November 2021. Time Allowed: Two Hours
This paper has three sections. Section One has forty (40) multiple choice questions. Section Two has twenty (20) short response questions. Section Three has one (1) essay question. All questions are compulsory.
SECTION ONE [40 MARKS] [40 MINUTES]
1. Name the process of determining what the authenticated entity is allowed to access and what operations they are allowed to perform. (1 mark)
2. Identify the science of measuring physiological characteristics that include hand prints, fingerprints, voice, or the entire face. (1 mark)
3. Name a Microsoft Word feature used that allows one to send copies of the same letter to multiple recipients. (1 mark)
4. A device that uses the best possible path to forward data packets from one network to another is. (1 mark)
5. Data and instructions inside the computer are represented using two states of electricity, that is, on and off. This is referred to as: (1 mark)
6. Name the software that uses rows and columns to manipulate numerical data. (1 mark)
7. Which generation of computers supports artificial intelligence? (1 mark)
8. State true or false: Absolute references are cell references that change when a formula is copied from one cell to another. (1 mark)
9. State true or false: System software includes programs designed to help end users solve specific problems or perform specific tasks using the computer. (1 mark)
10. State true or false: Linux, Windows and Android are examples of application software. (1 mark)
11. State true or false: Cut and paste is used to move the original content from one document to a new location without creating a duplicate. (1 mark)
12. State true or false: A standard user account gives full control access and permissions including installing applications and changing security settings. (1 mark)
13. State true or false: A compiler executes the source program line by line. (1 mark)
14. State true or false: A router broadcasts data to all connected devices. (1 mark)
15. State true or false: In a peer to-peer network, each workstation can act both as a client and server share all or part of its resources. (1 mark)
16. State true or false: Device drivers are used to convert fragmented files into contiguous files to enable faster loading of files. (1 marks
17. In a computer network, a switch can be used to: (1 mark)
(a) Deliver data packets to the intended destination port.
(b) Ensure data packets use the best possible route to get to the destination.
(c) Translate data from one kind of protocol to another.
(d) Link two or more network segments together.
18. You have been advised to purchase a Category 6 cable to connect your laptop to a router. This cable is an example of: (1 mark)
(a) Fibre optic cables
(b) Shielded twisted pair cables
(c) Unshielded twisted pair cables
(d) Coaxial cables.
19. The gap between those who have and those who do NOT have the ability to use technology is called. (1 mark) (a) Grid computing
(b) Internet of things
(c) Radio Frequency Identification
(d) Digital divide
20. The Slide Master view in power point allows a user to: (1 mark)
(a) Encrypt a PowerPoint document
(b) Make uniform changes to all the slides in the presentation
(c) Check for compatibility issues
(d) Insert a SmartArt graphic in a document.
21. One limitation of Server based networks is: (1 mark)
(a) Scalability
(b) Increased costs
(c) Centralised administration
(d) Multiple users may share files on the server.
22. The fastest computers used by large organisations to execute computationally demanding tasks involving very large data sets are. (1 mark)
(a) Mainframe computers
(b) Minicomputers
(c) Supercomputers
(d) Microcomputers.
23. Mary wants to transfer data from a laptop to a tablet computer using unguided media. Select the best option to use for this purpose from the following: (1 mark)
(a) Bluetooth
(b) Microwave transmission
(c) Fiber optic cables
(d) Coaxial cables.
24. Instructions needed when starting the computer are stored in the: (1 mark)
(a) Random Access Memory
(b) Read Only Memory (c) Processor
(d) Joystick.
25. Viruses, trojans and worms are examples of: (1 mark)
(a) Firewalls
(b) Malware
(c) Social engineering
(d) Natural hazards.
26. Laptops, desktops and thin clients are examples of: (1 mark)
(a) Mainframe computers
(b) Supercomputers
(c) Minicomputers
(d) Microcomputers.
27. The following are functions of an operating system except: (1 mark)
(a) Data backup
(b) File management
(c) Loading application software
(d) Provides security.
28. Which of the following is an example of an output device? (1 mark)
(a) Mouse
(b) Speakers
(c) Processor
(d) Flash disk.
29. Utility software includes: (1 mark)
(a) Random access memory
(b) Central processing unit
(c) Honeypots
(d) Antivirus.
