TOPIC FIVE: HARDWARE, SOFTWARE SELECTION AND ACQUISITION
THEORY
Specific Objective
By the end of this topic, the trainee should be able to:-
- Explain the meaning and importance of hardware, software selection and acquisition
- Describe factors considered in selection and acquisition
- Highlight procedure of selection and acquisition
- Describe methods of selection and acquisition
CONTENT
- Meaning and importance of hardware and software selection and acquisition
- Factors considered in hardware and software selection and acquisition
- Procedure of selection and acquisition of hardware and software
- Methods of hardware and software acquisition and selection
Meaning of hardware/ software selection and acquisition (check)
Hardware and software acquisition is the act of coming into possession of hardware and software solutions in an organization. It can also be referred to as gaining, procuring, securing or obtaining hardware and software. Includes but is not limited to buying, renting and leasing as well as accepting as a gift or donation.
Selection on the other hand refers to choosing the best solution from several alternatives.
Importance of hardware/software selection and acquisition (check)
The process of hardware/software selection and acquisition is important because it ensures that the organization acquires hardware/software:
- At the best possible price
- In the right quality
- At the right time
- From the right source
- That meets the users needs
Factors considered in hardware and software selection and acquisition
Hardware Selection Criteria
- Hardware must support current software as well as software planned for procurement in future
- Hardware must be compatible with existing or planned systems
- Hardware must be upgradeable and expandable to meet the future needs
- Hardware cost must be within the budget
- Hardware must be reliable
- Hardware vendor should be of high reputation
Software Selection Criteria
- Software must be compatible with current and future hardware needs
- Software must be user friendly
- Software vendor should provide user training
- Software vendor should be of high reputation
- Software vendor should provide user manuals
Software Procurement Procedures
- Software Specification
The first stage in procurement is to identify an organization’s need for a service or a product. Once a requirement has been identified, the specification is prepared. A specification defines the requirement in terms of performance, quality, quantity and timescales.
2. Determine Your Evaluation Criteria
To start the RFP process, determine what criterion you are going to evaluate the vendors proposals on and establish the weight each criterion will hold in relation to the others. Common criteria include experience, team strength, project understanding, differential advantage, and price. Evaluations based on established criterion will help to eliminate any situational bias that may occur.
An example of an evaluation criterion is shown in the table below:
| EVALUATION CRITERIA | |||
| Qualitative | Score | ||
| 1 | Supplier organization | ||
| (a)Stability | 5 | ||
| (b) Previous experience | 15 | ||
| (c) Support capability | 5 | ||
| Total Score 25 | |||
| 2 | Proposed Software | ||
| (a) Requirements | 35 | ||
| (b) Documentation | 10 | ||
| (c) Design | 10 | ||
| (d) Implementation | 10 | ||
| Total score 65 | |||
| 3 | Additional factors | ||
| (a) Compatibility | 5 | ||
| (b) Security | 3 | ||
| (c) User satisfaction | 2 | ||
| Total Score 10 | |||
The above is called a qualitative evaluation criterion as it is an assessment that partly depends on perception. The second part of evaluation is quantitative as it measures relative costs amongst the suppliers. An example of elements of cost analysis is shown below:
| Qualitative Analysis (Thousands of Units) | ||||
| Supplier Quotations | ||||
| A B C | ||||
| 1. Hardware | (a) Purchase cost | 2000 | 1890 | 2100 |
| (b) Installation cost | 500 | 620 | 480 | |
| Sub-total 2500 2510 2580 | ||||
| 2. Software | (a) Basic cost | 800 | 930 | 480 |
| (b) Modification costs | 160 | 50 | 430 | |
| (c) Annual maintenance | 144 | 147 | 137 | |
| (d) installation cost | 30 | 20 | 57 | |
| Sub-total 1134 1147 1105 | ||||
| 3. Additional costs | (a) Training | 100 | 90 | 80 |
| (b) General support | 40 | 150 | 100 | |
| Sub-total | 140 | 240 | 180 | |
| Grand Total 3774 3897 3865 | ||||
- Request for proposal (RFP)
The RFP is a solicitation process in which vendors are asked to submit sealed bids on a specific software. The RFP specifies what the buyer needs, how the buyer is going to evaluate the bids, and all the terms and conditions surrounding the subsequent contract.The RFP process brings structure to the procurement decision and allows the risks and benefits to be identified in advance.
An RFP typically involves more than a request for the price. Other requested information may include basic corporate information and history, financial information (can the company deliver without risk of bankruptcy), technical capability, product information and customer references that can be checked to determine a company’s suitability.
- Briefing conference
Often suppliers seek clarification or additional information. To ensure that no vendor is disadvantaged and that the same information is passed, a briefing conference is organized. This will be a formal session to answer questions from potential suppliers.
- Proposal Evaluation
It is advisable to perform evaluation in three stages.
The first stage is to eliminate suppliers/vendors who do not meet the most basic requirements leaving only those who qualify for more in-depth evaluation.
The second stage will be more comprehensive evaluation to determine a short-list of three or four suppliers. Finally, references may be taken up for short-listed potential suppliers with their existing clients. These references are useful as they provide an evaluation of the proposed software in a live environment.
References are done to determine overall satisfaction that existing clients have with the short-listed suppliers. The issues that should be addressed are:
- Ease of installation
- Ease of use
- Training
- Quality of documentation
- System efficiency
- 6. Selecting a vendor
After client references, the winning vendor is selected based on the evaluation and invited for contract negotiation.
- Contract Negotiation and signing
The negotiation process is the final stage of procurement. The main objective of contract negotiation is to work out a fair deal that will avoid litigation. It assumes that all the terms of the supplier are negotiable.
It is advisable to use a lawyer to revise the standard supplier agreement so as to develop specific issues relevant to the contract.
optional
The contract should cover the following:
- Currently purchased software and ‘optional’ software, documentation, manuals and source code (if applicable)
- If the software is being licensed, is the license non-exclusive and non-transferable?
- Does the contract cover all the future enhancements, updates and additions?
- How will the supplier resolve compatibility?
- Payment
The contract should take care of payment issues especially if the supplier requires non-refundable deposit
- Delivery
The contract should specify how software will be delivered, how and when will software be tested for performance. Appropriate insurance should be taken out to cover for any potential loss
- Acceptance testing
The key to successful acceptance testing is to develop, in advance, an objective method of defining compliance/non-compliance. This method should involve definition of technical standards against which the software can be measured. Some critical areas that can be incorporated into the performance specification are the degree to which software complies to technical requirements in RFP and how the client will attain redress if the test is not passed.
- Deliverables
The agreement should specify clearly the number of copies of the software that the supplier will deliver and the media of delivery. The type of documentation accompanying delivery should also be specified together with the number of documentation manuals.
- Warranty
Warranty is a period the supplier undertakes to remedy any faults found in the software without asking for a support contract. After this period the client must take out a support contract or pay for services. Warranty is negotiable and the buyer should tie it to product specification.
- Term and termination
The contract should define how long the contract will remain in force (term) and how it can be terminated
Hardware Procurement Procedures
- Hardware specification
In specifying hardware capacity, also called sizing, some of the most important features are: speed, storage capacity, connectivity and communication facilities.
Processor speed
The processor speed, measured in Hertz, defines the speed at which the computer performs specific instructions. The faster the computer can perform an instruction, the faster its response to users. Processor speeds are significant in a multi-user environment.
- Storage capacity/memory size
The size of memory, measured in bytes, will determine the size and the number of programs that the computer will run. The speed of the computer is very important if the computer is expected to make many programs available at the same time. The memory size must be adequate to support such processing environment. Storage capacity which is also measured in bytes, determines the amount of data and information that a computer can hold at a given time.
- Connectivity
Connectivity measures the number of input and output devices that can be connected to a computer. An organization should specify the total number of devices as these will affect the size of working storage required. A specific hardware model will also impose the maximum number of devices that can be connected.
- Communication facilities
Computers can provide different communication facilities. If necessary the facilities ought to be specified at the outset and the requirements defined. If these are not specified, there may be need to upgrade the computer by inserting cards at a later stage.
- Request for proposal (as above)
- Proposal Evaluation (as above)
Evaluation is done in three stages.
The first stage is to eliminate suppliers/vendors who do not meet the most basic requirements leaving only those who qualify for more in-depth evaluation.
The second stage will be more comprehensive evaluation to determine a short-list of three or four suppliers. Finally, references may be taken up for short-listed potential suppliers with their existing clients. These references are useful as they provide an evaluation of the proposed hardware in a live environment.
