THURSDAY: 4 August 2022. Morning paper. Time Allowed: 2 hours.
This paper has two sections. SECTION I has twenty (20) multiple choice questions. SECTION II has three practical questions of sixty (60) marks. All questions are compulsory. Marks allocated to each question are shown at the end of the question.
SECTION I
1. Internetworking ensures data communication among networks owned and operated by different entities using the same protocol stack or communication methodologies. What is the name given to the device that performs the function of determining the path that messages should take through internetworks?
A. Router
B. Switch
C. Hub
D. Bridge (2 marks)
2. What network will IP address 172.16.10.50 belong to if the subnet mask is 255.255.255.252
A. 172.16.10.32
B. 172.16.10.48
C. 172.16.10.49
D. 172.16.10.52 (2 marks)
3. What is the name given to a mechanism of combining several class-C address ranges into a single network or route?
A. Classless Inter-domain Routing (CIDR)
B. Classful Addressing
C. IP Range
D. Subnet mask (2 marks)
4. Ms. Mahmud a newly hired network technician is investigating network connectivity from a host in Finance department to remote host in Procurement department with the unicast address 192.168.10.8. Which command, when issued on a PC, will display the path to the remote host?
A. Ping
B. Tracert
C. Netstat
D. Nbstat (2 marks)
5. A network Technician was using his computer to open a YouTube video using a web browser. From the perspective of Mr. Kazembe what would be the correct order of the protocol stack that is used to prepare the request for transmission.
A. HTTP, UDP, IP, Ethernet
B. HTTP,TCP,IP,Ethernet
C. HTTP,IP,UDP,Ethernet
D. HTTP,IP,TCP,Ethernet (2 marks)
6. A small branch office in your neighborhood has been established with ONLY two computers. What type of cable should be used to connect the two computers?
A. Rolled Cable
B. Straight-through cable
C. Crossover Cable
D. Ethernet Cable (2 marks)
7. Which command utility is used to display protocol statistics of Transport layer Protocol?
A. Netstat –s
B. Netstat –r
C. Netstat –e
D. Netstat –n (2 marks)
8. A loopback address is a type of IP address that is used to test the communication or transportation medium on a local network card for testing network applications. Which IPv4 address can be used by End User Device to ping a loopback address?
A. 192.168.0.1
B. 127.0.0.1
C. 169.254.0.1
D. 224.0.0.9 (2 marks)
9. An attempt by attacker to take control of computer system, programs and network communication can be defined as what.
A. Threats
B. Session hijacking
C. Cyber hijacking
D. Cyber Attacks (2 marks)
10. What is the term that relates to weakness exhibited in system or network?
A. Threat
B. Vulnerability
C. Attack
D. Exploit (2 marks)
11. Which one of the following is a program designed to help users computer detect virus and avoid them
A. Antivirus
B. Spyware
C. Adware
D. Malware (2 marks)
12. Which of the following adheres to the principle of keeping sensitive information highly classified.
A. Confidentiality
B. Availability
C. Integrity
D. Maintainability (2 marks)
13. Wi-Fi is a wireless network technology that sends data through the internet and on to non-wired computers. Which of the following can be used by threat actor to undertake Wi-Fi hacking.
A. Mininet wifi
B. Wireshark
C. Nmap
D. Aircrack-ng (2 marks)
14. Miss Tumbili turned on her tablet and got a message displaying a message indicating that all of her files have been locked. In order to get the files unencrypted, he is supposed to send an email and include a specific ID in the email title. The message also includes ways to use block-chain as payment for the file decryption. After inspecting the message, the network analyst suspects a security breach occurred. What type of malware could be responsible?
A. Trojan horse
B. Adware
C. Ransomware
D. Spyware (2 marks)
15. Which one of the following extends a private network across a public network and enables users to send and receive secure data across shared or public networks
A. Kibana
B. Wireshark
C. Generic Encapsulation Protocol
D. Virtual Private Network (2 marks)
16. What is the name given to a communications standard designed to send packets across the internet and ensure the successful delivery of data and messages over networks?
A. Transmission Control Protocol (TCP)
B. User Datagram Protocol
C. Simple Mail Transfer Protocol
D. Network Time Protocol (2 marks)
17. Which of the following is an integration of two or more different topologies to form a resultant topology.
A. Hybrid topology
B. Star topology
C. Bus topology
D. Mesh topology
18. What one of the following is the procedure that connects an ever-changing Internet Protocol (IP) address to a fixed physical machine address?
A. Internet control Message Protocol (ICMP)
B. Getmac
C. DNS
D. Address Resolution Protocol (ARP) (2 marks)
19. What is the name given to a method used to automatically configure IPv6 host addresses using MAC address of a host device to generate a unique 64-bit interface ID?
A. Link Local
B. Global Unicast
C. Extended Unique Identifier
D. Unique local (2 marks)
20. Which of the following displays the name of a given network in the list of available networks when nearby users try to connect their wireless devices.
A. Basic service set identifier (BSSID)
B. Service Set Identifier(SSID)
C. Wireless Access Point(WAP)
D. Wired Equivalent Privacy (WEP) (2 marks)
SECTION II
21. Use Wireshark as a network monitoring tool to communicate and examine DNS server.
Required resources
• Wireshark Protocol analyzer
• Internet connection
• Windows or Linux PC
Open Wireshark and test connectivity to www.google.com in order to examine UDP packets generated when communicating with DNS server. Examine fields in the DNS query packet and answer the following questions:
Capture a screenshot in wireshark showing Filtered DNS (4 marks)
Display source IP and Mac address (4 marks)
Display destination IP and Mac address (4 marks)
Display source port number (4 marks)
Display destination port number (4 marks)
Upload screenshots/files to demonstrate how you have performed the above task.
(Total: 20 marks)
22. Relaunch Wireshark and connect to your to www.gmail.com account through the browser in order to examine HTTPs traffic.
Capture a screenshot of wireshark showing HTTPS traffic filtered via port 443 (6 marks)
Display source and destination IP addresses (4 marks)
Display source and destination application layer protocol numbers (4 marks)
Display encrypted application data from secure socket layer (6 marks)
Upload screenshots/files to demonstrate how you have performed the above task.
(Total: 20 marks)
23. Using appropriate network simulator (GNS3), configure the topology as shown below:
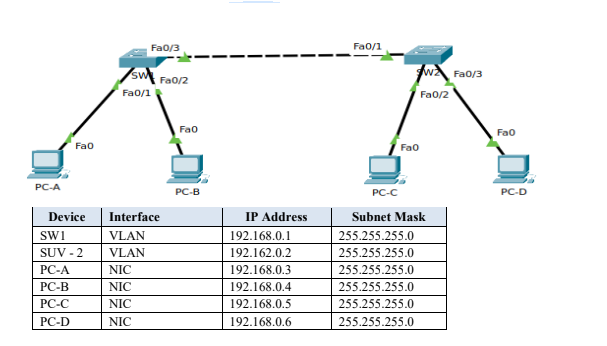
Configure IP Address as shown in the topology. (4 marks)
Capture a screenshot displaying Layer I and Layer II status from SW1. (4 marks)
Capture screen showing connectivity between PC-A and PC-B. (2 marks)
Capture screen showing connectivity between PC-C and PC-D. (2 marks)
From PC-A use appropriate command utility to trace the path to PC-B. (2 marks)
From PC-B test connectivity to SW1. (2 marks)
Capture a screenshot displaying the physical layer of PC-C. (4 marks)
Upload screenshots/files to demonstrate how you have performed the above task.
(Total: 20 marks)
