WEDNESDAY: 3 August 2022. Afternoon paper. Time Allowed: 2 hours.
Answer ALL questions. Each question is allocated two (2) marks.
1. Which of the following statements correctly defines cryptography?
A. The process of converting ordinary plain text into unintelligible text and vice-versa
B. The method of storing and transmitting data in a storage device with secret codes
C. The process of backing and storing data in a more secure method
D. The process of storing ordinary plain text without altering it and vice-versa
2. Below is a list of security services of cryptography. Which one is NOT?
A. Confidentiality
B. Repudiation
C. Authentication
D. Integrity
3. Anyone can send an encrypted message to Allan but only Allan can read it. Using PKI, when Kathy wishes to send an encrypted message to Allan, she looks up Allan’s public key in a directory, uses it to encrypt the message, and sends it off. Allan then uses his private key to decrypt the message and read it. No one listening in can decrypt the message. Thus, although many people may know the public key of Allan and use it to verify Allan’s signatures, they cannot discover Allan’s private key and use it to forge digital signatures. This is referred to as the principle of:
A. Symmetry
B. Non-repudiation
C. Irreversibility
D. Asymmetry
4. ______________________is a file or electronic password that proves the authenticity of a device, server, or user through the use of cryptography and the public key infrastructure (PKI).
A. Digital certificate
B. Digital signature
C. Digital code
D. Digital value
5. The following are salient features of cryptosystem based on symmetric key encryption. Which one is NOT?
A. Persons using symmetric key encryption must share a common key prior to exchange of information
B. Keys are recommended not to change regularly to maintain stability of the system
C. Length of key in this encryption is smaller and hence, process of encryption-decryption is faster than asymmetric key encryption
D. Processing power of computer system required to run symmetric algorithm is less
6. Identify the type of attack on cryptography shown by the diagram shown below
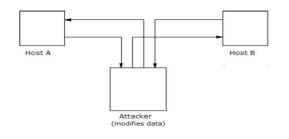
A. Active attacks
B. Passive attacks
C. Public attacks
D. Proprietary attacks
7. Which of the following is NOT a block cipher scheme
A. Digital Encryption Standard
B. Triple DES
C. Unique Encryption Standard
D. IDEA
8. Which of these statements BEST describes stream ciphers as used in cryptography?
A. A scheme where plaintext is processed one bit at a time
B. A scheme where plaintext is processed blocks of bits at a time
C. A scheme where positions held by plaintext are shifted to a regular system.
D. A scheme where positions held by plaintext are shifted to an irregular system
9. ______is a technique for hiding a secret message within a larger one in such a way that others cannot discern the presence or contents of the hidden message.
A. Cryptography
B. Stethonography
C. Decryption
D. Steganography
10. On comparing AES with DES, which of the following functions from DES does not have an equivalent AES function?
A. f function
B. permutation p
C. swapping of halves
D. xor of subkey with function f
11. The statements below are disadvantages of cryptography. Which ONE is NOT?
A. Cryptography does not safeguard against vulnerability and threats that come from poor designs of systems, procedures, and protocols.
B. A strongly authenticated, encrypted, and digitally signed information is difficult to access for a legitimate user at the time of decision-making.
C. Without detecting any suspicious activity, the data cannot be altered in storage or transmitted to the sender and also the receiver.
D. The security of the cryptographic technique is based on the computational difficulty of mathematical problems.
12. Match the following statements with their corresponding terminologies
I. Uses a single key for both encryption and decryption
II. Uses one key for encryption and another for decryption
III. Uses a mathematical transformation to irreversibly “encrypt” information
X. Hash Functions
Y. Public Key Cryptography
Z. Secret Key Cryptography
A. I-Y, II-Z, III-X
B. I-X, II-Z, III-Y
C. I-Y, II-X, III-Z
D. I-Z, II-Y, III-X
13. For messages sent through an insecure channel, a properly implemented digital signature gives the receiver reason to believe the message was sent by the claimed sender. While using a digital signature, the message digest isencrypted with which key?
A. Sender’s private key
B. Receiver’s private key
C. Receiver’s public key
D. Sender’s public key
14. A digital signature works in cryptography by utilising the following components EXCEPT one. Select the ODD one out.
A. Hash
B. Asymmetric encryption
C. Certificate authority
D. Private Key infrastructure
15. Which of the following statements BEST describes adaptive hash functions as used in cryptography?
A. Any algorithm designed to iterate on its inner workings, feeding the output back as input, in a manner that causes it to take longer to execute.