- Selecting a vendor (as above)
- Contract scope and negotiation
After selection of a suitable supplier, contract negotiation will commence. There are legal considerations which should be handled by a legal counsel. However the following matters which are of general nature should also be considered:
- Delivery
It should be specified clearly who meets the cost of delivery and who will be responsible if the hardware is damaged while on transit, between the buyer and the seller. In most cases the supplier takes out insurance for this purpose and may add this cost to the overall price of the hardware. Alternatively an organization may wish to avoid this cost by accepting responsibility for delivery from the supplier’s premises.
- Warranty period
Warranty period is a duration in which the supplier undertakes to replace or repair equipment in the event of a breakdown. It should be specified clearly and it should commence at the time of successful installation rather than delivery.
- Support considerations
Every computer system requires maintenance for both hardware and software which is traditionally provided by the supplier. The extent of support to be provided should be specified.
- Installation
Installation of hardware, especially for large computer systems, is often the responsibility of the supplier. However the installation of micro-computers can be undertaken by the user. It is important to specify who will be responsible. At the end of a successful installation the supplier will issue an installation certificate, whish in effect says that a warranty period has commenced.
- Training
The computer supplier frequently provides training to staff of an organisation to enable them use the computer. This form of training is, however, limited. An organisation should provide additional funds for further training.
Methods of hardware and software acquisition and selection (check)
The four methods of acquiring and / or financing the computer costs are;
- Rental
- Purchasing
- Leasing
- Using Bureaus
(a) Renting a computer
This is a very common arrangement of acquiring computer facilities. The computer facilities are acquired and installed for use within the aspiring user’s premises at fixed periodic charges, e.g. monthly charges, payable to the vendor. Most agreements have a minimum rental period, such as 90 days.
Advantages:
- Tax allowances are available.
- There is no large initial capital expenditure.
- The effects of technological changes are reduced, because during the agreement period, the charges are fixed hence inflation and maintenance are taken by the manufacturer and obsolete equipments can be returned to him.
- The user has more flexibility to change the equipment configuration.
Disadvantages
- This method of acquiring the computer and its related facilities is usually expensive in the long term, that is with time more computer varities and related facilities may be in market hence prices fall, but the rental charges remain fixed.
- The computer and the related facilities remain the assets of the manufacturer and hence can not be used by the renting company as a security e.g. while seeking loan facilities.
- In breach of the rental agreement , the computer and the related facilities may be repossessed by the manufacturer.
- The renting company usually pays more for any extra work done by the computer and its facilities, that was not covered in the rental agreement.
- Productivity of machine comes down with time but rental charges remain the same.
(b) Purchasing a computer
The buyer pays the supplier an amount equivalent to the computer and related facility’s value and the purchasing company owns the computer and the related facilities.
The payment can be in cash, through bank savings, loan arrangement or hire purchase arrangements. Whether it is straight purchase or through e.g. hire purchase the buying company gets the ownership of the facilities including the computer though in hire-purchase arrangement the ownership shall be limited to the extent payments are made. The computer and the related facilities therefore become full property of the buying company after all the installment payments are made.
Advantages:
- The computer and the related facilities become the assets of the buying company.
- It may be cheaper in the long term with tax advantages.
- Frequent expenditure is not expected, where the manufacturer enters maintenance agreement with the buying company.
- The company can decide to sell the computer and/ or related facilities to generate cash, which will depend on the market value of the facility to be sold.
- Since the company owns the computer and the related facilities, there are no extra charges for additional work done, as in renting.
Disadvantages
- In long term the computer and the related facilities may become obsolege, hence the organization suffers the loss, due to advancement in technology, Note that computer technology, advances fast generally, though it is dependent on the manufacturers of a particular computer family and amount of research.
- An organization acquires the computer and its related facilities in order to carry out its data processing tasks, which keep on changing. A good facility therefore will be that facility which is flexible to adapt to the current work load of the organization, it is a common situation where the work load is beyond or much below the computer configuration’s capabilities.
- There is large initial capital outlay but the returns are usually slow.
- Capital committed in purchasing the computer and its related facilities may be spent on other higher returning investments for the organization.
- Several other competing investment opportunities would have to be forgone in making the big cash outflow for purchasing the computer. The outflow would also reduce the company’s liquidity greatly. If use is made of loan facilities that would represent a liability in the balance sheet as also impose the burden of loan repayment and interest.
(c) Leasing a computer
The leasing company (Lessor), instals the computer and its facilities in the user’s (lessee’s) premises. The lessee then pays leasing charges to the lessor, who acquires the computer and its related facilities from the manufacturer and meets all the payments of the equipments values.
Leasing contracts are similar to rental contracts but usually for longer periods than those of renting. Leasing contract charges are low and renewable even at lower rates as compared to rental agreements.
Advantages
- Leasing agreements charges are lower than the rental charges, and the contracts are renewable even at lower rates unlike rental agreements.
- In leasing, the extra work load for the computer system is not charged for by the lessor.
- It does not require heavy initial investment.
- Lease expenditure being a revenue expense may be charged to the profit and loss account.
- Maintenance charges are included in the lease charges.
- Lease charges generally decline after a specified period.
Disadvantages
- Fixed charges are to be met.
- The computer and the related facilities may be repossessed by the lessor, in case the leasing contract is breached.
- The computer and the related facilities remain the assets of the lessor.
- Maintenance contracts may not be a guarantee, after a certain period of time, though the lessee may suffer inflexibility within the lease time e.g. when the equipments fail to adapt to the functional environments of the organisation. This aspect is, therefore, worth to clarify during the signing of the leasing contract between the lessee and the lessor. Note that maintenance contract is usually agreed on by the manufacturer for the leased equipment.
- In this arrangement of acquiring the computer and its facilities, the lessee has got no choice over such facilities, because the lessor acquires such facilities from the manufacturer of his choice.
- The primary period for leasing is usually much longer than the renting period.
- Using a bureaus
The methods of acquiring the computer equipments discussed so far i.e rental, purchasing, or leasing are used to acquire ‘in-house’ computer equipments that is the computer equipment is installed within the aspiring organization’s premises.
A bureau is an organization which renders computer services to, other companies which depend on such services, its clients. Computer bureaus can be companies, manufacturers, or users, with extra time to hire out, who work an aim of rendering services to the other companies.
Computer bureaus renders a wider cross section of the processing tasks for other organizations on either continuously or on demand basis.
Some of such services are:
- System analysis and design.
- Developing computer programs.
- Computer time hire out, and do-it-yourself.
- Advice and consultancy.
Notes:
The bureaus may undertake a full service to a given company, in the computer related services. Basically, all bureaus offer a wider cross section of the data processing services, though others may specialize on the industry, processing tasks or application type they deal with.
Advantages
- A company that is considering acquiring a computer may find it extremely beneficial to use a bureau because:
- It can evaluate the type of computer it is interested in.
- It can test and develop its programs prior to the delivery of its own computer.
- Its staff will become familiar with the requirements of a computer system.
- The major benefit of using data centre is that the user pays only for the information systems development and D.P. services that he needs. Installing in-house computer and employing staff of D.P. professionals creates fixed costs such as machine cost, rent, depreciation, salaries, etc.
- Many companies cannot justify the installation of an in-house computer on cost benefit grounds and the use of a bureau does not require a high capital outlay. Thus the computing services can be availed using a data centre and the organisation is not having sufficient finance for the installation of an in-house computer.
- Some computer users find it convenient to employ a bureau to cope with peak loads arising, for example, from seasonal variation in sales. Also if the organisation has insufficient volume of work to justify the installation of a computer, it can go for data centre.
- A bureau’s computer may be used in the event of a breakdown of an in-house machine.
- Enable the data processing to be done by the people who have the expertise.
- Obtain advice on all aspects of systems development and operation.
- Enable the client to obtain the user up-to-date computer technology, specialised equipment, and programs.
- However, there are also time-sharing vendors who provide for a fee the usage of central computer and online file storage to users who obtain access through remote terminals and telecommunication lines. Time-sharing vendors also generally offer a large number of specialized programs many of which the user may find to be strikingly applicable and useful.
- It avoids the responsibility of operating an in-house computer, i.e., it eliminates the personnel and management problems caused by the employment of a group of highly paid technical professionals in a rapidly changing and highly technical field of computer.
Disadvantages:
- The users of the bureau services have got no control over their jobs once they are submitted to the bureau.
- Periodic audit is necessary, because transportation of data and/or information from the organization to the bureau’s premises or vice versa, may pose problems e.g. fraud.
- Control by individual companies is difficult because processing goes on at a remote location.