30. One characteristic of third generation computers is the use of: (1 mark)
(a) Transistors
(b) Integrated circuits
(c) Vacuum tubes
(d) Parallel processing.
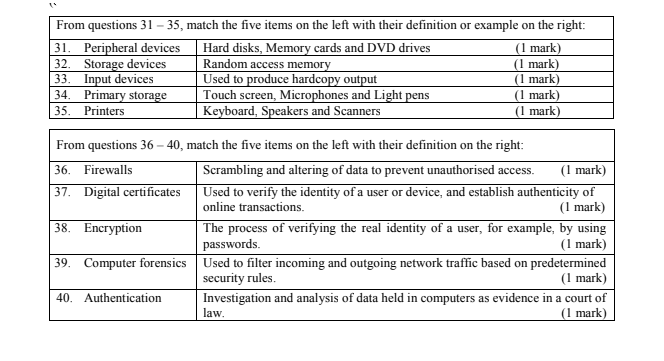
(Total: 40 marks)
SECTION TWO
[40 MARKS] [1 Hour]
You are advised not to exceed forty words in answering each question.
41. Distinguish between the following terminologies:
(a) A Workbook and Worksheet in Microsoft Excel. (2 marks)
(b) Command line interface and Graphical user interface. (2 marks)
(c) Antivirus and Backups (2 marks)
(d) Denial-of-service attacks and Distributed Denial-of-Service attacks. (2 marks)
(e) Personal area network and Wide area network. (2 marks)
42. Identify two benefits of:
(a) Accounting software. (2 marks)
(b) Presentation software (2 marks)
43. Highlight two causes of hardware obsolescence. (2 marks)
44. List two icons found on a Windows desktop. (2 marks)
45. Identify two to factors to consider when selecting a printer. (2 marks)
46. State two options available when aligning text in Microsoft Excel. (2 marks)
47. Explain two factors to consider when selecting an operating system. (2 marks)
48. Highlight two computer application areas. (2 marks)
49. In Word processing software, page orientation can be displayed in two ways. Outline these two ways. (2 marks)
50. Explain two basic features of accounting software. (2 marks)
51. Outline two disadvantages of low-level languages. (2 marks)
52. Explain two ways in which information technology has transformed organisations. (2 marks)
53. Discuss the impact of cyber security education. (2 marks)
54. Describe the role of hyperlinks in Microsoft Word. (2 marks)
55. Explain two ways that can be used to make a Microsoft PowerPoint presentation attractive. (2 marks)
(Total: 40 marks)
SECTION III
[20 MARKS] [20 MINUTES]
56. Create a new blank workbook in Microsoft Excel. Name the workbook Westlands Sales Report. Enter the data as it appears below: (1 mark)
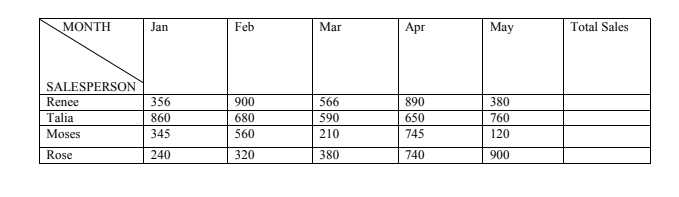
(a) Insert a row before the first row and type WESTLANDS SALES REPORT in cell A1. (2 marks)
(b) Insert a new row between Talia and Moses. In the new row, type in the following: (1 mark)
John 890 211 340 691 720
(c) Calculate the Totals in Column G. (2 marks)
(d) Type the word Minimum in cell I2. Calculate the Minimum Sales. (2 marks)
(e) Type the word Maximum in cell J2. Calculate the Maximum Sales. (2 marks)
(f) Merge and Center cell A1 to J1. (1 mark)
(g) Save the document as Westlands Sales report.
(h) Create a 2-DClustered column chart showing the Total sales for each Sales person. (3 marks)
(i) Edit the Title of the chart to display the data WESTLANDS SALES REPORT. (1 mark)
(j) Insert data labels on the Inside end showing the Total sales for each Sales person. (2 marks)
(k) Move the chart to Sheet 2, pasting it in cell B2. (2 marks)
(l) Rename Sheet 1 as Sales Data and Sheet 2 as Chart. (2 marks)
(Total: 20 marks)
