CHAPTER 10
INFORMATION SYSTEM ETHICS
Ethics refers to the principles of rights and wrong that can be used by individuals acting as free moral agents to make choices to guide their behavior. Information systems raise new ethical questions for both individuals and society because they create opportunities for intense social change and they threaten existing distribution of power, money, rights and obligations. These issues have 5 dimensions.
1. Information rights and obligations – what rights do individuals and organization posses with respect to information about themselves?
What can they protect?
What obligation do individuals and organization have a conceiving this information?
2. Property rights – How will traditional property rights be protected in a digital
society in which trading and accounting for ownership is difficult and ignoring such
property rights is it so easy.
3. Accountability and control – who will be held responsible, accountable and reliable for the harm done to individuals and their property rights.
4. System quality – what standards of data and system quality should we demand to protect the individual rights and the safety of the society.
5. Quality of life – what values should be preserved in information and knowledge based society?
What institution should we protect from violation?
What actual values and practices are supported by the new technology?
Key technology trends that raise ethical issues
1. The doubling of computer power every 18 months has made it possible for most organizations to utilize information systems for the core production processes.
Leading to an increase in dependency on systems, vulnerability to system errors and poor data quality.
There are no social rules and laws adjusted to this dependency and standards for ensuring the accuracy and reliability of information systems.
2. Advance in data storage techniques and rapidly declining storage costs has been responsible for the multiplication of databases e.g. employees, customer and potential customer maintained by private and public organization.
These advances make routine violation of individual’s privacy both cheap and effective.
3. Advances in determining techniques for large databases, organization collect and combine information about a customer from credit card purchase, telephone calls, banking records and police records. If properly mine this can reveal credit information, living habits, tastes, association and political interests.
4. Advances in networking – this greatly reduces the cost of moving and accessing large quantities of data and open the possibility of mining large pools of data remotely using small desktop machines permitting and invasion of privacy.
The global digital superhighway communication network posse’s social and ethical concerns such as:-
i) Who will account for the flow of information over the networks?
ii) Will you be able to trace information collected about you?
iii) What will these networks do to the traditional relationships, families, work
and leisure?
Ethical Principles:-
1) The golden rule – do unto other as you would have them do unto you.
2) Kant’s categorical imperative – if an action is not right for everyone to take then it’s not right for anyone to take.
3) Descarte’s rule of change – if an action can’t be taken repeatedly, then it’s not right
to be taken at any time.
4) Utilization principle – take the action that achieves the higher or greater value.
5) Risks aversion principle – take the action that products the lease lewd on the least
potential cost.
6) No free lunch – virtually all tangible and intangible objects are owned by someone unless there is a specific declaration otherwise.
Professional Codes of Ethics (CONDUCT)
These are special rights and obligations take on by professional due to their special claims of knowledge and wisdom. It also entails respect e.g. institute for the management of information system (IMIS), Association of Business Executive (ABE),
ICPAK, Law Society of Kenya (LSK) and Association of Computer Machinery Codes
(ACMC).
These promise the professionals to regulate themselves in the general interest of the society e.g. avoiding harm to other, honoring property rights including intellectual property and respecting privacy.
They also determine entrance qualifications and competence consider an e.g. British
Computer Society (BSC) which was formed in 1957 and become a full member of England Engineering council in 1990. It’s a professional body of computer practitioners in the United Kingdom and has more than 34 members.
The society is concerned with development of computing and its effective applications. It has assumed responsibilities for education and training for public awareness and for standards of quality and professionalism.
Its role is to set the professional standards of competence conduct and ethical practice in
the U.K. It’s an authoritative voice to the society government and industry or all aspects
of IS.
It influences legislation on data registration, safety, copyright and product liability. The society has 3 degrees of members i.e associate, members and fellow.
Members at the 3 levels are accepted according to their qualification.
Some Real World Ethical Dilemma
1. Continental incorporated developed a human resource Db that was able to ‘red flag’ an employee who was almost retirement age, where the red flag went up the management for the employee even in delay.
