam is commercial advertising, often for dubious products, get-rich-quick schemes, or quasi-legal services.
Every time a “spammer” sends out email spam, the entire Internet community has to bear the cost, in particular the recipients and the ISPs at the receiving end. It wastes a lot of recipients’ time and disk space.
Spam also ties up bandwidth and resources on computers and routers all over the Internet. Every unwanted email message adds to the total cost of operating the networks of computers which form the Internet. Spam can disrupt a network by crashing mail servers and filling up hard drives. Spam also constitutes an invasion of Internet users’ online privacy.
- Phishing
Phishing is the act of sending an e-mail to a user falsely claiming to be an established legitimate enterprise in an attempt to trick the user into surrendering private information that will be used for identity theft. The e-mail directs the user to visit a Web site where they are asked to update personal information, such as passwords and credit card, social security, and bank account numbers, that the legitimate organization already has. The Web site, however, is bogus and set up only to steal the user information.
Reasons for unethical behavior in ICT
- Pressure can drive people to do things they wouldn’t normally do. For example pressure to meet unrealistic deadlines and expectations, from co-workers, bosses, or customers, can lead some people to engage in unethical activities or at least look the other way.
- Some people make unethical choices because they are ignorant of what really is the right thing to do. Often, ethical problems are complicated, and the proper choice may not be obvious.
- Some people behave unethically because of self-interest, need for personal gain, ambition or downright greed.
- Misguided loyalty is another reason for unethical conduct on the job. People sometimes lie because they think in doing so they are being loyal to the organization or to their bosses. For example, managers at automobile companies who hide or falsify information about defects that later cause accidents and kill people.
- There are those people who never learned or do not care about ethical values. Since they have no personal ethical values, they do not have any basis for understanding or applying ethical standards in their work. These people do not think about right and wrong. They only think, “What’s in it for me?” and “Can I get away with it?”
- Competition for scarce resources, power or position can also cause individuals to engage in unethical behaviors.
Measures for controlling unethical behavior in ICT
There azre a number of ways which managers can adopt to reduce unethical behavior in their organizations. These include:
- Hiring of individuals with high ethical standards;
- Establishing code of ethics and decision rules;
- Defining job goals and performance appraisal mechanism;
- Providing ethical training;
- Conducting social audits and providing support to individuals facing ethical dilemmas.
Sources of ICT legislation
Legislation is the laws governing everybody in a country while ICT legislation refers to the laws governing the ICT sector. In Kenya, the ICT sector is still emerging and there are no specific laws for the sector. However, there are several affecting the ICT sector in Kenya. These are:
- The following laws govern/affect the sector:
- Kenya Communications Act 1998
- Postal Corporation Kenya Act 1998
- Kenya Broadcasting Corporation Act
- The Telegraph Press Message Act 1983
- The Science & Technology Act
- State Corporations Act
- The Education Act
Draft legislation that is expected to be passed soon and which are likely to affect the ICT sector includes:
- Broadcasting Bill
- Freedom of Information
- Electronic Transaction bill
- Mobile Telephone Reprogramming
Other laws that are used to govern the sector include the ‘Common law’ and the ‘Statute law’ of the United Kingdom
ICT policy
A policy can be defined as a plan of action to guide decisions and actions. The term may apply to government, organizations and individuals. Policies in short can be understood as mechanisms arranged to reach explicit goals.
An ICT policy can therefore be defined as the rules and regulations set by the organization that determines the type of internal and external ICT resources employees can access, the kinds of programs they may install on their own computers as well as their authority for accessing network resources.
Benefits of policies
- i) Help save time
- ii) Help prevent managerial mistakes
iii) Improve consistency of decision making
- iv) Focus decisions towards business goals
Data Protection (Information Privacy)
Data Protection is achieved through the Data Protection Act. The Data Protection Act was developed to give protection and lay down the rules about how personal data can be used. It was created to protect individuals from misuse of this data. It governs the collection and processing of data by organizations and the individual rights to access the data if they wish.
Principles of Data Protection Act
- Data must be kept secure;
- Data stored must be relevant;
- Data stored must be kept no longer than necessary;
- Data stored must be kept accurate and up-to-date;
- Data must be obtained and processed lawfully;
- Data must be processed within the data subject rights;
- Data must be obtained and specified for lawful purposes;
- Data must not be transferred to countries without adequate data protection laws.
Copyright
Copyright is achieved through the Copyright, Design and Patents Act of 1988. This Act was introduced to protect people who have created original pieces of work like Books, Music, Films, Games and Applications, etc.
Two main purposes of the Act:
- To ensure people are rewarded for their endeavours.
- To give protection to the copyright holder if someone tries to steal their work.
The Act protects a wide range of work both written and computer based and Includes:
- Copying Software;
- Copying or Downloading music;
- Copying images or photographs from the Web;
- Copying text from web pages
The Computer Misuse Act
The Computer Misuse Act (1990) was introduced to secure computer material against unauthorised access or modification. Before this act was enacted, it was not possible to prosecute a ‘hacker’. Three categories of criminal offences were established to cover the following conduct:
- Unauthorised access to computer material (viewing data which you are not authorized to see).
- Unauthorised access with intent to commit or facilitate commission of further offences (hacking).
- Unauthorised modification of computer material.
Enforcement measures for ICT legislation and policies (Add)