- Documentation strictly adhered to, to ease the understanding of the systems, whose developers might not be available during the running of the systems. This is especially in a situation where the bureau develops and implements the systems.
- Confidential information’s security is at risk and the cost of using the bureau services should be carefully weighed out against the cost of using an in-house set up as an alternative. In most cases, the use of bureau services may be expensive, especially in the long term.
TOPIC SIX: COMPUTER PERSONNEL
THEORY
Specific Objective
By the end of this topic, the trainee should be able to describe the roles and skills requirements expected of various computer personnel
CONTENT
Roles and skills requirements of various computer personnel
- Computer programmers
- System analysts
- System designers
- Others
Attributes/ Skills necessary for Computer Personnel
- Analytical skills
These will enable systems analysts to understand the organization and its functions, which helps him/her to identify opportunities and to analyze and solve problems.
- Technical skills
Will help systems analysts understand the potential and the limitations of information technology. The systems analyst must be able to work with various programming languages, operating systems, and computer hardware platforms.
- Management skills
Will help systems analysts manage projects, resources, risk, and change.
- Interpersonal skills
Will help systems analysts work with end users as well as with analysts, programmers, and other systems professionals.
Responsibilities/Roles of a Computer Programmer
- The main role of computer programmer the development of programs.
- Programmers also correct errors by making appropriate changes and then rechecking the program to ensure that the desired results are produced.
- Another specific duty of a computer programmer is to perform monitoring tasks to ensure that the programs which they develop work as they are supposed to. This is done by reviewing programs on a frequent basis and making adjustments as are necessary to ensure the proper working of a computer program.
- The computer programmer may also be the individual who is responsible for providing technical support to those who use the computer programs developed by the individual and his/her company.
- Programmers compile and write documentation of program development and subsequent revisions, inserting comments in the coded instructions so others can understand the program.
- Consult with managerial, engineering, and technical personnel to clarify program intent, identify problems, and suggest changes.
- Perform or direct revision, repair, or expansion of existing programs to increase operating efficiency or adapt to new requirements.
Responsibilities/Roles of System Analyst (check)
- Interact with the customers to know their requirements
- Act as liaisons between vendors and the organization they represent.
- They are responsible for feasibility studies of a computer system before making recommendations to senior management.
- Perform system testing.
- Deploy the completed system.
- Research, plan, install, configure, troubleshoot, maintain and upgrade operating systems.
- Research, plan, install, configure, troubleshoot, maintain and upgrade hardware and software interfaces with the operating system.
- Research and recommend hardware and software development, purchase, and use.
- Troubleshoot and resolve hardware, software, and connectivity problems, including user access and component configuration.
- Write and maintain system documentation.
Responsibilities/Roles of a System Designer
- work with analysts on the feasibility of a conceptual design by taking technical specifications prepared by the analyst and designing system components to meet the set requirements
- draw up detailed design documentation including charts and diagrams that indicate the various components involved
- prepare instructions for programmer implementation
- talk with other team members (analysts and programmers) to ensure functionality according to systems specifications, and develop solutions as problems or issues arise
- design monitoring and performance measurement processes.
- The system designer is also responsible for writing the test plans and co-ordinating with a team of user and system testers to ensure that the system is thoroughly tested.
Responsibilities/Roles of a System Administrator
- Create new users
- Resetting user passwords
- Lock/unlock user accounts
- Monitor server security
- Install, support, maintain and monitor servers or other computer systems
- Plan for and respond to service outages and other problems.
- Install software
- Create a backup and recover policy
- Monitor network communication
- Update system as soon as new version of OS and application software comes out
- Implement the policies for the use of the computer system and network
- Setup security policies for users. A system admin must have a strong grasp of computer security (e.g. firewalls and intrusion detection systems).
- Monitor system performance
Responsibilities/Roles of the Network Administrator
- Designing and planning the network by making choices about network structure and networking protocols
- Setting up the network
- Maintaining the network
- Expanding the network
- making resources available on the network by:
- keeping the network running smoothly by:
- monitoring activity on the network and tuning performance
- troubleshooting the network
Responsibilities/Roles of a Database Administrator (check)
A database administrator’s responsibilities can include the following tasks:[6]
- Installing and upgrading the database server and application tools
- Allocating system storage and planning future storage requirements for the database system
- Modifying the database structure, as necessary, from information given by application developers
- Enrolling users and maintaining system security
- Ensuring compliance with database vendor license agreement
- Controlling and monitoring user access to the database
- Monitoring and optimizing the performance of the database
- Planning for backup and recovery of database information
- Maintaining archived data
- Backup|Backing up and restoring databases
- Contacting database vendor for technical support
- Generating various reports by querying from database as per need.
TOPIC SEVEN: COMPUTER SAFETY AND ERGONOMICS
Check the downloads
THEORY
Specific Objectives
By the end of this topic, the trainee should be able to:-
- Describe the meaning and importance of computer safety and ergonomics
- Describe computer safety
- Explain computer ergonomics
CONTENT
Meaning and importance of computer safety and ergonomics
Computer safety
- Hardware safety
- Software safety
- Data safety
Computer ergonomics
PRACTICE
Specific Objectives
By the end of this topic, the trainee should be able to demonstrate ergonomic use of computers
CONTENT
Trainee to demonstrate ergonomic use of computers
Meaning and importance of computer safety and ergonomics
Ergonomics is the science of adapting the job and/or the equipment and the human to each other for optimal safety and productivity. In basic language, ergonomics is the study of fitting the job to the worker rather than the worker to the job.
Computer ergonomics therefore means the designing machines, tools, and work environments to best accommodate human performance and behaviour. It aims to improve the practicality, efficiency, and safety of a person working with computer devices.
The use of computers has greatly increased over the last few decades. People now use computers and keyboards as a daily way of communicating, working, and even for entertainment. A condition known as Repetitive Strain Injury (RSI) has now been recognized as a result of the repetitive motion of typing and sitting in a fixed position (i.e. at a desk for eight hours). This can cause significant injury and pain to the arms, elbows, fingers, and wrists. This condition is extremely painful and can affect everyone from sedentary people to those who are active and physically fit.
Preventing RSI
- Taking regular breaks from working at your computer – a few minutes at least once an hour
- Alternating work tasks
- Regular stretching to relax your body
- Use equipment such as footrests, wrist rests and document holders if need be
- Keeping your mouse and keyboard at the same level
- Avoid gripping your mouse too tightly. You should hold the mouse lightly and click gently
- Familiarize yourself with keyboard shortcuts for applications you regularly use (to avoid overusing the mouse)
- Place your document at about the same height as the computer screen and make sure it’s close enough to the screen so you don’t have to look back and forth
- Adjust you chair so the bottom of your feet reach and rest comfortable on the floor and the back of your knees are slightly higher than the chairs’s seat.
- Adjust your screen to your height. The screen’s top viewing line should be no higher than your eyes and 18 – 24 inches from our face.
- Position your keyboard properly. It should be placed on a lower-than-normal work surface in order to keep the arms in a downward position and not interfere with the blood flow to the hands and fingers. Forearms should be parallel to the floor and wrist in line with the forearm.
- Organize your workstation so everything you need is within comfortable reach
Eyestrain
Another safety concerns resulting from use of computers is eyestrain.
Most computer-related eyestrain is caused by improper lighting. While you may not be able to do much about the overhead lighting, you can take these steps to minimize eyestrain:
- Exercising the eyes by periodically focusing on objects at varying distances
- Blinking regularly
- Keeping the air around you moist – for example using plants, open pans of water or a humidifier (spider plants are said to be particularly good for this and removing chemical vapours from the air)
- Adjusting the screen height / seating so that when sitting comfortably your eyes are in line with the top of the monitor screen
- Adjusting the brightness control on your monitor for comfort
- Adjusting the contrast on your monitor to make the characters distinct from the background
- Adjusting the refresh rate of your monitor to stop it flickering
- Positioning monitors to avoid glare (e.g. not directly in front of windows)
- Keeping your monitor clean
- Keeping the screen and document holder (if you use one) at the same distance from your eyes
- Servicing, repairing or replacing monitors that flicker or have inadequate clarity
- Regular eye testing
It is also important to have your workstation set up correctly or use ergonomically designed gadgets.