2. AT & T Telephone Company uses technology to monitor employees’ responses to customer. It hopes to eliminate 3000 to 6000 employees by identifying speech that is unpractical and summary.
3. E-mail-privacy at Epson – in 1990 an employee of Epson sued the company for $75,000,000 for unlawful termination. She was fired because of questioning the company’s policy of monitoring and printing of employees.
4. Mails messages – many firms claim the right to open mail because they own the facility. They are intended for the business only and create this facility for a business purpose.
Other ethical issues concerning technology include;
1. Employment – is have been known to lead to loss of jobs and hence a decline in quality of life.
2. Equity Access and increasing ratio and social classes – Does everyone have an
equal opportunity to participate in the digital age? Will the gaps increase or
reduce.
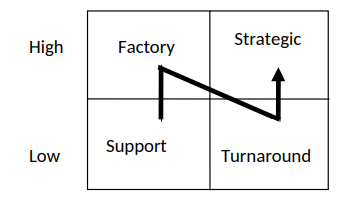
Any of the organization in existence has to fall in any of the above four quadrants.
1. Strategic quadrant – information systems planning is critical to the current and future performance of the firm. I.S planning must be closely linked to corporate planning.
2. Turn-round is – information systems planning is very importance to the future performance of the firm, without I.S planning, performance will suffer significantly in the long-run I.S planning must be closely linked to corporate planning.
3. Factory – I.S planning is needed for the information systems activity to be coordinated and to run smoothly. It’s important to the current company performance, but it’s not expressed to be a critical factor in the future.
4. Support – I.S planning is still needed for the I.S activity to be coordinated and to run smoothly. It’s not critical to the current company performance and is very unlikely to be of strategic importance in the future.
Example:
1. Support – this could be an organization that has developed a system to automate some of the clerical procedures and it has no intention of investing in I.T in the near future.
2. Factory – this could be an organization that has developed a network which is quiteuseful in day-to-day running of company activities and has no intention further in
I.T.
3. Turnaround – are organizations that one currently not using I.T. for nay strategic use but there future survival will involve I.T. a lot, such as a university that is contemplating of having a virtual university i.e. African Virtual University (A.V.U).
Strategic Factory
Support Turnaround High Low
4. Strategic – e.g a Bank that has invested in ATMs and any future survival in competing effectively is alighted to I.T. e.g. loan portfolio management. Maslow qualified human wants into a hierarchy of needs. Each lower want or need must be stratified before a worker will seek rewards at the next higher level. Consider the levels starting with the most basic:-
1. Physiological needs – food, clothing and shelter. For the worker this means money.
Many workers are willing to work at relatively tedious jobs or at higher production rates given sufficient monetary incentives.
2. Safety or security needs – for the worker this means overall job security. Also at the work site, improving the safety environment will improve the working climate.
3. Social needs – worker seek “belonging” interms of work, this could mean having friendly co-workers, comfortable interaction with management and being able to participate in company’s committees.
4. Self –esteem – workers strive for competence, desire some respect and seek to satisfy their egos. This could be provided by making the work more challenging, adding more responsibility and providing greater variety.
5. Self-fulfillment – when all other needs are fulfilled people become satisfied with life.
Computer crime
Information system control, threats to security, privacy and confidentiality in MIS operations
Electronic funds transfer systems, ICU (Intensive Care Unit) and air traffic control systems depend on computers to function reliably and it’s estimated that they can’t survive a total failure of their information systems processing capacity for longer than a
day or two. The relationship between threats to information systems control can be illustrated as follows:-

Classes of threats
1. Human error – involves wrong input data, errors in program development or maintenance and operator errors e.g. mislabeling the tapes.
2. Natural and political disasters – includes earthquakes, typhoons, tornados and hurricanes.
3. Failure to hardware and software – e.g. network and power failures and software maintenance.
4. Computer abuse and crime – using a computer to steal, sabotaging the system and authorized access to a modification of data (hacking). Computer crime is any illegal act in which a computer is used as a primary e.g. impersonification i.e.
giving access to a system by identifying oneself as one person and therefore enjoys privileges of the legitimate user.