B. An algorithm that uses a cryptographic key and a cryptographic hash function to produce a message authentication code that is keyed and hashed.
C. An algorithm that takes an arbitrary amount of data input and produces a fixed-size output of enciphered text
D. Any algorithm designed to add random data to each plaintext credential in a manner that causes it to take longer to execute
16. Blockchain applications make use of cryptography techniques in the following ways EXCEPT one. Select the ODD one out.
A. Digital signatures to sign transactions.
B. Digital rapid delivery of transactions.
C. Hashing to create a unique identity string for each block
D. Creating consensus algorithms
17. Give the four major types of tokens used in cryptocurrency.
A. Utility, Payment, Security, Digital coins
B. Payment, Security, Digital coins, Altcoins
C. Utility, Payment, Security, Exchange
D. Integrity, Utility, Security Altcoins
18. Which of the following statements BEST describes public key encryption?
A. The type of cryptography that involves a private key which are associated with an entity that needs to authenticate its identity electronically
B. The type of cryptography that involves a pair of keys known as a public key and a private key which are associated with an entity that needs to authenticate its identity electronically
C. The type of cryptography that does not involve a pair of keys known as a public key and a private key which are associated with an entity that needs to authenticate its identity electronically
D. The type of cryptography that involves a public key which is associated with an entity that needs to authenticate its identity electronically
19. For the cipher text 0000 0111 0011 1000 and Key 0110 1111 0110 1011, apply the Simplified AES to obtain the
plaintext. The plain text is
A. 0110 1001 0111 0001
B. 0110 1111 0110 1011
C. 0010 1001 0110 1011
D. 1111 0101 0111 1111
20. ____________ can be considered a field of study, which encompasses many techniques and technologies, whereas _____________is more of mathematical and algorithmic in nature.
A. Encryption, cryptography
B. Cryptography, encryption
C. Cryptocurrency, encryption
D. Encryption, cryptocurrency
21. Use Caesar’s Cipher (C =(p+3) to decipher the following HQFUBSWHG WHAW
A. ABANDONED LOCK
B. ENCRYPTED TEXT
C. ABANDONED TEXT
D. ENCRYPTED LOCK
22. A building block of encryption techniques in which the letters of plaintext are replaced by other letters or by numbers or symbols is known as?
A. Transposition technique
B. Substitution technique
C. Subscription technique
D. Unique key
23. What is the name given to the encryption technique where characters present in the original message are replaced by the other characters or numbers or by symbols?
A. Transposition
B. Mirroring
C. Imaging
D. Substitution
24. Which of the following is a disadvantage of Steganography?
A. Once the system is discovered, it becomes worthy
B. It requires a lot of overhead to hide relatively few bits of information
C. A message can be first hidden then encrypted
D. It requires minimal overhead to hide relatively few bits of information
25. A _____ refers to the number of bitcoins you get if you successfully mine a block of the currency
A. Block dividends
B. Block Deal
C. Block reward
D. Block Profit
26. Which of the following slows the cryptographic algorithm
1) Increase in Number of rounds
2) Decrease in Block size
3) Decrease in Key Size
4) Increase in Sub key Generation
A. 1 and 3
B. 2 and 3
C. 3 and 4
D. 2 and 4
27. Identify the type of fork shown by the diagram below.
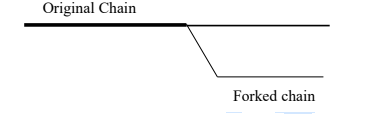
A. Soft fork
B. Hard fork
C. Ethereum fork
D. older fork
28. A______ is a device, physical medium, program or a service which stores the public or private keys for cryptocurrency transactions
A. Coinbase
B. Crypto safe
C. Wallet
D. Altcoin
29. Match each of the terms on the left with their corresponding statements on the right
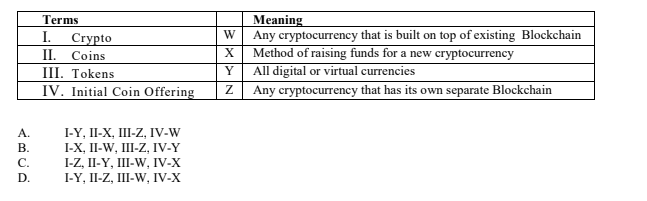
30. Organisations that have successfully implemented digital asset management systems cite all of the following as being essential EXCEPT?