Monitors should:
- Rotate, tilt and elevate – if not use an adjustable stand, books or blocks to adjust the height
- Be positioned so the top line of the monitor is no higher than your eyes or no lower than 20° below the horizon of your eyes or field of vision
- Be at the same level and beside the document holder if you use one
- Be between 18 to 24 inches away from your face
Ergonomic Keyboards should:
- Be detachable and adjustable (with legs to adjust angle)
- Allow your forearms to be parallel to the floor without raising your elbows
- Allow your wrists to be in line with your forearms so your wrists does not need to be flexed up or down
- Include enough space to rest your wrists or should include a padded detachable wrist rest (or you can use a separate gel wrist rest which should be at least 50 mm deep)
- Be placed directly in front of the monitor and at the same height as the mouse, track ball or touch pad
Ergonomic mouse should have:
- The shape and size of the mouse should fit comfortably in the hand.
- You should have the ability to hold the mouse in a neutral position, i.e., your hand should not be bent at any awkward position.
- The mouse should be placed in such a way so that it can be used with your upper arm comfortably relaxed, and as near your body as possible, and without you having to reach towards the side or forwards for it.
Ergonomic Chairs should:
- Support the back – and have a vertically adjustable independent back rest that returns to its original position and has tilt adjustment to support the lower back
- Allow chair height to be adjusted from a sitting position
- Be adjusted so the back crease of the knee is slightly higher than the pan of the chair (use a suitable footrest where necessary)
- Be supported by a five prong caster base
- Have removable and adjustable armrests
- Have a contoured seat with breathable fabric and rounded edges to distribute the weight and should be adjustable to allow the seat pan to tilt forward or back
Ergonomic Tables and desks should:
- Provide sufficient leg room and preferably be height adjustable
- Have enough room to support the computer equipment and space for documents
- Be at least 900 mm deep
- Have rounded corners and edges
Computer Hardware Safety (check)
A phenomenal amount of information now resides on computers. Individual computers as well as computers on networks contain billions of pages of text, graphics, and other sources of information. Without safeguards, this information is vulnerable to misuse or theft.
Hardware security protects the machine and peripheral hardware from theft and from electronic intrusion and damage. The following are some of the measures to ensure hardware security:
- Physical Security
- Physical on-site security can be provided by confining mission-critical computers like servers to a locked room, and restricting access to only those who are authorized.
- Securing the physical perimeters of the room where the computer systems is kept is also necessary.
- Ensuring only a single entrance is used to the computer room
- Use of a strong lock on the door
- Control access to the computer room using measures like:
- access monitoring through badge-based entry
- security guard at the building entrance,
- Restriction of
- unscheduled visits,
- Surveillance cameras around the building and at each entrance.
- Access monitoring through biometric devices like fingerprint readers, voice recognition systems and iris readers
- Fire Protection
- Smoke detectors are usually installed to provide early warning of a developing fire by detecting particles generated by smoldering components prior to the development of flame. This allows investigation, interruption of power, and manual fire suppression using hand held fire extinguishers before the fire grows to a large size.
- Hand-held fire extinguishers should be within close reach of the computers
- Automatic fire sprinkler system is often provided to control a full scale fire if it develops.
- Various materials within computer rooms can enhance the magnitude of fires. Create a non-combustible environment to decrease risk of fire and help ensure that if a fire does begin it will not spread quickly. If furnishings are necessary in the computer area, guarantee they are made of non-combustible materials. Also, try to keep papers outside of the computer room as they would quickly amplify any fire that begins within the space.
- Perform regular testing on the safety equipment. For example, check the gauges of the fire extinguishers to see whether they need to be recharged. Re-train staff often on how to properly use the extinguishers and bring in professionals to ensure the devices are still in working order.
- Ensure that there is a plan in place for staff to follow if there is a fire. Perform fire drills to keep the plan fresh in the minds of employees.
Computer software safety
- Use only genuine software
- Install antivirus software on your computer
- Keep your antivirus software updated.
- If you have an antivirus software you should have a scan at least once a day on your computer so that the software can remove viruses
- Don’t open any e-mails if you don’t know who sent them.
- Never open email attachments unless you know with certainty that the attachment is something you expected and want to receive.
- Install or turn on the firewall to protect your computer against automatic network virus attacks.
Data Safety/Security
Data security is the practice of keeping data protected from corruption and unauthorized access. The focus behind data security is to ensure privacy while protecting personal or corporate data.
Data could be anything of interest that can be read or otherwise interpreted in human form.
The unauthorized access of this data could lead to numerous problems for both organizations and individual. Having your bank account details stolen is just as damaging as the system administrator who has had client information stolen from the database.
There has been a huge emphasis on data security as of late, largely because of the internet. There are a number of options for ensuring safety of your data and they include:
Encryption
Encryption has become a critical security feature for thriving networks and active home users alike. This security mechanism uses mathematical schemes and algorithms to scramble data into unreadable text. It can only by decoded or decrypted by the party that possesses the associated key.
Strong User Authentication
Authentication is another part of data security that we encounter with everyday computer usage. Just think about when you log into your email or blog account. That single sign-on process is a form of authentication that allows you to log into applications, files, folders and even an entire computer system. Once logged in, you have various given privileges until logging out. Some systems will cancel a session if your machine has been idle for a certain amount of time, requiring that you prove authentication once again to re-enter.
Use of Passwords
Sensitive data should always be protected by a password which should be chosen wisely. Unfortunately, many users choose weak passwords that provide little protection against the experienced hacker. A strong password contains more than eight characters which are a combination of letters (both upper case and lower case), symbols or numbers.
Backup Solutions
Data security wouldn’t be complete without a solution to backup your critical information. Though it may appear secure while confined away in a machine, there is always a chance that your data can be compromised. You could suddenly be hit with a malware infection where a virus destroys all of your files or a hacker can get access to your computer and corrupt/ steal data your data. If all else fails, a reliable backup solution will allow you to restore your data instead of starting completely from scratch. It is also important that you also keep a copy of your backup solution off-site in a secure location.
TOPIC: EIGHT: INTRODUCTION TO COMMUNICATION NETWORK
THEORY
Specific Objectives
By the end of this topic, the trainee should be able to:-
- Explain the meaning of a communication network
- Explain the uses and benefits of communication network
- Describe telecommunication technologies
- Describe the types of networks
- Describe network topologies
CONTENT
- Meaning of a communication network
- Uses and benefits of communication networks
- Telecommunication technology
- Types of networks
- Network topologies
Meaning of a communication network
A communication network can be defined as a set of devices (often referred to as nodes) connected by communication links and is used to transfer information between users located at various geographical points.
A communication network can also be defined as a collection of computers, printers and other equipment that is connected together so that they can communicate with each other. Using hardware and software, these interconnected computing devices can communicate with each other through defined rules of data communications. In a network, computers can exchange and share information and resources.
A computer network may operate on wired connections or wireless connections.
Uses/ benefits of communication networks
- Resource sharing. Resource sharing is one of the most popular uses of computer networks in the business applications. For Instance, a printer is shared in a network and hence saves a lot of investment in hardware. Other resources that can be shared include fax machines and modems
- File sharing. A network makes it easy for everyone to access the same file and prevents people from accidentally creating different versions of the same file.
- In a larger office, you can use e-mail and instant messaging tools to communicate quickly and to store messages for future reference.
- Collaboration A network allows employees to share files, view other people’s work, and exchange ideas more efficiently
- Organization: A variety of scheduling software is available that makes it possible to arrange meetings without constantly checking everyone’s schedules. This software usually includes other helpful features, such as shared address books and to-do lists.
- Teleconferencing: Teleconferencing allows conferences to occur without the
participants being in the same place. Applications include video conferencing where participants can see as well as talk to one another
- Mobile telephony: In the past two parties wishing to use the services of the
telephone company had to be linked by a fixed physical connection. Today’s cellular
networks make it possible to maintain wireless phone connections even while traveling
over large distances. - E-Business. E-business or electronic business refers to conducting business transactions on the internet, not only limited to buying and selling but also servicing customers and collaborating with business partners.
- Online Education. With network connections, online education is made possible. Students at any location around the world can participate in an online classroom, download tutorial questions and submit their assignments.
- E-Banking. E-banking or electronic banking is the most popular banking facility nowadays. It handles all types of banking transactions like account management, fund transfer and payments primarily over the internet. User can pay bills, check the account balance and transfer money to other parties, using e-banking facilities twenty four hours a day and seven days a week.
- Long Distance Communication. Long distance communication is made easy via network availability. Communication is possible via voice, text or video. The cost of having this type of communication is cheaper than making a normal phone call and definitely faster and more effective than corresponding via letters of fax.