TROJAN HORSE method i.e. conspiring within an authorized programme are routine of actions causing unauthorized actions.
LOGIC BOMB i.e. programme who placed a logic bomb in his companies personnel system such that should his name be upset from the personal file the entire file is erased.
Computer viruses introduced deliberately.
Data diddling i.e. changing of data during or before input often to change the contents of the database.
Salami technique – this is diverting small amounts from large number of accounts maintained by a system.
Super-zapping – using a system program that can by pass regular system controls to perform unauthorized act e.g. the IBM super-zap utility.
Super-zaps are provided to handle emergencies in systems such as restoring systems operations after a multifunction that can’t be handled with a regular recovery method.
Scavenging – its unauthorized access to information by searching via the residue after the job has been run on the computer e.g. searching the waste paper basket for printouts etc.
Wire tapping or carves-dropping
Spoofing – collecting of confidential information from unsuspecting visitors to the website they visit.
Having defined controls as a set of policies, procedures and technological measures that are put together an error or an attack of commuter systems from taking place detect the violation and correct the exceptional situation. These controls can be categorized into general or application controls.
General controls:
1. Administrative – include separation of duties, constant supervision of staff, thorough screening of new employees, published procedures and standards. These can also include disaster recovery planning or contingency planning.
2. System development and maintenance control – systems should be secure and auditable. Documentation should be maintained and should specify changes made to the system.
3. Operational controls – involve controlling access to system, maintenance of computer equipment and storage and the day to day running of the company activities.
4. Physical protection of data centres – e.g. installation of air conditioning equipments, fire extinguishers and UPS (uninterruptable power supply).
5. Controlling access to computer system and information e.g. identification, authentification and encryption. This may use the user’s knowledge e.g. the name, account number or password i.e. a smart card with a microprocessor or a biometric control. This is the using of bodily features such as fingerprints, hand geometry (chiromancy) , retrieval scanning and the signature.
6. Control as a last result e.g. adequate insurance for the residual risk or a disaster recovery plan.
Application controls
Implemented specifically for a particular information system e.g. a payroll system, account payable or order processing system. They include;
1. Input control – this is to ensure accuracy, completeness and validation of input.
2. Processing control – e.g. cross-checking two computation which can also include reasonable checks and rounding off.
3. Database controls – these include backups, recovery, file handling and authorization.
4. Communication controls – including encrypting and the use of digital signatures which should also be encrypted.
5. Output controls .e.g. scheduling, handling and distribution.
Auditing of Information Systems
Auditing is the process of verifying organizations accounting records and financial statements. However, this is not possible today without a thorough audit of the information systems which are the primary tools for managing these records. Information systems are audited by external auditors who test the accuracy and the truth of the corporate financial statements and by internal auditors who work for the organization itself.
Internal auditors also perform operational auditors to evaluate the effectiveness and efficiency of MIS operations.
The principle behind the auditability of information systems is that every transactions must reliably be traceable to the aggregate figures that it affects and each aggregate figure must be traceable back to the transactions which gives rise to it i.e. An audit trail must exist making it possible to trace the origin and verify the processing. Transactions logs provides basic audit trail.
Conducting MIS Audit MIS auditors generally evaluate the controls on the assumption that if a system has adequate controls that are consistently applied the information produced by these systems is also reliable. Audit can both be scheduled or unscheduled. The process is as follows;-
1. Study the I.S. and its documentation, inputs and outputs then interview the key users and the M.I.S personnel. Study both the general and the application controls.
2. Select a sample of transactions processed by the system and trace their processing from the original document onto the totals they affect. Replicate the processing done by the system and compare it with the result. This is called compliance testing.
3. Validate totals contained in financial records. This is known as substantive testing.
The extent of this depends on the compliance results. If controls were operative their only a limited substantive testing would be required.