A. Web content management and enterprise content management systems
B. Enterprise collaboration tools
C. Business analytics tools and dashboards
D. Enterprise search software
31. Select from the list below the ONE which is not a type of transposition cipher.
A. Rail fence cipher
B. Pad cipher
C. Columnar transposition cipher
D. Route cipher
32. Which of the following is a characteristic of public key infrastructure (PKI)?
A. Public-key cryptosystems do not require a secure key distribution channel
B. Public-key cryptosystems do not provide technical nonrepudiation via digital signatures
C. Public-key cryptosystems distribute public-keys within digital signatures
D. Public-key cryptosystems are faster than symmetric-key cryptosystems
33. Select the statement that correctly defines poly alphabetic cipher.
A. A substitution-based cipher which uses multiple substitution at different positions
B. A substitution-based cipher which uses fixed substitution over entire message
C. A transposition-based cipher which uses multiple substitution at different positions
D. A transposition-based cipher which uses fixed substitution over entire message
34. In ___________________ cipher the plain text and the ciphered text does not have a same number of letters?
A. Affine cipher
B. Vigenere cipher
C. Volumnar cipher
D. Additive cipher
35. Which of the following techniques can be used for security of data?
A. Authorisation
B. Authentication
C. Encryption
D. Permission
36. Hassan recently received an electronic mail message from Amina. What cryptographic goal would need to be met to convince Hassan that Amina was actually the sender of the message?
A. Nonrepudiation
B. Confidentiality
C. Uniqueness
D. Digital signature
37. Salim and Tom wish to communicate using symmetric cryptography but do not have a prearranged secret key. What algorithm might they use to resolve this situation?
A. DES
B. AES
C. Skipjack
D. Diffie-Hellman
38. The following are kinds of threats that exist for a cryptographic system. Which one is NOT?
A. Mutating plaintext attack
B. Ciphertext-only attack
C. Known-plaintext attack
D. Chosen-plaintext attack
39. The list below is of specific components of the Public Key Infrastructure EXECPT_____
A. Certificate Authority
B. Revenue Authority
C. Digital Certificate
D. Registration Authority
40. _____________________cryptographic primitives are defined to be secure in one of several different security models against adversaries with different capabilities.
A. Privacy protocols
B. Integrity preserving
C. Privacy preserving
D. Wallets
41. Data encryption standard is a block cipher and encrypts data in blocks of size of _________________________ each.
A. 16 bits
B. 64 bits
C. 32 bits
D. 128 bits
42. Public key encryption is advantageous over Symmetric key Cryptography because of ____
A. Speed
B. Space
C. Key length
D. Key exchange
43. __________________________ was designed to replace the original Data Encryption Standard (DES) algorithm, which hackers eventually learned to defeat with relative ease
A. AES
B. Triple DES
C. RSA
D. Blowfish
44. What does one need to verify a digital signature?
A. Sender’s Private key
B. Sender’s Public key
C. Receiver’s Private key
D. Receiver’s Public key
45. Chosen cipher text attack is based on___________________
A. Encryption
B. Cryptography
C. Cryptanalysis
D. Decryption
46. Select the principal that ensures only the sender and the intended recipients have access to the contents of message
A. Confidentiality
B. Authentication
C. Integrity
D. Access control
47. An attacker has captured a target file that is encrypted with public key cryptography. Which of the attacks below is likely to be used to crack the target file?
A. Chosen plain-text attack
B. Timing attack
C. Memory trade-off attack
D. Replay attack
48. In Digital Signature, there is ___________________ relationship between signature and message
A. Many to one
B. One to many
C. Many to many
D. One to one
49. In one of the attacks below, an attacker obtains ciphertexts encrypted under two different keys and gathers plaintext and matching ciphertext. Which one?
A. Ciphertext-only attack
B. Chosen-plaintext attack
C. Related-key attack
D. Adaptive chosen-plaintext attack
50. Encryption Strength is based on ALL of the following EXCEPT?
A. Strength of Algorithm
B. Knowledge of the user.
C. Secrecy of key
D. Length of key