- Centralized software management. Software can be loaded on one computer (the file server) eliminating that need to spend time and energy installing updates and tracking files on independent computers
- Workgroup computing. Workgroup software (such as Microsoft BackOffice) allows many users to work on a document or project concurrently
- Interactive entertainment
Disadvantages of networks
- Expensive Set Up: The initial set up cost of a computer network can be high depending on the number of computers to be connected. Costly devices like servers, routers, switches, hubs and cables can add up to the cost of installing a computer network.
- Managing a large network is complicated and requires hiring somebody with technical skills.
- Dependency on the Main File Server: In case the main File Server of a computer network breaks down, the system becomes useless. In case of big networks, the File Server should be a powerful computer, which often makes it expensive.
- Rapid Spread of Computer Viruses: If any computer system in a network gets affected by computer virus, there is a possible threat of other systems getting affected too. Viruses get spread on a network easily because of the interconnectivity of workstations. Such spread can be dangerous if the computers have important database which can get corrupted by the virus.
- There is a danger of hacking, particularly with wide area networks. Security procedures are needed to prevent such abuse, eg a firewall.
- As traffic increases on a network, the performance degrades unless the network is designed properly.
Types of Computer Networks
Below is a list of the most common types of computer networks.
Local area network (LAN)
A local area network is a computer network covering a small physical area, like a home, office, or small group of buildings, such as a school, or an airport. Current LANs are most likely to be based on Ethernet technology. For example, a library may have a wired or wireless LAN for users to interconnect local devices (e.g., printers and servers) and to connect to the internet.
A metropolitan area network (MAN)
A metropolitan area network is a network that connects two or more local area networks or campus area networks together but does not extend beyond the boundaries of the immediate town/city.
A wide area network (WAN)
A wide area network is a computer network that covers a broad area (i.e., any network whose communications links cross metropolitan, regional, or national boundaries. This is contrasted with personal area networks (PANs), local area networks (LANs), campus area networks (CANs), or metropolitan area networks (MANs) which are usually limited to a room, building, campus or specific metropolitan area (e.g., a city) respectively. The largest and most well-known example of a WAN is the Internet. A WAN is a data communications network that covers a relatively broad geographic area (i.e. one city to another and one country to another country) and that often uses transmission facilities provided by common carriers, such as telephone companies..
OTHERS
Other networks include the following:
A campus area network (CAN)
A campus area network is a computer network made up of an interconnection of local area networks (LANs) within a limited geographical area. It can be considered one form of a metropolitan area network, specific to an academic setting.
In the case of a university campus-based campus area network, the network is likely to link a variety of campus buildings including; academic departments, the university library and student residence halls. A campus area network is larger than a local area network but smaller than a wide area network (WAN).
Personal area network (PAN)
A personal area network is a computer network used for communication among computer devices close to one person. Some examples of devices that are used in a PAN are printers, fax machines, telephones, PDAs and scanners. The reach of a PAN is typically about 20-30 feet (approximately 6-9 meters).
Network topologies
Network topologies refer to the way in which computers in a network are linked together. It determines the data path that may be used between any two communicating computers in the network. The following are the common topologies
Bus Topology
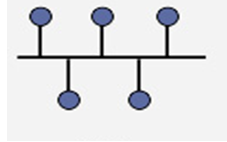
This is a network topology in which all the nodes are connected to a common transmission medium with two endpoints (this is the ‘bus’, which is also commonly referred to as the backbone or trunk). All data that is transmitted between nodes in the network is transmitted over this common transmission medium and is received by all nodes in the network simultaneously.
Note:
The two endpoints of the common transmission medium are normally terminated with a device called a terminator, which dissipates or absorbs the energy that remains in the signal to prevent the signal from being reflected back onto the transmission medium. Otherwise it causes interference resulting in degradation of the signals on the transmission medium.
Advantages of a Linear Bus Topology
- Easy to connect a computer or peripheral to a linear bus.
- Requires less cable length than a star topology.
Disadvantages of a Linear Bus Topology
- Entire network shuts down if there is a break in the main cable.
- Terminators are required at both ends of the backbone cable.
- Difficult to identify the problem if the entire network shuts down.
- Not meant to be used as a stand-alone solution in a large building.
Star
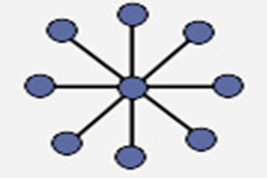
Also known as a star network, a star topology is one of the most common network setups where each of the devices and computers on a network connect to a central hub as shown in the diagram above.
Advantages
- A failure on one link does not affect other links as they use different routes.
- It provides shorter data paths. Since the central site is connected directly to the destination site, data does not have to travel through any intermediate sites, thus providing a shorter data path.
- It is also easier and less expensive to extend a star topology compared to the bus or ring topologies.
- Easy to detect faults and to remove parts.
Disadvantages
- Any failure at the central site or hub can cause the entire network to go down.
- In case the central connection point gets overloaded with data, the performance of the entire network gets affected.
- Requires more cable length than a linear topology.
- More expensive than linear bus topologies because of the cost of the central node
Ring
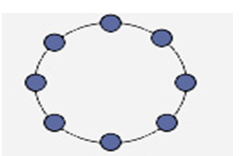
In a ring topology, each node in the network is connected to the next node forming a closed loop giving the appearance of a ring-like structure. Thus each device is connected directly to two other devices, one on each side of it. When this topology is used, it connects nodes using two parallel paths of data.
Advantages
- It also offers high bandwidth and can span long distances
Disadvantages
- It is expensive when it comes to expanding the topology
- It may also be difficult to install.
- Ring topology is suitable for only a few node
Tree
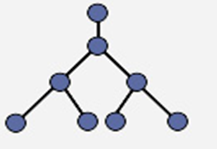
A tree topology combines characteristics of linear bus and star topologies. It consists of groups of star-configured workstations connected to a linear bus backbone cable (See fig. 4). Tree topologies allow for the expansion of an existing network, and enable schools to configure a network to meet their needs.
Advantages of a Tree Topology
- Point-to-point wiring for individual segments.
- Supported by several hardware and software venders.
Disadvantages of a Tree Topology
- Overall length of each segment is limited by the type of cabling used.
- If the backbone line breaks, the entire segment goes down.
- More difficult to configure and wire than other topologies.
Combined (Hybrid) (Check if it is similar to mesh topology)
Hybrid Topology
A hybrid topology is a combination of any two or more network topologies in such a way that the resulting network does not have one of the standard forms. For example, a tree network connected to a tree network is still a tree network, but two star networks connected together exhibit hybrid network topologies. A hybrid topology is always produced when two different basic network topologies are connected.
Advantage
Hybrid topology allows coexistence and cohabitation by integrating different network topologies to work together.
Disadvantage
it is costly to support and maintain them.
Telecommunications technology
Telecommunications is the exchange of information over significant distances by electronic means. Telecommunications technology includes anything used by humans to communicate information over a distance. The concept has been around since the early days of human history, when smoke signals and drums were used to inform a person or groups of people of an event or situation. However, major breakthroughs since the late 1800s have brought the field of telecommunications into the modern age. More recent developments include the telephone, radio, television, fax machine and computer, each with its own unique properties to benefit the information exchange of mankind.
A basic telecommunication system consists of three elements:
- a transmitter that takes information and converts it to a signal;
- a transmission medium that carries the signal; and,
- a receiver that receives the signal and converts it back into usable information.
Common Telecommunication Technologies
- Telephone
One of the most prevalent telecommunications devices is the phone, an instrument which transfers vocal information from place to place. Two main types of phones are used in modern society: the analog-based fixed-line telephone and the satellite-based cellular phone.
- Radio and Television
The broadcast system, which features the radio and television networks, uses a different format to transmit information. Both systems use electromagnetic waves that send audio and video information from one location to another. This can either be accomplished through an analog or digital method.
- Computer Networks
Networked computers are very common in the modern world and are either connected to a local-area network or the world wide web. This telecommunications technology allows users to send and receive a variety of formatted information such as text via emails or video with webcams. Different types of connections are available to make this technology function. Early connective techniques included fixed-line analog-to-digital modems, while newer methods including Ethernet lines and wireless connections utilizing electromagnetic waves.
Transmission Media
For effective communication to take place, communication media is required to connect the transmitter and the receiver. The diagram below gives a clear picture of different type of transmission media.
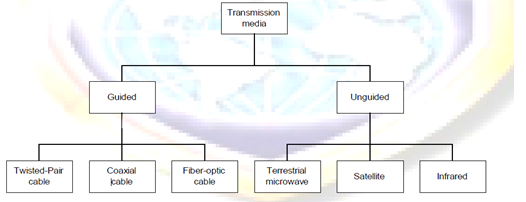
Guided Transmission Media
Guided/physical/non-wireless/bounded media have a physical link between sender and receiver. There are three categories of guided media: twisted-Pair, coaxial and fiber-optic.
