
UNIVERSITY EXAMINATIONS: 2017/2018
ORDINARY EXAMINATION FOR THE BACHELOR OF SCIENCE IN
APPLIED COMPUTING
BAC3306 NETWORK SECURITY
FULLTIME/PARTTIME
DATE: APRIL 2018 TIME: 2 HOURS
INSTRUCTIONS: Answer Question ONE and any other TWO
QUESTION ONE
a) A security administrator is looking to set up a secure network. To this end, he wants to
deploy both an IDS and a Firewall. He is considering the following deployment scheme:
Deploy the IDS behind the edge of the Firewall
Deploy the IDS in-front of the edge Firewall
i. Name Five pros and cons of both deployment schemes [5 Marks]
ii. It is said that IDS majorly detect intrusions. How then is it useful in securing networks if
it cannot prevent intrusion? Discuss. [4 Marks]
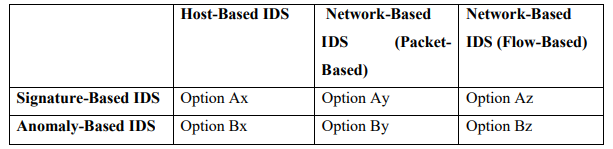
iii. For each of the SIX options shown in the table below, give one example of attack that can
be detected with the considered type of IDS. For each attack, briefly explain how and/or
why. [6 Marks]
b) Explain OSI architecture for security [2 Marks]
c) What are the different types of security services [2 Marks]
d) Briefly define categories of security mechanisms [2 Marks]
e) Difference between block cipher and stream cipher [2 Marks]
f) Explain any substitution techniques for cryptography [2 Marks]
g) Describe Differential Cryptanalysis and Linear Cryptanalysis for DES [5 Marks]
QUESTION TWO
a) The Data Link Layer in the OSI model is concerned with the logical elements of
transmissions between two directly connected stations. It deals with issues of local
topology where many stations may share a common local media. This is the layer where
data packets are prepared for transmission by the physical layer. The Data Link Layer has
been a long-neglected area of study for information security, lost between the physical
issues of layer one and the dominating realm of the firewall in layers three and four.
i. Discuss the common vulnerabilities posed on a network at this level [5 Marks]
ii. Describe different types of firewall [5 Marks]
b) Define e-mail security [2 Marks]
c) Briefly explain different protocols for e-mail security. [2 Marks]
d) Describe the use SMIME [2 Marks]
e) What are web security threats [2 Marks]
f) Give countermeasures of web security threats [2 Marks]
QUESTION THREE
Authentication can be accomplished in many ways. The importance of selecting an environment
appropriate Authentication Method is perhaps the most crucial decision in designing secure
network system.
a) Define Authentication with relation to network security systems [2 Mark]
b) Describe the processes involved in the following authentication techniques:
i. Digital Signatures [2 Marks]
ii. Secure Sockets Layer [2 Marks]
iii. Secure Shell [SSH] [2 Marks]
iv. IP-SEC [2 Marks]
v. Kerberos [2 Marks]
c) User authentication can be handled using one or more different authentication methods.
Some authentication methods such as plain password authentication is easily
implemented but are in general weak and primitive.
i. State two types of password authentication [2 Marks]
ii. Outline TWO weaknesses exhibited by passwords [2 Marks]
d) Briefly outline the problems and challenges faced in implementing network security by
intrusion detection [4 Marks]
QUESTION FOUR
All information systems create risks to an organization, and whether the level of risk introduced
is acceptable is ultimately a business decision. What constitutes an acceptable level of risk
depends on the individual organization and its ability to tolerate risk. An organization that is risk
averse will ultimately accept lower levels of risk and require more security controls in deployed
systems.
a) List FIVE risks associated to network system security [5 Marks]
b) Elaborate how you can mitigate the above (a) named risks [5 Marks]
c) Explain FIVE key considerations when engaging in network security strategy
[5 Marks]
d) Briefly discuss the demerits of wireless networks with regards to security. [5 Marks]
QUESTION FIVE
a) The objective of an ideal IDS is to give a notification of a successful attack in progress;
with 100% accuracy, promptly, with complete diagnosis and recommendations.
Unfortunately, this does NOT exist. Discuss using relevant examples. [5 Marks]
b) Outline FIVE pros and Cons of an IDS as a network security [5 Marks]
c) Describe the working of Public Keys with relation to authentication [5 Marks]
d) What is a Certificate in relation to security [1 Mark]
e) Describe the contents of a Certificate [4 Marks]
