THURSDAY: 4 August 2022. Afternoon paper. Time Allowed: 2 hours.
This paper has two sections. SECTION I has twenty (20) multiple choice questions. SECTION II has three practical questions of sixty (60) marks. All questions are compulsory. Marks allocated to each question are shown at the end of the question.
SECTION I
1. A software that manages related records is known as___________________________.
A. Word processor
B. Spreadsheet
C. Database Management System
D. SQL (2 marks)
2. The name referring to replacing repeating groups in database design is called?
A. Database design
B. Sorting
C. Normalisation
D. Filtering (2 marks)
3. Which of the following is NOT control measures to database security?
A. Training
B. Password
C. Encryption
D. Access control (2 marks)
4. A column in a table is known as?
A. Query
B. Field
C. Cell
D. Database (2 marks)
5. A database model in which the data are organized into a tree-like structure is called
A. Relational
B. Object oriented
C. Flat file
D. Hierarchical (2 marks)
6. A language in databases used to create, alter and retrieve data is known as?
A. SQL
B. Python
C. Java
D. Visual Basics (2 marks)
7. What is prototyping?
A. Rapid development
B. Creating final database
C. Testing databases
D. Database experimental process (2 marks)
8. Which of the following is a functional requirement?
A. Business rules
B. Security
C. Portability
D. Reliability (2 marks)
9. Which of the following is an advantage of using databases?
A. Provide ready solutions to users
B. Cheap software
C. Eliminates redundancy
D. Data is 100% available (2 marks)
10. A database object that act as a printing template is.
A. Table
B. Form
C. Query
D. Report (2 marks)
11. The command alter is used to?
A. Delete data
B. Change table structure
C. Update data
D. Create table (2 marks)
12. The act of tracing a transaction to a user is known as?
A. Reporting
B. Tracing
C. Observation
D. Audit (2 marks)
13. Instructions or programs in a database are known as?
A. Stored procedures
B. Forms
C. Queries
D. Macros (2 marks)
14. Which of the following is NOT a security threat to databases?
A. Industrial espionage
B. Sabotage
C. Hacking
D. Encryption (2 marks)
15. A database backup that happens when database is NOT in use is known as?
A. Offline backup
B. Online database
C. Hot backup
D. Proper backup (2 marks)
16. Which of the following is NOT a requirement to be applied for a database software?
A. Memory size
B. Speed
C. User language
D. Compatibility (2 marks)
17. Small software installed to update a database software is called?
A. Reconfiguration
B. Patches
C. Drivers
D. Applications (2 marks)
18. A database cycle done during every stage is known as?
A. Development
B. Requirements gathering
C. Investigation
D. Documentation (2 marks)
19. Evaluate the statement “A copy of a database files is known as backups” as True or False.
A) FALSE
B) TRUE (2 marks)
20. Which of the following is a method of data segmentation in a database?
A. Location
B. Application
C. Size
D. Speed (2 marks)
SECTION II
21. Consider the data below
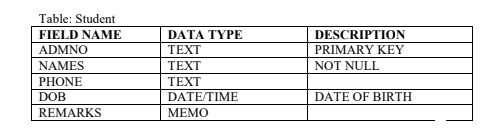
Using a database software create a database called “school” with the table above. (5 marks)
Fill in 5 records of any students. (5 marks)
Prepare a query/view to display all students and all fields (5 marks)
Prepare report showing all the fields. (5 marks)
Capture and upload screenshots/files to demonstrate how you have performed the above task
(Total: 20 marks)
22. Consider the tables below:
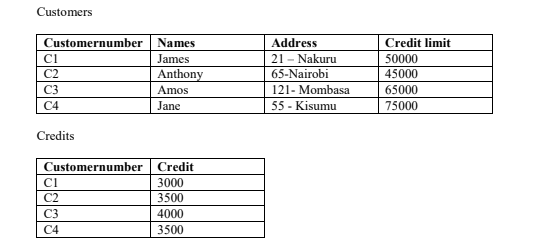
Using MYSQL database create a database called “business” with the above tables. (5 marks)
Input the data into respective tables. (5 marks)
Create and save a view/query that shows all fields from both tables as they relate. (5 marks)
Create and save a view/query that shows fields Customernumber, names and available balance as credit limit less credit. (5 marks)
Capture and upload screenshots/files to demonstrate how you have performed the above task
(Total: 20 marks)
23. Create a backup of both databases in questions 21 and 22 above.
Restore the database “school” as “shule”.
Restore the database “business” as “biashara”.
Secure shule and biashara databases using a password “exam”. (4 marks)
Capture and upload screenshots/files to demonstrate how you have performed the above task
(Total: 20 marks)
