LEGAL, ETHICAL AND SOCIAL ISSUES IN M.I.S
Technology can be a double-edged sword. It can be the source of many benefits but it can also create new opportunities for invading your privacy, and enabling the reckless use of that information in a variety of decisions about you.
UNDERSTANDING ETHICAL AND SOCIAL ISSUES RELATED TO SYSTEMS
Ethics refers to the principles of right and wrong that individuals, acting as free moral agents, use to make choices to guide their behaviors. When using information systems, it is essential to ask, “What is the ethical and socially responsible course of actin?” Ethical, social, and political issues are closely linked. The ethical dilemma you may face as a manager of information systems typically is reflected in social and political debate.
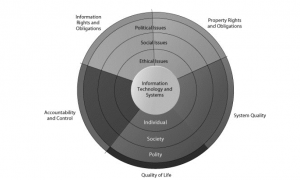
Figure: The Relationship between Ethical, Social, and Political Issues in an Information Society
FIVE MORAL DIMENSIONS OF THE INFORMATION AGE
The major ethical, social, and political issues raised by information systems include the following moral dimensions: 1. Information rights and obligations. What information rights do individuals and organizations possess with respect to themselves? What can they protect?
Internet Challenges to Privacy
Internet technology has posed new challenges for the protection of individual privacy. Information sent over this vast network of networks may pass through many different computer systems before it reaches its final destination. Each of these systems is capable of monitoring, capturing, and storing communications that pass through it.
2. Property rights and obligations. How will traditional intellectual property rights be protected in a digital society in which tracing and accounting for ownership are difficult and ignoring such property rights is so easy? Intellectual property is considered to be intangible property created by individuals or corporations. Information technology has made it difficult to protect intellectual property because computerized information can be so easily copied or distributed on networks. Intellectual property is subject to a variety of protections under three different legal traditions: trade secrets, copyright, and patent law.
i. Trade Secrets Any intellectual work product – a formula, device, pattern, or compilation of data-used for a business purpose can be classified as a trade secret, provided it is not based on information in the public domain.
ii. Copyright Copyright is a statutory grant that protects creators of intellectual property from having their work copied by others for any purpose during the life of the author plus an additional 70 years after the author’s death. iii. Patents A patent grants the owner an exclusive monopoly on the ideas behind an invention for 20 years. The congressional intent behind patent law was to ensure that inventors of new machines, devices, or methods receive the full financial and other rewards of their labor and yet make widespread use of the invention possible by providing
detailed diagrams for those wishing to use the idea under license from the patent’s owner. 3. Accountability and control. Who can and will be held accountable and liable for the harm done to individual and collective information and property rights? System Quality: Data Quality and System Errors Three principle sources of poor system performance are: – (1) Software bugs and errors (2) Hardware or facility failures caused by natural or other causes and (3) Poor input data quality. The software industry has not yet arrived at testing standards for producing software of acceptable but not perfect performance. System quality – What standards of data and system quality should we demand to protect individual rights and the safety of society? 4. Quality of Life. What values should be preserved in an information- and knowledge-based society? i. Balancing Power: Center versus Periphery
Lower level employees many be empowered to make minor decisions but the key policy decisions may be as centralized as in the past.
ii. Rapidity of Change: Reduced Response Time to Competition Information systems have helped to create much more efficient national and international market. The now-more-efficient global marketplace has reduced the normal social buffers that permitted businesses many years to adjust to competition. We stand the risk of developing a “just-in-time society” with “just-in-time jobs” and “just-in-time” workplaces, families, and vacations.
iii. Maintaining Boundaries: Family, Work, and Leisure The danger to ubiquitous computing, telecommuting, nomad computing, and the “do anything anywhere” computing environment is that it is actually coming true. The traditional boundaries that separate work from family and just plain leisure have been weakened. The work umbrella now extends far beyond the eight-hour day.
iv. Dependence and Vulnerability Today our businesses, governments, schools, and private associations, such as churches are incredibly dependent on information systems and are, therefore, highly vulnerable if these systems fail. The absence of standards and the criticality of some system
applications will probably call forth demands for national standards and perhaps regulatory oversight.
v. Computer Crime and Abuse New technologies, including computers, create new opportunities for committing crimes by creating new valuable items to steal, new way to steal them, and new ways to harm others. Computer crime is the commission illegal acts through the use of a computer or against a computer system. Simply accessing a computer system without authorization or with intent to do harm, even by accident, is now a federal crime.
Computer abuse is the commission of acts involving a computer that may not illegal but that are considered unethical. The popularity of the Internet and e-mail has turned one form of computer abuse – spamming – into a serious problem for both individuals and businesses. Spam is junk e-mail sent by an organization or individual to a mass audience of Internet users who have expressed no interest in the product or service being marketed.
vi. Employment: Trickle-Down Technology and Reengineering Job Loss Reengineering work is typically hailed in the information systems community as a major benefit of new information technology. It is much less frequently noted that redesigning business processes could potentially cause millions of mid-level managers and clerical workers to lose their jobs. One economist has raised the possibility that we will create a society run by a small “high tech elite of corporate professionals…in a nation of permanently unemployed” (Rifkin, 1993). Careful planning and sensitivity to employee needs can help companies redesign work to minimize job losses.
vii. Equity and Access: Increasing Racial and Social Class Cleavages Several studies have found that certain ethnic and income groups in the United States are less likely to have computers or online Internet access even though computer ownership and Internet access have soared in the past five years. A similar digital divide exists in U.S. schools, with schools in high-poverty areas less likely to have computers, high-quality educational technology programs, or internet access availability for their students. Public interest groups want to narrow this digital divide by making digital information services – including the Internet – available to virtually everyone, just as basic telephone service is now.
viii. Health Risks: RSI, CVS, and Technostress The most common occupational disease today is repetitive stress injury (RSI). RSI occurs when muscle groups are forced through repetitive actions often with high-impact loads (such as tennis) or tens of thousands of repetitions under low-impact loads (such as working at a computer keyboard). The single largest source of RSI is computer keyboards. The most common kind of computer-related RSI is carpal tunnel syndrome (CTS), in which pressure on the median nerve through the wrist’s bony structure, called a carpal tunnel, produces pain. Millions of workers have been diagnosed with carpal tunnel syndrome. Computer vision syndrome (CVS) refers to any eyestrain condition related to display screen use in desktop computers, laptops, e-readers, smart-phones, and hand-held video games. Its symptoms, which are usually temporary, include headaches, blurred vision, and dry and irritated eyes. The newest computer-related malady is technostress, which is stress induced by computer use. Its symptoms include aggravation, hostility toward humans, impatience, and fatigue. Technostress is thought to be related to high levels of job turnover in the computer industry, high levels of early retirement from computer-intense occupations, and elevated levels of drug and alcohol abuse.
(adsbygoogle = window.adsbygoogle || []).push({});

2 thoughts on “LEGAL, ETHICAL AND SOCIAL ISSUES IN M.I.S”
Comments are closed.