Twisted-Pair Cable
A twisted consist of two conductors (usually copper), each with its own colored plastic insulation. In the past, two parallel wires were used for communication. However, electromagnetic interference from devices such as a motor can create over noise those wires. If the two wires are parallel, the wire closest to the source of the noise gets more interference than the wire further away. This results in an uneven load and a damaged signal.
If, however, the two wires are twisted around each other at regular intervals (between 2 to 12 twist per foot), each wire is closer to the noise source for half the time and the further away the other half. With the twisting interference can be equalized for both wires. Twisting does not always eliminate the impact of noise, but does significantly reduce it
Twisted cable comes in two forms: unshielded and shielded.
Unshielded Twisted Pair (UTP) cable
UTP consists of a number of twisted pairs with simple plastic casing. UTP is commonly used in telephone system.

Shielded Twisted Pair (STP) cable
STP includes shielding to reduce cross talk as well as to limit the effects of external interference. For most STP cables, this means that the wiring includes a wire braid inside the cladding or sheath material as well as a foil wrap around each individual wire. This shield improves the cable’s transmission and interference characteristics, which, in turn, support higher bandwidth over longer distance than UTP.

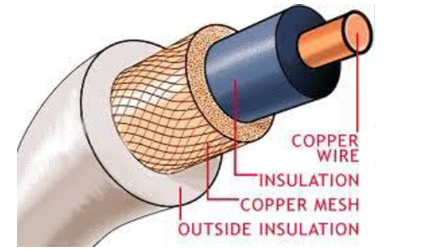
Coaxial Cable
Coaxial cable, commonly called coax, has two conductors that share the same axis. A solid copper wire runs down the center of the cable, and this wire is surrounded by plastic foam insulation. The foam is surrounded by a second conductor, wire mesh tube, metallic foil, or both. The wire mesh protects the wire from EMI. It is often called the shield. A tough plastic jacket forms the cover of the cable, providing protection and insulation.
Fiber Optic Cable: fiber optic cable transmits light signals rather than electrical signals. It is enormously more efficient than the other network transmission media. As soon as it comes down in price (both in terms of the cable and installation cost), fiber optic will be the choice for network cabling.
A light pulse can be used to signal a ‗1‘ bit; the absence of a pulse signals a ‗0‘ bit. Visible light has a frequency of about 108 MHz, so the bandwidth of an optical transmission system is potentially enormous.
An optical transmission system has three components: the transmission medium, the light source and the detector. The transmission medium is an ultra-thin fiber of glass or fused silica. The light source is either a LED (Light Emit Diode) or a laser diode, both of which emits light pulses when a electrical current is applied. The detector is a photo diode, which generates an electrical pulse when light falls on it.
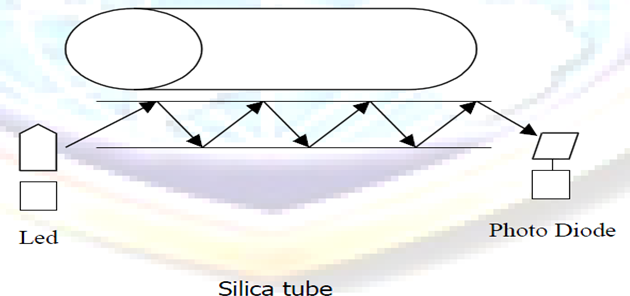
A cable may contain a single fiber, but often fibers are bundled together in the center of the cable. Optical fibre are smaller and lighter than copper wire. One optical fiber is approximately the same diameter as a human hair.
Advantages of Fiber Optic
- Noise resistance: it is immune to Electromagnetic Interference (EMI)
- Less signal attenuation: signal can run for miles without requiring regeneration
- Higher bandwidth: fiber optic cable can support dramatically higher bandwidths (and hence data rate) than all other cables. Currently, data rates and bandwidth utilization over fiber-optic cable are limited not by the medium but by the signal generation and reception technology available. A typical bandwidth for fiber optic is 100Mbps to 1Gbps.
Disadvantages of Fiber Optic
- Cost : most expensive among all the cables
- Installation / maintenance: is high
- Fragility : glass fiber is more easily broken than wire
Unguided Transmission Media
Unguided/non-physical/wireless/unbounded media have no physical link between sender and receiver.
There has been increasing need for mobile users to connect to a network. The answer for their needs is wireless. In wireless communications, space (air) is the medium for the signals.
Wireless networking has some advantages over wired networking:
- No wires needed. Running wires can be difficult in some cases; such as wiring an existing building, wiring between buildings, wiring across mountains, etc.
- Staying connected is important for mobile users. Wireless networks allow users stay connected more hours each day. Users with laptops may roam their work space without losing network connection and without logging into another machine. This increases the productivity of workers.
- Wireless networks can grow without much difficulty compared with wired networks. Making a wired network larger often involves wiring and usually costly.
- Wireless networks are not confined to an area. There is no long term commitment as in the wired networks.
Categories of unguided media
There are two categories of unguided media. These are:
- Radio transmission: These are systems for AM or FM radio. They are one form of communications and not used for computer networks.
- Microwave transmission: We can classify them into three categories; Terrestrial microwave, Satellite and Infra Transmission
Terrestrial Microwave
Microwaves do not follow the curvature of the earth therefore require line of sight transmission and reception equipment. The distance coverable by line of sight signals depends to a large extend on the height of the antenna: the taller the antenna, the longer the sight distance. Height allows the signals to travel farther without being stopped by the curvature of the earth and raises the signals above many surface obstacles, such as low hills and tall buildings that would otherwise block transmission.
Microwave signals propagate in one direction at a time, which means that two frequencies are necessary for two ways communication such as telephone communication. One frequency is reserved for transmission in one direction and other for transmission in other. Each frequency requires its own transmitter and receiver. Today, both pieces of equipment usually are combined in a single piece of equipment called transceiver, which allows a single antenna to serve both frequencies and functions.
Terrestrial microwave systems are typically used when using cabling is very costly and difficult to set.
Satellite Communication
Satellite transmission is much like line of sight microwave transmission in which one of the stations is a satellite orbiting the earth. The principle is the same as terrestrial microwave, with a satellite acting as a super-tall antenna and repeater. Although in satellite transmission signals must still travel in straight lines, the limitations imposed on distance by the curvature of the earth are reduced. In this way, satellite relays allow microwave signals to span continents and ocean with a single bounce.
Satellite microwave can provide transmission capability to and from any location on earth, no mater how remote. This advantage makes high quality communication available to undeveloped parts of the world without requiring a huge investment in ground based infrastructure. Satellite themselves are extremely expensive, of course, but leasing time or frequencies on one can be relatively cheap.
Infrared Transmission
Infrared media uses infrared light to transmit signals. LEDs transmit the signals, and photodiodes receive the signals. The remote control we use for television, VCR and CD player use infrared technology to send and receive signals.
Because infrared signals are in high frequency range, they have good throughput. Infrared signals do have a downside; the signals cannot penetrate walls or other objects, and they are diluted by strong light sources.
With any communication system, there is a high possibility that the signal that is received will differ from the signal that is transmitted as a result of various transmission impairments. For analog signals, these impairments introduce various random modifications that degrade the signal quality. For digital signals, bit errors are introduced: A binary 1 is transformed into a binary 0, and vice versa.
The most significant impairments are the following:
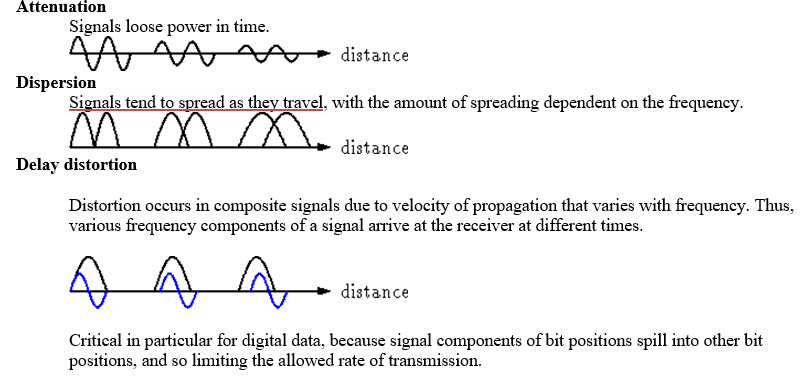
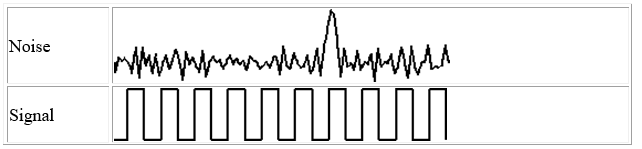
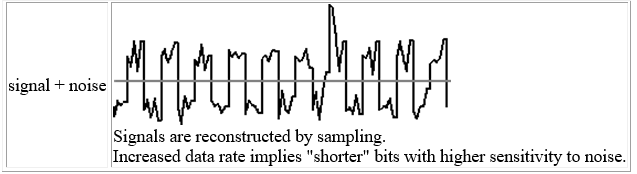
Noise
Noise refers to any unwanted signal. For any data transmission event, the received signal will consist of the transmitted signal, modified by the various distortions imposed by the transmission system, plus additional unwanted signals that are inserted somewhere between transmission and reception; the latter, undesired signals are referred to as noise-a major limiting factor in communications system performance.
