TUESDAY: 6 December 2022. Morning Paper. Time Allowed: 2 hours.
This paper is made up of fifty (50) Multiple Choice Questions. Answer ALL the questions by indicating the letter (A, B, C or D) that represents the correct answer. Do NOT write anything on this paper.
1. A person who writes computer software for running the hardware of a computer is called a___________________.
A. Systems analyst
B. Programmer
C. Systems designer
D. Data processor (2 marks)
2. The purpose of computer software is to turn data into_____________________.
A. Information
B. Program
C. Knowledge
D. Object (2 marks)
3. A set of parallel wires or electronic pathway used to transmit data, address and control signals in between the CPU and other components of the motherboard are known as___________________.
A. Bus
B. Register
C. Processor
D. Port (2 marks)
4. Identify an advantage of information communication technology (ICT) in the education sector.
A. ICT use in the classroom can be a distraction
B. ICT can detract students from social interactions
C. ICT use motivates learning
D. ICT can foster cheating (2 marks)
5. The type of an operating system which allows a single CPU to execute what appears to be more than one program at the same time is called__________________.
A. Multiprocessing
B. Multiprogramming
C. Multiuser
D. Parallel (2 marks)
6. Which of the following is NOT part of a Computer processor?
A. Register
B. Cache
C. Bus
D. RAM (2 marks)
7. What is the name given to a computer network for interconnecting electronic devices within an individual person’s workspace?
A. Personal area network (PAN)
B. Metropolitan area network (MAN)
C. Wide area network (WAN)
D. Virtual private network (VPN) (2 marks)
8. The following are basic file operations by an operating system EXCEPT____________________.
A. Create
B. Read
C. Delete
D. Manage (2 marks)
9. Which of the following is NOT a feature of third generation of computers?
A. Technology used was of integrated circuits
B. Smaller, cheaper, more efficient and faster than second generation computers
C. Single-chip processor and the single-board computer emerged
D. Used high-level programming languages (2 marks)
10. Which of the following devices converts analogue signals to digital signals and vice versa?
A. Hub
B. Modem
C. Router
D. Switch (2 marks)
11. Which of the following refers to a security measure system that acts as a trap for hackers and can be used to study hacking attempts on a system?
A. Honeypots
B. Encryption
C. Backups
D. Controls (2 marks)
12. Which of the following terms refer to a computer animation technique used to convert images from one form to another?
A. Modeling
B. Framing
C. Morphing
D. Scarping (2 marks)
13. Identify two advantages of using new technology in businesses.
I. Easier, faster and more effective communication
II. Increased dependency on technology
III. Require regular updates
IV. Ability to develop new, innovative approaches
A. I and II
B. II and III
C. I and IV
D. II and IV (2 marks)
14. A set of step-by-step instructions, used to solve a problem or perform a computation is known as _____________.
A. Algorithm
B. Flowchart
C. Artefact
D. Accumulator (2 marks)
15. Which one of the following is NOT an example of an antivirus software?
A. Kaspersky
B. McAfee
C. Acrobat
D. Avira (2 marks)
16. The main part of the computer that contains all the essential hardware components is known as _______________.
A. System unit
B. Monitor
C. Processor
D. Power supply (2 marks)
17. A__________________ consists of two or more computers connected together.
A. Network
B. Server
C. Client
D. Cable (2 marks)
18. Which of the following devices can be used to input sound into a device?
A. Speakers
B. Sound card
C. Microphone
D. Earphones (2 marks)
19. The Internet is an example of a _____________.
A. Metropolitan Area Network
B. Campus Area Network
C. Wide Area Network
D. Local Area Network (2 marks)
20. Which of the following attacks involve a hacker intercepting and relaying messages between two parties who believe they are communicating with each other?
A. Advanced persistent threats
B. Man-in-the-middle attack
C. Drive-by attacks
D. AI powered attacks (2 marks)
21. Which of the following statements is CORRECT?
A. A translator translates object code to source code
B. Interpreter translates entire program before execution
C. Interpreter saves the object program
D. Interpreter is effective in statement by statement error correction (2 marks)
22. Which of the following is NOT an advantage of command line interface?
A. Command line interface can handle repetitive tasks easily
B. Command line interface requires less memory than other interfaces
C. Command line interface does not require windows and a low-resolution monitor can be used
D. Command line interface is very user friendly (2 marks)
23. Which of the following statements is correct as used in ICT?
A. Machine language use mnemonics
B. Machine language use abbreviations
C. Machine language use binary notation
D. Assembly language use binary notation (2 marks)
24. What is the function of uninterruptible power supply (UPS)?
A. It is a device that stores chemical energy and converts it to electrical energy
B. It provides enough electricity to a computer during a power outage so that the user can save files before shutting down the computer
C. It is a device which converts mains AC to low-voltage regulated DC power for the internal components of a computer
D. It means electric energy or capacity supplied by an electric utility to replace electric energy ordinarily generated by a qualifying facility’s own electric generation equipment during an unscheduled outage of the qualifying facility (2 marks)
25. Which of the following software acquisition statements is FALSE?
A. Off-the-shelf software is cheap
B. Off-the-shelf software is less error prone
C. Off-the-shelf software has high quality documentation
D. Off-the-shelf software rarely gives an organisation competitive advantage (2 marks)
26. Which of the following is the major limitation of bus topology?
A. Uses a lot of cabling in comparison to other topologies
B. Failure of the central cable will bring the whole network down
C. Failure of the central computer will cause the network to break down
D. Easy to detect faults and to add new sites to the network (2 marks)
27. Which of the following artificial intelligence technologies, incorporates the use of voice recognition, voice synthesis and language comprehension systems?
