 UNIVERSITY EXAMINATIONS: 2013/2014
UNIVERSITY EXAMINATIONS: 2013/2014
ORDINARY EXAMINATION FOR THE BACHELOR OF SCIENCE
IN INFORMATION TECHNOLOGY
BIT 2104 DATABASE DESIGN AND DEVELOPMENT
DATE: AUGUST, 2014 TIME: 2 HOURS
INSTRUCTIONS: Answer Question ONE and any other TWO
QUESTION ONE [30 MARKS]
i). A research organization is in the process of developing an application that keeps
information about studies done over a period of time. In this proposed system there
are several data collection tools e.g. questionnaire, interview e.t.c. Each tool can be
administered to several respondents but a respondent will only be given one tool.
Each tool consists of several questions of different types but a given question belongs
to one and only one tool. As a result there are several responses for the same question
but only one response from the same respondent for a particular question. The study
is described by studyId, sample_size and area of study. The research tool is described
by toolID and tool name. The respondent is described by respondent ID, gender and
age. The questions are described by question id and description. Finally, the response
is described by response Id and details.
Required: Produce a logical data model for this case using chen’s notation.
[9 Marks]
ii). Differentiate between a distributed database (DDB) and a distributed database
management system (DDBMS).
[4 Marks]
iii). Differentiate between horizontal and vertical fragmentation as used in a distributed
database
[4 Marks]
iv). Define object as used in object oriented database systems.
[2 Marks]
v). State any three characteristics of objects in an object oriented database.
[3 Marks]
vi). Define mobile database and give any applications of mobile databases.
[4 Marks]
vii). Data management is a discipline that focuses on proper generation, storage and
retrieval of data. Outline any four data management issues.
[4 Marks]
QUESTION TWO [20 MARKS]
a) A database design and development team for a hospital patient system have identified
two important entity types and during their modeling they have come up with the
schema below:
PATIENT->(PatientID, PatientName, PatientGender,PatientAge)
DOCTOR->(DoctorID, DoctorName, Department)
You been tasked with the responsibility of normalizing this design to third normal
form and producing a logical data model using crow’s foot notation. [10 Marks]
b) Describe any three functions of a database administrator (DBA).
[6 Marks]
c) End users are people whose jobs require access to the database for querying, updating
and generating reports. The database basically exists because of the end user.
Describe four types of end users highlighting main activities for each.
[4 Marks ]
QUESTION THREE [20 MARKS]
a) Describe three advantages and three disadvantages of object oriented database
management systems (ODBMS). [6 Marks]
b) Discuss any four structural components of a database management system (DBMS).
[8 Marks]
c) Describe the term database replication and state its importance.
[6 Marks]
QUESTION FOUR [20 MARKS]
a) Discuss three main types of actions involving a database. [9 Marks]
b) Outline any four applications of advanced databases. [4 Marks]
c) Explain the difference between object oriented data model(OODM) and object
oriented database (OODB). [3 Marks]
d) When developing a database application, developers are required to develop
application that can access and used the database. Consequently, coding is required.
Discuss any four best practices followed when coding a database application.
[4 Marks]
QUESTION FIVE [20 MARKS]
a) Describe the difference between a database state and database schema.
[4 Marks]
b) Database tuning is the process of modifying the actual database which encompasses
the allocated memory, disk usage, CPU, I/O and underlying database processes as
well as modification of database architecture to optimize the use of the hardware
resources available. In this regard discuss three advantages of database tuning.
[6 Marks]
c) Database security refers to the process of protecting the database against unauthorized
access to or modification of the database, denial of service to authorized users and
provision of service to authorized users. Any security measure must address three key
characteristics. Discuss these characteristics. [6 Marks]
d) Use the table below to answer the questions that follow.
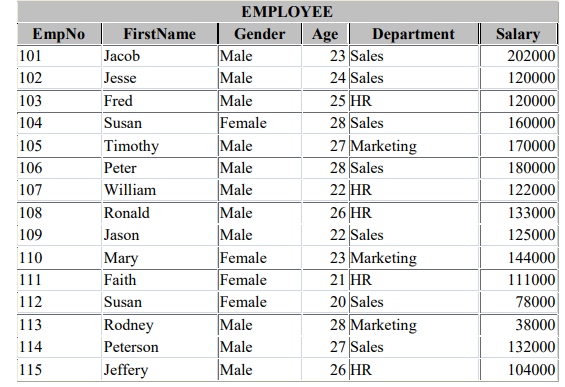
Write DML statements for each of the following tasks.
i). Display female employees who do not work in sales department.
[2 Marks]
ii). Compute the total salary paid to each department displayed as PAY.
[2 Marks]