TOPIC NINE: ICT ETHICS AND LEGISLATIONS
THEORY
Specific Objectives
By the end of this topic, the trainee should be able to:-
- Explain the meaning and importance of ICT ethics
- Describe unethical behavior in ICT
- Explain reasons for unethical behavior in ICT
- Explain the measures for controlling unethical behavior in ICT
- Explain the sources of ICT legislations
- Describe ICT legislations and policies
- Explain enforcement measures for ICT legislation and policies
CONTENT
- Meaning and importance of ICT ethics
- Unethical behavior in ICT
- Software piracy
- Unauthorized access
- others
- reasons for unethical behavior in ICT
- Measures for controlling unethical behavior in ICT
- Sources of ICT legislation
- ICT legislations and policies
- ICT policy
- Data Protection
- Copyright
- Information Privacy
- Others
- Enforcement measures for ICT legislation and policies
Meaning of ICT ethics
Ethics is a set of moral principles that govern the behavior of a group or individual. Therefore, ICT ethics is set of moral principles that regulate the use of ICT. Ethics
are grounded in the notion of responsibility (as free moral agents, individuals,
Organizations, and societies are responsible for the actions that they take) and
Accountability (individuals, organizations, and society should be held accountable
to others for the consequences of their actions).
The Importance of Ethics in ICT (Check)
Information is a source of power and, increasingly, the key to prosperity among those with access to it. Consequently, developments in ICT also involve social and political relationships. This makes ethical considerations on how important information is used.
Electronic systems now reach into all levels of government, into the workplace, and into private lives to such an extent that even people without access to these systems are affected in significant ways by them. New ethical and legal decisions are necessary to balance the needs and rights of everyone.
As in other new technological arenas, legal decisions lag behind technical developments. Ethics fill the gap as people negotiate how use of electronic information should proceed. The following notes define the broad ethical issues now being negotiated. Since laws deciding some aspects of these issues have been made, these notes should be read in conjunction with Legal Issues in Electronic Information Systems.
Unethical behavior in ICT
Unethical behavior in ICT is the incorrect use of ICT in a way that disturbs privacy of others or their intellectual property rights thereby creating ethical dilemmas. Unethical behavior in ICT includes:
- Software piracy
Software piracy is the unauthorized copying of software. Most retail programs are licensed for use at just one computer site or for use by only one user at any time. By buying the software, you become a licensed user rather than an owner. You are allowed to make copies of the program for backup purposes, but it is against the law to give copies to friends and colleagues. Another type of software piracy is software counterfeiting which occurs when fake copies of software are produced in such a way that they appear to be authentic.
- Unauthorized access or Hacking
Hacking or unauthorized access is breaking into computer systems, it entails approaching, trespassing within, communicating with, storing data in, retrieving data from, or otherwise intercepting and changing computer resources without consent. These break-ins may cause damage or disruption to computer systems or networks.
- Plagiarism check)
Plagiarism is the practice of taking someone else’s work or ideas and passing them off as one’s own. Plagiarism was around long before the Internet but the advent of the internet has increased cases of plagiarism and made it difficult to detect.
- Spamming
Spamming is flooding the Internet with many copies of the same message, in an attempt to force the message on people who would not otherwise choose to receive it. It is normally done through unsolicited bulk emails. Most spam is commercial advertising, often for dubious products, get-rich-quick schemes, or quasi-legal services.
Every time a “spammer” sends out email spam, the entire Internet community has to bear the cost, in particular the recipients and the ISPs at the receiving end. It wastes a lot of recipients’ time and disk space.
Spam also ties up bandwidth and resources on computers and routers all over the Internet. Every unwanted email message adds to the total cost of operating the networks of computers which form the Internet. Spam can disrupt a network by crashing mail servers and filling up hard drives. Spam also constitutes an invasion of Internet users’ online privacy.
- Phishing
Phishing is the act of sending an e-mail to a user falsely claiming to be an established legitimate enterprise in an attempt to trick the user into surrendering private information that will be used for identity theft. The e-mail directs the user to visit a Web site where they are asked to update personal information, such as passwords and credit card, social security, and bank account numbers, that the legitimate organization already has. The Web site, however, is bogus and set up only to steal the user information.
Reasons for unethical behavior in ICT
- Pressure can drive people to do things they wouldn’t normally do. For example pressure to meet unrealistic deadlines and expectations, from co-workers, bosses, or customers, can lead some people to engage in unethical activities or at least look the other way.
- Some people make unethical choices because they are ignorant of what really is the right thing to do. Often, ethical problems are complicated, and the proper choice may not be obvious.
- Some people behave unethically because of self-interest, need for personal gain, ambition or downright greed.
- Misguided loyalty is another reason for unethical conduct on the job. People sometimes lie because they think in doing so they are being loyal to the organization or to their bosses. For example, managers at automobile companies who hide or falsify information about defects that later cause accidents and kill people.
- There are those people who never learned or do not care about ethical values. Since they have no personal ethical values, they do not have any basis for understanding or applying ethical standards in their work. These people do not think about right and wrong. They only think, “What’s in it for me?” and “Can I get away with it?”
- Competition for scarce resources, power or position can also cause individuals to engage in unethical behaviors.
Measures for controlling unethical behavior in ICT
There azre a number of ways which managers can adopt to reduce unethical behavior in their organizations. These include:
- Hiring of individuals with high ethical standards;
- Establishing code of ethics and decision rules;
- Defining job goals and performance appraisal mechanism;
- Providing ethical training;
- Conducting social audits and providing support to individuals facing ethical dilemmas.
Sources of ICT legislation
Legislation is the laws governing everybody in a country while ICT legislation refers to the laws governing the ICT sector. In Kenya, the ICT sector is still emerging and there are no specific laws for the sector. However, there are several affecting the ICT sector in Kenya. These are:
- The following laws govern/affect the sector:
- Kenya Communications Act 1998
- Postal Corporation Kenya Act 1998
- Kenya Broadcasting Corporation Act
- The Telegraph Press Message Act 1983
- The Science & Technology Act
- State Corporations Act
- The Education Act
Draft legislation that is expected to be passed soon and which are likely to affect the ICT sector includes:
- Broadcasting Bill
- Freedom of Information
- Electronic Transaction bill
- Mobile Telephone Reprogramming
Other laws that are used to govern the sector include the ‘Common law’ and the ‘Statute law’ of the United Kingdom
ICT policy
A policy can be defined as a plan of action to guide decisions and actions. The term may apply to government, organizations and individuals. Policies in short can be understood as mechanisms arranged to reach explicit goals.
An ICT policy can therefore be defined as the rules and regulations set by the organization that determines the type of internal and external ICT resources employees can access, the kinds of programs they may install on their own computers as well as their authority for accessing network resources.
Benefits of policies
- i) Help save time
- ii) Help prevent managerial mistakes
iii) Improve consistency of decision making
- iv) Focus decisions towards business goals
Data Protection (Information Privacy)
Data Protection is achieved through the Data Protection Act. The Data Protection Act was developed to give protection and lay down the rules about how personal data can be used. It was created to protect individuals from misuse of this data. It governs the collection and processing of data by organizations and the individual rights to access the data if they wish.
Principles of Data Protection Act
- Data must be kept secure;
- Data stored must be relevant;
- Data stored must be kept no longer than necessary;
- Data stored must be kept accurate and up-to-date;
- Data must be obtained and processed lawfully;
- Data must be processed within the data subject rights;
- Data must be obtained and specified for lawful purposes;
- Data must not be transferred to countries without adequate data protection laws.
Copyright
Copyright is achieved through the Copyright, Design and Patents Act of 1988. This Act was introduced to protect people who have created original pieces of work like Books, Music, Films, Games and Applications, etc.