A. Virtual reality systems
B. Natural language processing
C. Computer aided detection
D. Magnetic resonance imaging (2 marks)
28. Which of the following statements BEST explains “wireless fidelity” (Wi-Fi)?
A. A set of standards for facilitating wireless networks in a local area, enabling devices to connect to the Internet when in range of an access point.
B. A website or similar online resource which allows anyone to set up a resource in which content can be created collectively
C. A worldwide Interoperability for Microwave Access, a telecommunication technology aimed at providing wireless data over long distances.
D. It is a computer network connecting millions of computers all over the world and provides communications to governments, businesses, universities, schools and homes. (2 marks)
29. Which of the following features is NOT part of a database?
A. Tables
B. Records
C. Fields
D. Worksheets (2 marks)
30. Identify the statement which BEST defines throughput as used in computing?
A. The volume of work or information flowing through a system.
B. The execution of more than one program, apparently at the same time, on a computer.
C. It is a measure of the number of pixels or small dots displayed on a computer display screen, printer or scanner.
D. The process and outcome of successfully adapting to difficult or challenging life experiences especially, through mental, emotional, and behavioral flexibility and adjustment to external and internal demands. (2 marks)
31. Select the BEST statement that defines a computer chipset
A. A device for storing and processing data, typically in binary form, according to instructions given to it in a variable program.
B. A technique through which multiple operating systems can be kept within the boot sequence on the same computer.
C. A collection of integrated circuits which are designed to function together as a unit, especially to perform a particular task within a computer system.
D. A printed circuit board containing the principal components of a computer or other device, with connectors for other circuit boards to be slotted into. (2 marks)
32. State the function of name box feature found in a spreadsheet window.
A. To display the active cell address or the name of the selected cell, range, or object.
B. To enter information or formulas into a cell.
C. To display various messages as well as the status of the Num Lock, Caps Lock, and Scroll Lock keys on your keyboard.
D. To display the name of the program and the name of the current workbook. (2 marks)
33. Which one of the following is NOT a function of a computer network?
A. Users can easily share or exchange information
B. The computers in a network can share resources such as printers and scanners
C. Enhances user’s security
D. Data backup can be achieved easily (2 marks)
34. What is the name of the network topology shown below?
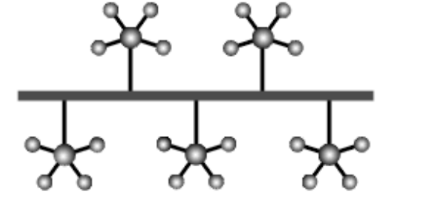
A. Star
B. Bus
C. Ring
D. Tree (2 marks)
35. Which of the following network devices can connect similar types of local area networks, while keeping local data inside its own network?
A. Bridges
B. Repeaters
C. Routers
D. Switches (2 marks)
36. Which of the following is NOT a reason for parallel lines not being used for long distance data transmission?
A. Cost factor
B. Signal attenuation
C. Number of transmission channels
D. Low speed (2 marks)
37. All of the following are techniques B2C e-commerce companies use to attract customers, with the exception of?
A. Registering with search engines
B. Virtual marketing
C. Viral marketing
D. Online ads (2 marks)
38. Which of the following statements BEST describes the function of magnetic ink character recognition (MICR) method of capturing data?
A. Converts the physical action to be measured into an electrical equivalent and processes it so that the electrical signals can be easily sent and further processed.
B. Verifies the legitimacy or originality of paper documents, especially bank cheques.
C. Converts an image of text into a machine-readable text format.
D. Scans and captures the optical marks on such documents as the multiple choice scoring sheets. (2 marks)
39. The following are examples of system software EXCEPT?
A. Operating system
B. Word processor
C. Utility
D. Device driver (2 marks)
40. Which of the following is NOT a back up storage device?
A. Hard disk
B. DVD
C. Cache
D. CD (2 marks)
41. FORTRAN, BASIC, COBOL are examples of?
A. High level programming languages
B. Low level programming languages
C. Assembly languages
D. Application software (2 marks)
42. Which of the following is measured using “dots per inch”?
A. Screen size
B. Data speeds for modems
C. Resolution of an image
D. Processing speed (2 marks)
43. Which one of the following statements, BEST describes the function of a slide master view?
A. It allows you edit and create your own layouts.
B. It shows the layout of your presentation as it is printed out on paper.
C. It allows to change the layout for every single notes section in your project.
D. It allows a colourful presentation to be shown. (2marks)
44. Which ONE of the following is NOT an example of an operating system?
A. MacOS
B. Android
C. Oracle
D. Linux (2 marks)
45. Printers can be impact or non-impact. Which one of the following is a non-impact printer?
A. Dot Matrix
B. Daisy Wheel
C. Chain printer
D. Inkjet printer (2 marks)
46. Select from the list below one disadvantage of a client-server network?
A. When server is not on, clients do not power up.
B. Clients cannot connect wirelessly to the server
C. Dependent on server if server goes down clients stop working
D. Clients are more expensive than the server (2 marks)
47. Which ONE of the following is neither an input nor output device?
A. Flash disk
B. Mouse
C. LaserJet
D. Sensor (2 marks)
48. Which of the following is NOT an ethical issue in computing?
A. Privacy
B. Security
C. Tomography
D. Cyberslacking (2 marks)
49. Which of the following refers to a grid in spreadsheet software consisting of cells, rows and columns?
A. Worksheet
B. Workbook
C. Gridlines
D. Workflow (2 marks)
50. The section at the bottom of a page reserved for displaying information that is common to the whole document is referred to as?
A. Footnote
B. Task bar
C. Footer
D. Endnote (2 marks)