4. Conclude the audit by reporting the findings to the corporate management with a detailed statement of all the controls deficiencies discovered. The use of computer
Aided Auditing Techniques (CAAT) can be applied here.
Why is it necessary to conduct an I.S Audit?
1. Give an assurance of the system reliability e.g. whether the computations are accurate and if there is any likelihood of failure.
2. To search for efficient utilization of computer systems. This confirms that the invested funds produce adequate results i.e. no wastage of resources.
3. Prevention of computer crime. This detects destructive activities such as fraud and computer viruses.
4. Protection of privacy – administrative bodies collect process and store information on individual using computer. Auditing identifies points at which private information may be leaking.
Types of IS audit
1. System development audits: Audit staff advices members of pvy development team to ensure that controls are embedded in the original design.
2. Operational audits – they are periodically conducted on an I.S to ensure that proper system controls exists and that they are being followed. They involve checking input data, processing and output.
3. Application audits – meant to validate the integrity of an I.S. It involves identifying all the controls that govern individuals I.S and access their effectiveness. The auditor needs a thorough understanding of the operations, physical facilities, telecommunication control systems, data security objectives, personnel, organizational structure and manual procedures and individual applications.
Disaster recovery planning /contingency planning
A disaster recovery plan specifies how a company will maintain. The information system necessary in the event of a disaster.
A fire or an explosion in the data centre can bring operations to a standstill. In addition a disaster plan may be required by a regulatory agency or for the purposes of obtaining an
insurance cover;-
Importance of contingency planning
1. It enables a company to take a closer look and identify any threats that may hamper its operations.
2. It enables an enterprise to be adequately prepared in the eventuality of realization
of the risks.
3. It enables the critical operations to continue in case of a disaster.
4. It eliminates the confusion, uncertainty and panic that results whenever a disaster happens by clearly stating the actions to be undertaken in the event of such a disaster.
5. It facilitates the faster recovery from the disaster thereby reducing the impact.
Steps in drawing a contingency plan
1. Resolve the basic planning issues .e.g. the scope of the plan.
2. Gather important information e.g. the cost of the subject and the case of replacement.
3. Conduct a situation assessment e.g. identity open risks and potential disaster.
4. Identity the planning constraints and limitations.
5. Identify alternative sources of active and select the optimal cause
6. Compile the plan.
7. Conduct a drill for the plan.
A disaster recovery plan has 4 major elements:-
1. An emergency plan – it specifies in what situations a disaster is to be declared and
what actions are to be taken by the various employees.
2. A back-up plan – this is a principle component which specified how information processing would be carried out during an emergency. It details how backed up computer disks or tapes are to be maintained and specifies the facility where they can be run on a very short time notice. These arrangements include;-
(i) Reciprocal arrangement – compares with similar hardware configurations agree with one another to permit short term sharing of the problem by transferring the affected system to the other company before the situation is rectified. Should a disaster occur both companies are forced to reduce their levels of data processing to support only the critical operations.
Although the method is inexpensive critical operations of the two organizations may be too much for a single one to handle.
It’s also possible for a disaster to strive both companies together.
(ii) Cold site arrangements – This is a facility that can house a mainframe computer system including environmental control, electrical services and telecommunication services.
A company may contract with a disaster recovery company to provide a cold site in cases of disaster or may rent, lease, or purchase suitable space.
(iii) Hot site arrangement – this site contains a complete date centre including a working mainframe system compatible with the one that is backing up. The strategy is expensive but minimizes the down time e.g. a computer bureau.
However the company must be aware that a similar disaster can affect several companies at the same time.
(iv) Back up facilities – A parallel facility where one company has more than one data centre. This is usually an arrangement of real-time systems. The parallel facility has duplicated software and hardware and the database is updated as an ongoing process. This arrangement is the most expensive but would be the best approach.
3. Test plan – This includes drills and practices of what would happen in cases of emergency. It tests the reliability of the back-up plans.
4. Recovery plan – This includes arrangement on purchasing hardware and software to restore the original company. This involves insurance arrangements, loans etc.