Two main purposes of the Act:
- To ensure people are rewarded for their endeavours.
- To give protection to the copyright holder if someone tries to steal their work.
The Act protects a wide range of work both written and computer based and Includes:
- Copying Software;
- Copying or Downloading music;
- Copying images or photographs from the Web;
- Copying text from web pages
The Computer Misuse Act
The Computer Misuse Act (1990) was introduced to secure computer material against unauthorised access or modification. Before this act was enacted, it was not possible to prosecute a ‘hacker’. Three categories of criminal offences were established to cover the following conduct:
- Unauthorised access to computer material (viewing data which you are not authorized to see).
- Unauthorised access with intent to commit or facilitate commission of further offences (hacking).
- Unauthorised modification of computer material.
Enforcement measures for ICT legislation and policies (Add)
TOPIC TEN: LIFE SKILLS
TOPIC ELEVEN: CONFLICT MANAGEMENT
TOPIC TWELVE: SOCIAL RESPONSIPILITY IN INFORMATION COMMUNICATION TECHNOLOGY (ICT)
TOPIC THIRTEEN: EMERGING TRENDS IN ICT AND ETHICS
THEORY
Specific Objectives
By the end of this topic, the trainee should be able to:-
- Identify emerging trends in ICT and ethics
- Explain the challenges and opportunities of emerging trends in ICT and ethics
- Cope with the challenges of emerging trends in ICT and ethics
CONTENT
- Emerging trends in ICT and ethics
- Challenges and opportunities of emerging trends in ICT ethics
- Coping with the challenges of emerging trends in ICT and ethics
WIRELESS NETWORKS
One of the exciting new developments is the deployment of wireless networks. There are
two main types of wireless networks today: Cellular and WIFI.
- Cellular networks are used primarily for voice coverage along with very limited
data capabilities. The main advantage of cellular technology is its long-range
capability. In many parts of the world, there is persistent cellular connectivity available. (for example users on some of the high-speed trains in Europe and Asia can even use their cell phones while travelling).
Advantages of Cellular Technology
- Cellular technology is very good for voice communication.
- Very wide acceptance worldwide
Disadvantages of Cellular Technology
- It has very limited (i.e., slow) data capability.
- All of the major carriers are working on next generation cellular technology that will dramatically increase the data capabilities.
- WIFI is based on existing wired computer network technology (LAN). It
provides very high speed but with a much short range of service. It is available in
limited locations (commonly called ‘hot spots’.) It does not provide voice
Communication, just Internet access. Additionally, WIFI access requires a
specific device or a special add on to other devices (laptop and PC). Today, only
a relatively small number of users have appropriate devices. However, the
expectation is that this technology will gain very rapid popularity.
Advantages of WIFI Technology
- WIFI is excellent for data communication.
Disadvantages of WIFI Technology
- It is limited in availability
- Very expensive. However it is expected that as the availability increases, the costs will drop.
Cloud Computing
Cloud Computing is a technology that uses the internet and central remote servers to maintain data and applications. Cloud computing allows consumers and businesses to use applications without installation and access their data at any computer with internet connection. Cloud computing relies on sharing of resources to achieve economies of scale similar to a utility (like the electricity grid) over a network. At the foundation of cloud computing is the broader concept of converged infrastructure and shared services
A simple example of cloud computing is Yahoo email, Gmail, or Hotmail etc. All you need is just an internet connection and you can start sending emails. The server and email management software is all on the cloud (internet) and is totally managed by the cloud service provider Yahoo, Google etc
Cloud computing is so named because the information being accessed is found in the “clouds”, and does not require a user to be in a specific place to gain access to it. Companies may find that cloud computing allows them to reduce the cost of information management, since they are not required to own their own servers and can use capacity leased from third parties.
Advantages of Cloud Computing
If used properly and to the extent necessary, working with data in the cloud can benefit all types of businesses. The following are some of the advantages of this technology:
- Cost Efficient. Cloud computing is probably the most cost efficient method to use, maintain and upgrade. Traditional desktop software costs companies a lot in terms of finance. Adding up the licensing fees for multiple users can prove to be very expensive for the establishment concerned. The cloud, on the other hand, is available at much cheaper rates and hence, can significantly lower the company’s IT expenses.
- Almost Unlimited Storage. Storing information in the cloud gives you almost unlimited storage capacity. Hence, you no more need to worry about running out of storage space or increasing your current storage space availability.
- Backup and Recovery. Since all your data is stored in the cloud, backing it up and restoring the same is relatively much easier than storing the same on a physical device. Furthermore, most cloud service providers are usually competent enough to handle recovery of information. Hence, this makes the entire process of backup and recovery much simpler than other traditional methods of data storage.
- Automatic Software Integration. In the cloud, software integration is usually something that occurs automatically. This means that you do not need to take additional efforts to customize and integrate your applications as per your preferences. Cloud computing also allows you to customize your options with great ease.
- Easy Access to Information. Once you register yourself in the cloud, you can access the information from anywhere, where there is an Internet connection. This convenient feature lets you move beyond time zone and geographic location
- Quick Deployment. Lastly and most importantly, cloud computing gives you the advantage of quick deployment. Once you opt for this method of functioning, your entire system can be fully functional in a matter of a few minutes. Of course, the amount of time taken here will depend on the exact kind of technology that you need for your business.
Disadvantages of Cloud Computing
In spite of its many benefits, as mentioned above, cloud computing also has its disadvantages. Businesses, especially smaller ones, need to be aware of these cons before going in for this technology.
- Technical Issues .Though it is true that information and data on the cloud can be accessed anytime and from anywhere at all, there are times when this system can have some serious dysfunction. You should be aware of the fact that this technology is always prone to outages and other technical issues. Even the best cloud service providers run into this kind of trouble, in spite of keeping up high standards of maintenance. Besides, you will need a very good Internet connection to be logged onto the server at all times. You will invariably be stuck in case of network and connectivity problems.
- Security in the Cloud. The other major issue while in the cloud is that of security issues. Before adopting this technology, you should know that you will be surrendering all your company’s sensitive information to a third-party cloud service provider. This could potentially put your company to great risk. Hence, you need to make absolutely sure that you choose the most reliable service provider, who will keep your information totally secure.
- Prone to Attacks. Storing information in the cloud could make your company vulnerable to external hack attacks and threats. As you are well aware, nothing on the Internet is completely secure and hence, there is always the lurking possibility of stealth of sensitive data.
PERSONAL DIGITAL ASSISTANTS (PDA)
PDAs are small devices which can be loosely thought of as very small, limited functionality PCs. They do a very good job of storing contact lists and calendars. Some can be used to access email remotely.
In order to make them fit easily in a pocket or purse; PDAs have very small
screens and either no keyboard or a very small one.
Advantages of PDAs
- Can organize daily schedules
- Can take notes
- Can record voice memos and lectures
- Can write and rehearse PowerPoint presentations
- Able to view journal articles, photos and movies
Disadvantages of PDAs
- You can’t display a complete page of text or graphics on a PDA
- Data entry, beyond short messages, is difficult or impossible.
- Screen size is small
- Battery life is limited
- Limited memory capacity.
E-learning
E-Learning is the use of technology to enable people to learn anytime and anywhere. E-learning applications and processes include Web-based learning, computer-based learning, virtual education opportunities and digital collaboration. Content is delivered via the Internet, intranet/extranet, audio or video tape, satellite TV, and CD-ROM. It can be self-paced or instructor-led and includes media in the form of text, image, animation, streaming video and audio.
Electronic commerce
Electronic commerce, commonly known as e-commerce is the process used to distribute, buy, sell or market goods and services, and the transfer of funds online, through electronic communications or networks. Electronic commerce i basically began (although debated) in 1994 when Jeff Bezos started Amazon.com out of his own garage. Well known e-commerce stores include sites like eBay, Dell, Walmart and many more.
Social networking
A social networking service is an online service, platform, or site that focuses on facilitating the building of social networks or social relations among people who, for example, share interests, activities, backgrounds, or real-life connections. A social network service consists of a representation of each user (often a profile), his/her social links, and a variety of additional services. Most social network services are web-based and provide means for users to interact over the Internet, such as e-mail and instant messaging. Social networking sites allow users to share ideas, activities, events, and interests within their individual networks.
The main types of social networking services are those that contain category places (such as former school year or classmates), means to connect with friends (usually with self-description pages), and a recommendation system linked to trust. Popular methods now combine many of these, with American-based services Facebook, Google+, and Twitter widely used worldwide.
